- Home
- /
- Article

Install Webex App with Microsoft Intune to managed devices
 In this article
In this article Feedback?
Feedback?As an administrator, you can use the Webex integration with Intune to provision and manage Webex App from the Microsoft Intune Endpoint Manager.
Overview
Webex supports integration with Enterprise Mobility Management (EMM) such as Microsoft Intune, a cloud-based service that provides both Mobile Application Management (MAM) and Mobile Device Management (MDM) capabilities.
MAM software allows you to provision, configure and control access to mobile applications deployed in your organization. MDM software allows administrators to monitor, manage and secure corporate mobile devices used in your organization. Webex can be enrolled and managed on personal devices and corporate phones using MAM and MDM applications.
Deployment options
Webex for Intune—Using the Intune SDK, we developed Webex for Intune, which is available from the App Store and Google Play.
The Webex for Intune application ID is ee0f8f6b-011c-4d44-9cac-bb042de0ab18.
Webex Intune Intune allows for the enforcement of app policies, such as on-demand VPN and use of work email. Users download Webex Intune, and then the Intune application protection policy controls their access to Webex Intune app and sharing of corporate data.
Device enrollment is optional if you want to deploy Webex Intune; it can be used on managed and unmanaged devices.
EMM with Mobile Device Management—All mobile devices and corporate applications are enrolled in, and managed by, the MDM application.
In this deployment model, the administrator adds the Webex Intune application to the Intune app catalog and assigns it to users or devices (see Add Webex for Android and Add Webex for iOS in this article). The Intune app protection policy applies at the device or profile level. This policy defines a set of rules to control access to Webex Intune and sharing of corporate data.
You can also configure device restrictions to control data sharing from iOS devices.
See Create an application protection policy in this article.
EMM with Mobile Application Management—In this deployment model, the mobile devices are not enrolled in the Intune portal.
-
Users can download the Webex Intune app directly from App Store for iOS devices and Google Play for Android devices. The app protection policy applies at the application level. The policy controls application access requirements, like PIN for access, and controls data sharing from Webex Intune.
-
Another option is to use an app wrapping tool to wrap Webex App. The wrapped application files allow a MAM application to control how apps can be used on a mobile device. Users can download the wrapped and MAM managed version of Webex App from the enterprise's own app store or MAM app repository. The application protection policy controls the sharing of corporate data from the wrapped application.
See Create an application protection policy in this article.
Wrapped versions of Webex apps (.IPA files for iOS, and .APK files for Android) are available from the mobile application management program.
Things to keep in mind
-
Ensure that you have Microsoft Endpoint Manager admin center access.
-
User must have a Webex account.
-
Ensure that users are created in your Active Directory and that users have been assigned Intune licenses.
-
If Android devices are enrolled, ensure that they are enrolled in Intune with a Work profile and that they are compliant with your organization's compliance policy.
Add Webex for Android
| 1 |
Sign in to Microsoft Endpoint Manager Admin Center. |
| 2 |
In the left pane, select Apps, and under Platform choose Android. |
| 3 |
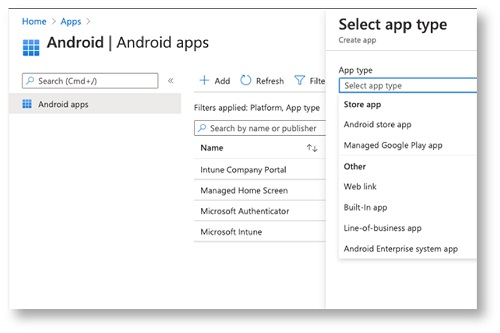
Click Add.
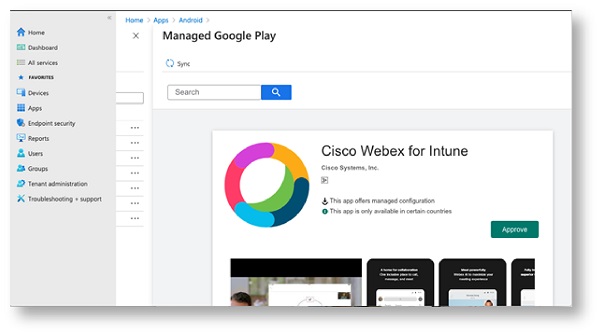
Webex for Intune can be deployed from the Store app in two ways:
|
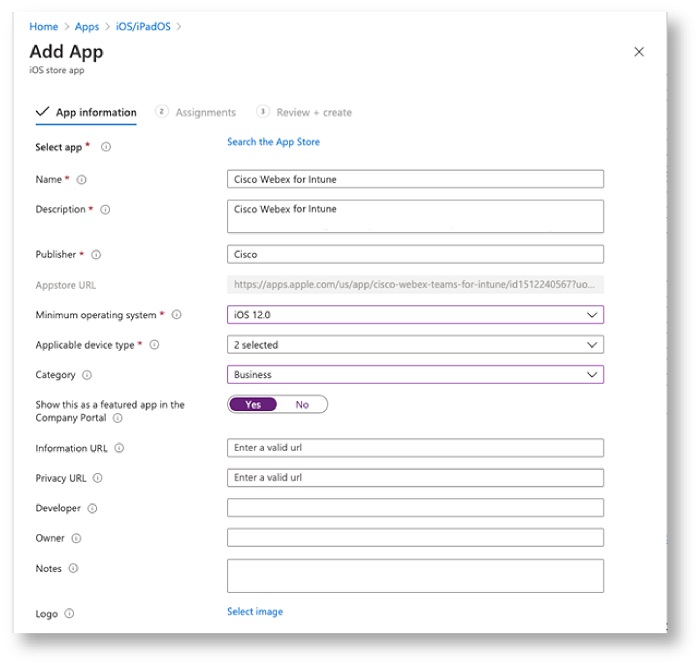
Add Webex for iOS
| 1 |
Sign in to Microsoft Endpoint Manager Admin Center. |
| 2 |
In the left pane, select Apps, and under Platform choose iOS/iPadOS. |
| 3 |
Click Add application and choose iOS store App. |
| 4 |
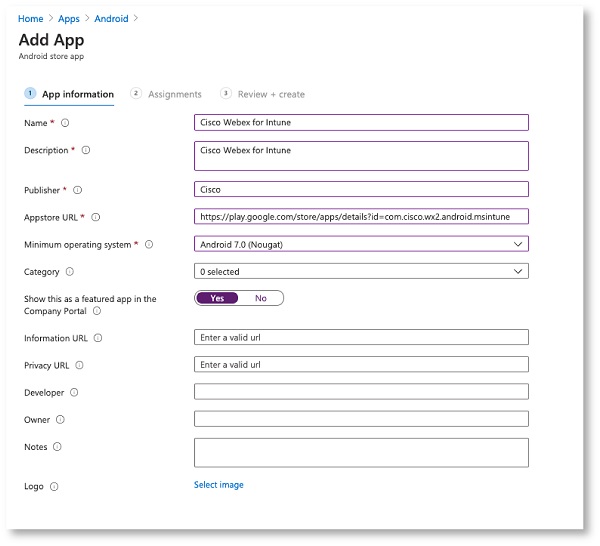
Search for Cisco Webex for Intune, enter the following information:
For iPadOS, select Minimum operating system as 13.1 and later |
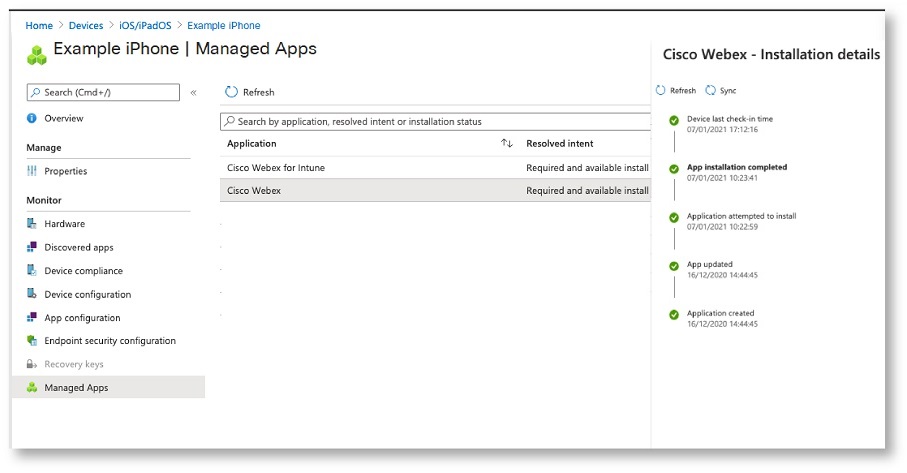
Check application installation status
| 1 |
Sign in to Microsoft Endpoint Manager Admin Center. |
| 2 |
In the left pane, select Devices and choose from Android or iOS. |
| 3 |
Select the device on which you've installed Webex, click Managed App, and then search for Cisco Webex for Intune.
|
| 4 |
Check the installation status. |
Create an app configuration policy
You can configure the Intune App Configuration Policy for both Android and iOS/iPadOS devices. You can apply these settings to both managed devices and managed applications. Webex App checks for these settings when users run the app for the first time on their mobile devices. The Intune App Configuration settings get applied, which then allows the app to be customized with app configuration and management.
Create an application protection policy
Application protection policies are rules that ensure an organization's data remains safe or contained in a managed app. A policy can be a rule that is enforced when the user attempts to access or move corporate data, or a set of actions that are prohibited or monitored when the user is in the app. App protection policies are available for MDM-managed Webex for Intune and wrapped applications (.IPA and .APK files).
If you have an existing application protection policy, you can use the same policy and assign it to the user. Or, you can use the following steps to create a new app protection policy.
You can read more about this procedure in Microsoft documentation.
| 1 |
Sign in to Microsoft Endpoint Manager Admin Center. |
| 2 |
In the left pane, select Apps and click App protection Policies. |
| 3 |
Select Create policy and choose Android or iOS. |
| 4 |
Enter a name for the protection policy and click Next. |
| 5 |
Select the target device type: Managed or Unmanaged. |
| 6 |
Click Select public apps, enter |
| 7 |
Select an appropriate option and click Next. |
| 8 |
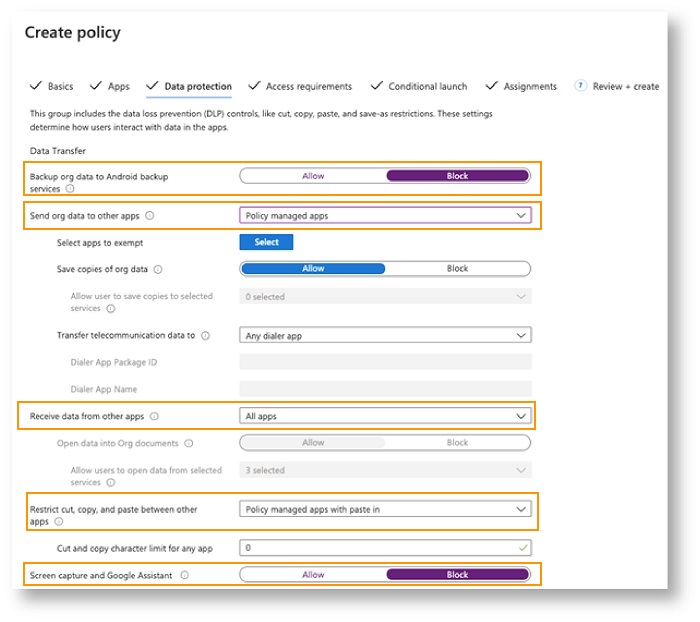
For Data protection, choose the restrictions as referenced below.
See Data protection settings for more information: |
| 9 |
(Optional) To create exemptions to the policy Select apps to exempt. Use this option if you need to configure exemptions for Webex applications. You can choose which unmanaged apps can transfer data to and from managed apps. For unmanaged Webex applications, use the following strings for the Value field on your policy's exemption list:
|
| 10 |
After configuring the settings, click Next. |
| 11 |
For Access requirements, configure a PIN and credential requirements. |
| 12 |
For Conditional launch, click Next. |
| 13 |
For Assignments, assign the policy to a Webex user group and then click Next. |
| 14 |
Review the settings you have entered and click Create. |
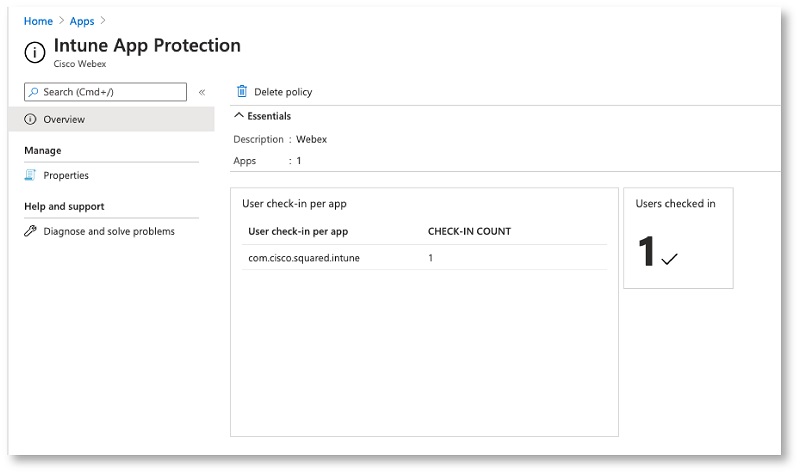
Check application protection policy
| 1 |
Sign in to Microsoft Endpoint Manager Admin Center. |
| 2 |
In the left pane, select Apps and click App Protection Policies. |
| 3 |
Select the App Protection Policy you want to check and verify that users are checked in and the policy is applied.
|
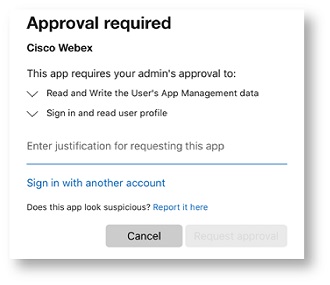
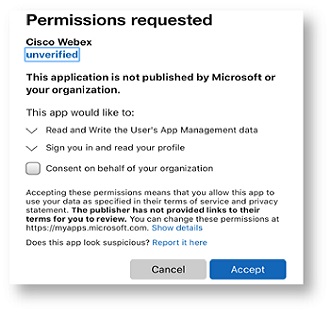
Approve user access
| 1 |
Users are prompted to request access when they sign in to Webex for the first time.
|
| 2 |
Administrators can grant permission for users to access the app from the Azure Enterprise App.
|
Supported policies
Microsoft Intune supports the following policies with Webex for Intune on managed devices:
-
Passcode/TouchID—Allow users to set up a Passcode or TouchID. The user is prompted to enter a passcode when they launch Webex App from a mobile device.
-
Maximum PIN attempts—Define the maximum number of times a user can enter an incorrect PIN.
-
Managed Open-In/Document Sharing—Allow sharing of documents from Webex for Intune to other policy-managed apps.
-
Prevent App Backup—Prevent users from saving Webex data to Android back-up service or iCloud for iOS.
-
Disable Screen Capture—Block screen capture and Google assistant capabilities. For iOS devices, use the iOS restrictions option in Intune.
-
Remotely Wipe App—Allow administrators to remotely wipe Webex for Intune from a mobile device.
-
Disable Copy and Paste—Prevent users from using copy and paste between Webex for Intune and other apps. However, you can allow copy and paste with other corporate policy-managed applications.
-
Disable Save Copies of Org Data—Block users from saving Webex for Intune data on local devices. Administrators can select services, such as OneDrive or SharePoint, to store Webex for Intune data.
-
Unlocked devices—Restrict users from running Webex for Intune on devices which have been unlocked (Jailbroken or rooted), to gain administrative or root access controls.
-
Minimum App version—Define the minimum version required for Webex for Intune to run on mobile devices.
Known limitations
Impact of PIN policy setting on Notifications
When you enable the PIN requirement in your App Protection policy, some users may experience missed calls or notifications. The Intune SDK locks the app behind the required PIN or biometric gate enforced by this policy. This prevents notifications from being fully processed or displayed until these checks are bypassed.