Use the SSO management features in Control Hub for certificate management and general SSO maintenance activities, such as updating an expiring certificate or checking on your existing SSO configuration. Each SSO management feature is covered in the individual tabs in this article.
If you want to set up SSO for multiple identity providers in your organization, refer to SSO with multiple IdPs in Webex.
If your organization's certificate usage is set to None but you're still receiving an alert, we recommend that you still proceed with the upgrade. Your SSO deployment is not using the certificate today but you may need the certificate for future changes. |
From time to time, you may receive an email notification or see an alert in Control Hub that the Webex single sign-on (SSO) certificate is going to expire. Follow the process in this article to retrieve the SSO cloud certificate metadata from us (the SP) and add it back to your IdP; otherwise, users won't be able to use Webex services. |
If you’re using the SAML Cisco (SP) SSO Certificate in your Webex organization, you must plan to update the cloud certificate during a regular scheduled maintenance window as soon as possible.
All services that are part of your Webex organization subscription are affected, including but not limited to:
-
Webex App (new sign-ins for all platforms: desktop, mobile, and web)
-
Webex services in Control Hub, including Calling
-
Webex Meetings sites managed through Control Hub
-
Cisco Jabber if it's integrated with SSO
Before you begin
Please read all directions before beginning. After you change the certificate or going through the wizard to update the certificate, new users may not be able to sign in successfully. |
If your IdP doesn’t support multiple certificates (most IdPs in the market don’t support this feature), we recommend that you schedule this upgrade during a maintenance window where Webex App users aren’t affected. These upgrade tasks should take approximately 30 minutes in operational time and postevent validation.
| 1 |
To check if the SAML Cisco (SP) SSO certificate is going to expire:
You can go directly into the SSO wizard to update the certificate, too. If you decide to exit the wizard before you complete it, you can access it again any time from in https://admin.webex.com. | ||
| 2 |
Go to the IdP and click | ||
| 3 |
Click Review certificates and expiry date. This take you to the Service Provider (SP) certificates
window.
| ||
| 4 |
Click Renew certificate. | ||
| 5 |
Choose the certificate type for the renewal:
| ||
| 6 |
Click Download Metadata File to download a copy of the updated metadata with the new certificate from the Webex cloud. Keep this screen open. | ||
| 7 |
Navigate to your IdP management interface to upload the new Webex metadata file.
| ||
| 8 |
Return to the tab where you signed in to Control Hub and click Next. | ||
| 9 |
Click Test SSO Update to confirm that the new metadata file was uploaded and interpreted correctly by your IdP. Confirm the expected results in the pop-up window, and if the test was successful, click Switch to new metadata.
Result: You're finished and your organization's SAML Cisco (SP) SSO Certificate is now renewed. You can check the certificate status at any time under the Identity provider tab.
|
From time to time, you may receive an email notification or see an alert in Control Hub that the IdP certificate is going to expire. Because IdP vendors have their own specific documentation for certificate renewal, we cover what's required in Control Hub, along with generic steps to retrieve updated IdP metadata and upload it to Control Hub to renew the certificate. |
| 1 |
To check if the IdP SAML certificate is going to expire:
| ||
| 2 |
Navigate to your IdP management interface to retrieve the new metadata file.
| ||
| 3 |
Return to the Identity provider tab. | ||
| 4 |
Go to the IdP, click | ||
| 5 |
Drag and drop your IdP metadata file into the window or click Choose a file and upload it that way. | ||
| 6 |
Choose Less secure (self-signed) or More secure (signed by a public CA), depending on how your IdP metadata is signed. | ||
| 7 |
Click Test SSO Update to confirm that the new metadata file was uploaded and interpreted correctly to your Control Hub organization. Confirm the expected results in the pop-up window, and if the test was successful, select Successful test: Activate SSO and the IdP and click Save.
Result: You're finished and your organization's IdP certificate is now renewed. You can check the certificate status at any time under the Identity provider tab.
|
You can export the latest Webex SP metadata whenever you need to add it back to your IdP. You'll see a notice when the imported IdP SAML metadata is going to expire or has expired.
This step is useful in common IdP SAML certificate management scenarios, such as IdPs that support multiple certificates where export was not done earlier, if the metadata was not imported into the IdP because an IdP admin wasn't available, or if your IdP supports the ability to update only the certificate. This option can help minimize the change by only updating the certificate in your SSO configuration and post-event validation.
| 1 |
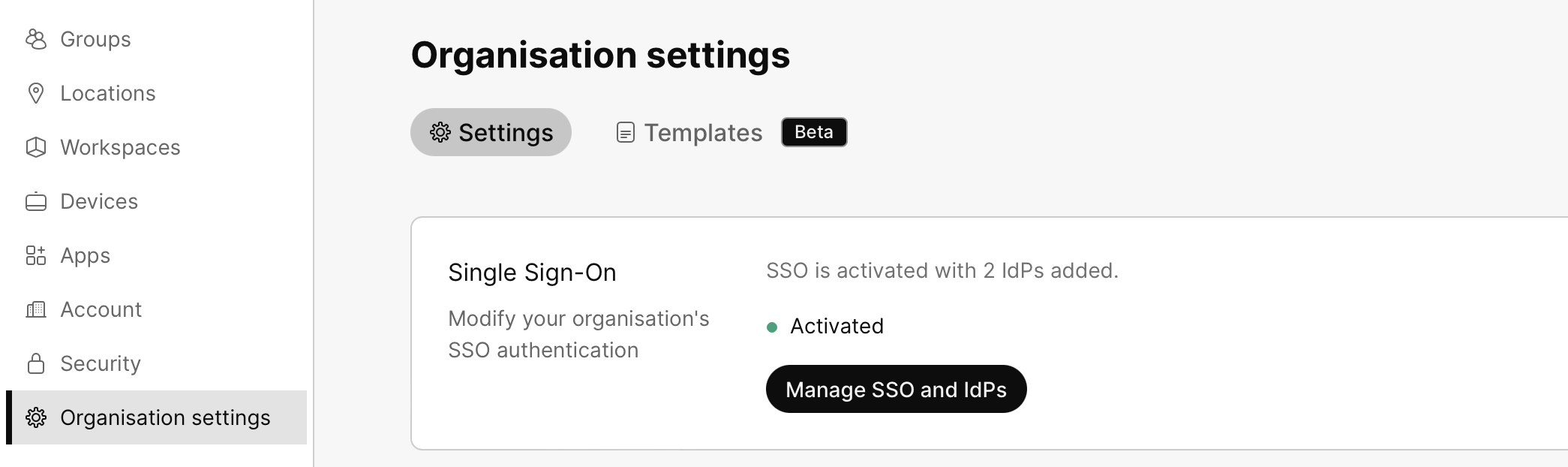
From the customer view in https://admin.webex.com, go to , scroll to Authentication and click Manage SSO and IdPs. |
| 2 |
Go to the Identity provider tab. |
| 3 |
Go to the IdP, click The Webex App metadata filename is idb-meta-<org-ID>-SP.xml. |
| 4 |
Import the metadata into your IdP. Follow the documentation for your IdP to import the Webex SP metadata. You can use our IdP integration guides or consult the documentation for your specific IdP if not listed. |
| 5 |
When you're finished, run the SSO test using the steps in |
When your IdP environment changes or if your IdP certificate is going to expire, you can import the updated metadata into Webex at any time.
Before you begin
Gather your IdP metadata, typically as an exported xml file.
| 1 |
From the customer view in https://admin.webex.com, go to , scroll to Authentication and click Manage SSO and IdPs. |
| 2 |
Go to the Identity provider tab. |
| 3 |
Go to the IdP, click |
| 4 |
Drag and drop your IdP metadata file into the window or click Choose a metadata file and upload it that way. |
| 5 |
Choose Less secure (self-signed) or More secure (signed by a public CA), depending on how your IdP metadata is signed. |
| 6 |
Click Test SSO setup, and when a new browser tab opens, authenticate with the IdP by signing in. |
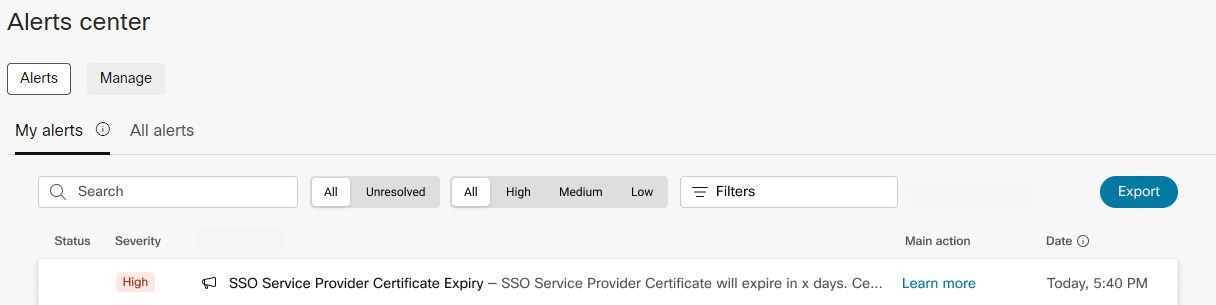
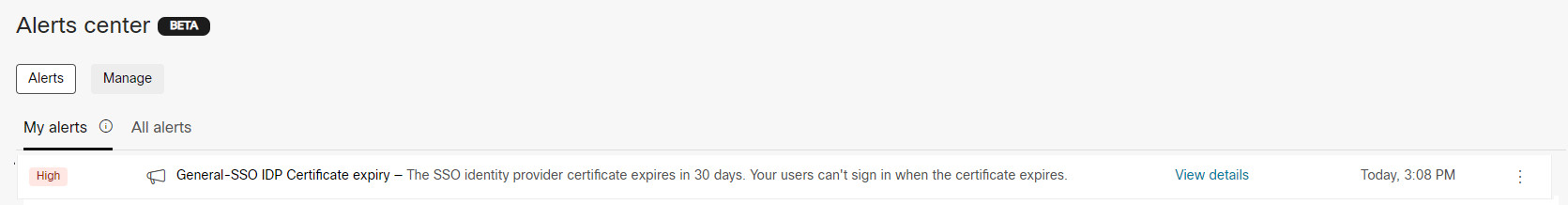
You'll receive alerts in Control Hub before certificates are set to expire, but you can also proactively set up alert rules. These rules let you know in advance that your SP or IdP certificates are going to expire. We can send these to you through email, a space in the Webex App, or both.
Regardless of the delivery channel configured, all alerts always appear in Control Hub. See Alerts center in Control Hub for more information. |
| 1 |
From the customer view in https://admin.webex.com, go to Alerts center. | ||
| 2 |
Choose Manage then All rules. | ||
| 3 |
From the Rules list, choose any of the SSO rules that you'd like to create:
| ||
| 4 |
In the Delivery channel section, check the box for Email, Webex space, or both. If you choose Email, enter the email address that should receive the notification.
| ||
| 5 |
Save your changes. |
What to do next
We send certificate expiry alerts once every 15 days, starting 60 days before expiry. (You can expect alerts on day 60, 45, 30, and 15.) Alerts stop when you renew the certificate.
You may see a notice that the single logout URL isn’t configured:
We recommend that you configure your IdP to support Single Log Out (also known as SLO). Webex supports both the redirect and post methods, available in our metadata that is downloaded from Control Hub. Not all IdPs support SLO; please contact your IdP team for assistance. Sometimes, for the major IdP vendors like AzureAD, Ping Federate, ForgeRock, and Oracle, that do support SLO, we document how to configure the integration. Consult your Identity & Security team on the specifics of your IDP and how to configure it properly. |
If single logout url isn’t configured:
-
An existing IdP Session remains valid. The next time users sign in, they may not be asked to reauthenticate by the IdP.
-
We display a warning message on sign out, so Webex App logout doesn't happen seamlessly.
You can disable single sign-on (SSO) for your Webex organization managed in Control Hub. You may want to disable SSO if you're changing identity providers (IdPs).
If single sign-on has been enabled for your organization but is failing, you can engage your Cisco partner who can access your Webex organization to disable it for you. |
| 1 |
From the customer view in https://admin.webex.com, go to , scroll to Authentication and click Manage SSO and IdPs. |
| 2 |
Go to the Identity provider tab. |
| 3 |
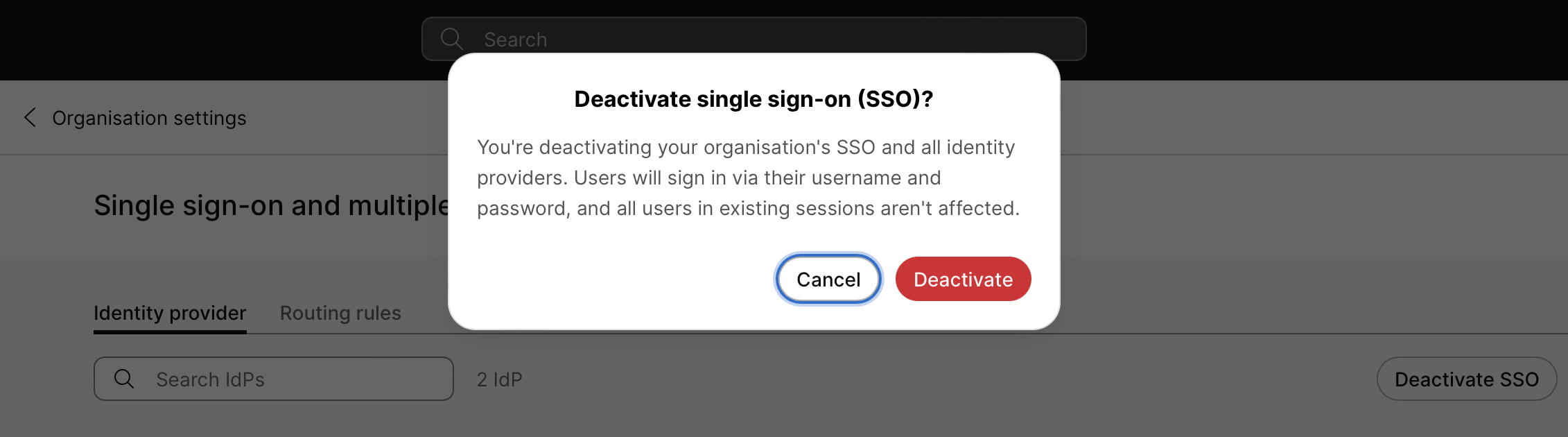
Click Deactivate SSO. A popup window appears that warns you about disabling SSO:
If you disable SSO, passwords are managed by the cloud instead of your integrated IdP configuration. |
| 4 |
If you understand the impact of disabling SSO and want to proceed, click Deactivate. SSO is deactivated and all SAML certificate listings are removed. If SSO is disabled, users who have to authenticate will see a password entry field during the sign-in process.
|
What to do next
If you or the customer reconfigure SSO for the customer organization, user accounts go back to using the password policy that is set by the IdP that is integrated with the Webex organization.
If you run into problems with your SSO login, you can use the SSO self recovery option to get access to your Webex organization managed in Control Hub. The self recovery option allows you to update or disable SSO in Control Hub.
 .
.
 and select
and select