- Home
- /
- Article

Configure Partner SSO - SAML and OpenID Connect
 In this article
In this article Feedback?
Feedback?Set up SSO for customer organizations using SAML or OIDC for seamless authentication.
Partner SSO - SAML
Allows partner administrators to configure SAML SSO for newly created customer organizations. Partners can configure a single pre-defined SSO relationship and apply that configuration to the customer organizations that they manage, as well as to their own employees.
The below Partner SSO steps apply to newly-created customer organizations only. If partner administrators try to add Partner SSO to an existing customer organization, the existing authentication method is retained in order to prevent existing users from losing access.
-
Verify that the third-party Identity Provider provider meets the requirements listed in the Requirements for Identity Providers section of Single Sign-On Integration in Control Hub.
-
Upload the CI metadata file that has Identity Provider.
-
Configure a Onboarding Template. For the Authentication Mode setting, select Partner Authentication. For the IDP Entity ID, enter the EntityID from the SAML metadata XML of the third-party identity provider.
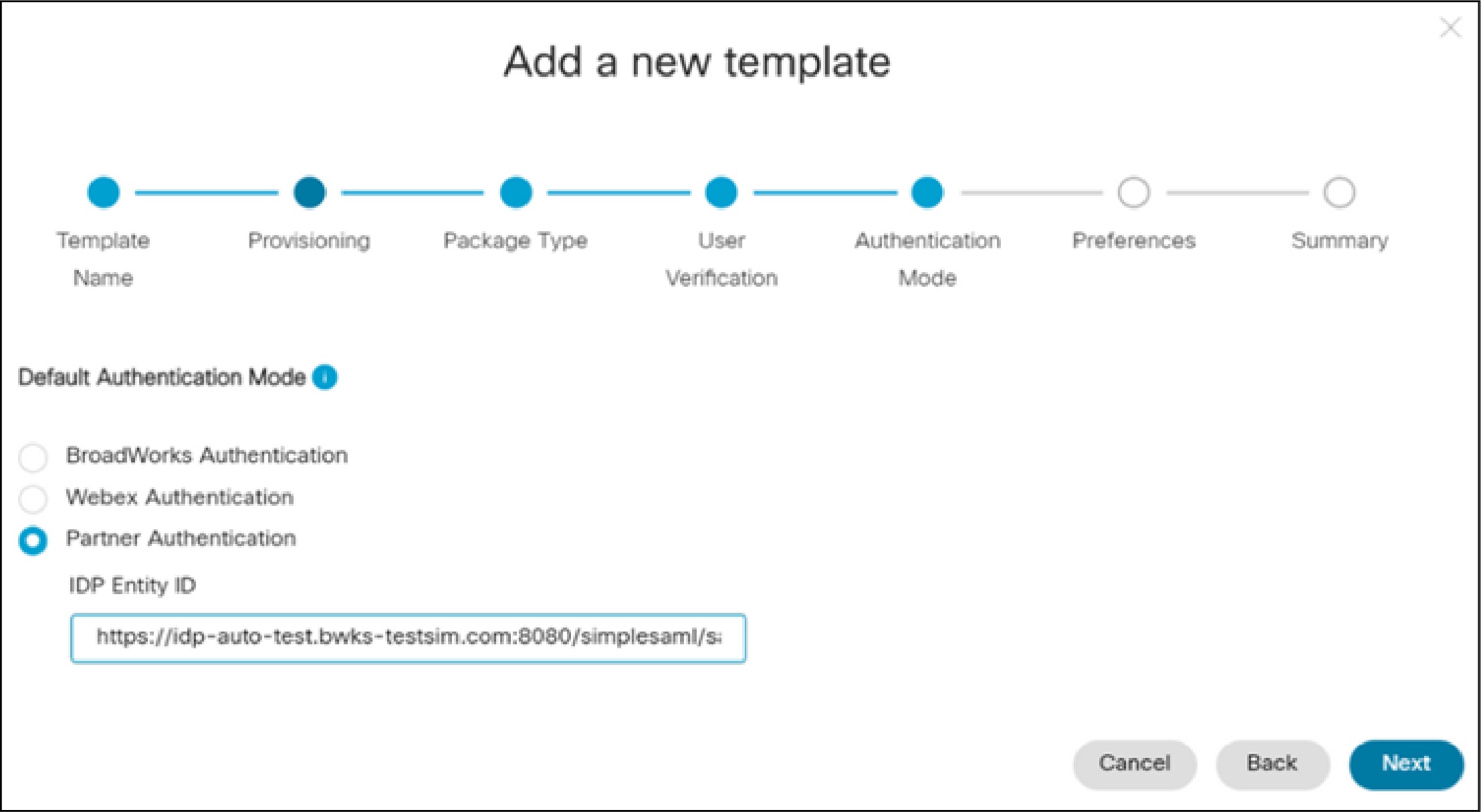
-
Create a new user in a new customer organization that uses the template.
-
Very that the user can log in.
Partner SSO - OpenID Connect (OIDC)
Allows partner administrators to configure OIDC SSO for newly created customer organizations. Partners can configure a single pre-defined SSO relationship and apply that configuration to the customer organizations that they manage, as well as to their own employees.
The below steps to set up Partner SSO OIDC apply to newly created customer organizations only. If partner administrators try to modify the default authentication type to Partner SSO OIDC in an existing temple, the changes will not apply to the customer organizations already onboarded using the template.
-
Open a Service Request with Cisco TAC with the details of the OpenID Connect IDP. The following are mandatory and optional IDP attributes. TAC must set up the IDP on the CI and provide the redirect URI to be configured on the IDP.
Attribute
Required
Description
IDP Name
Yes
Unique but case-insensitive name for OIDC IdP config, could consist of letters, numbers, hyphens, underlines, tildes, and dots and max length is 128 characters.
OAuth client Id
Yes
Used to request OIDC IdP Authentication.
OAuth client Secret
Yes
Used to request OIDC IdP Authentication.
List of scopes
Yes
List of scopes which will be used to request OIDC IdP authentication, split by space, e.g. 'openid email profile' Must including openid and email.
Authorization Endpoint
Yes if discoveryEndpoint not provided
URL of the IdP's OAuth 2.0 Authorization Endpoint.
tokenEndpoint
Yes if discoveryEndpoint not provided
URL of the IdP's OAuth 2.0 Token Endpoint.
Discovery Endpoint
No
URL of the IdP's Discovery Endpoint for OpenID endpoints discovery.
userInfoEndpoint
No
URL of the IdP's UserInfo Endpoint.
Key Set Endpoint
No
URL of the IdP's JSON Web Key Set Endpoint.
In addition to the above IDP attributes, the partner organization ID needs to be specified in the TAC request.
-
Configure the redirect URI on the OpenID connect IDP.
-
Configure a Onboarding template. For the Authentication Mode setting, select Partner Authentication With OpenID Connect and enter the IDP Name provided during the IDP setup as the OpenID Connect IDP Entity ID.
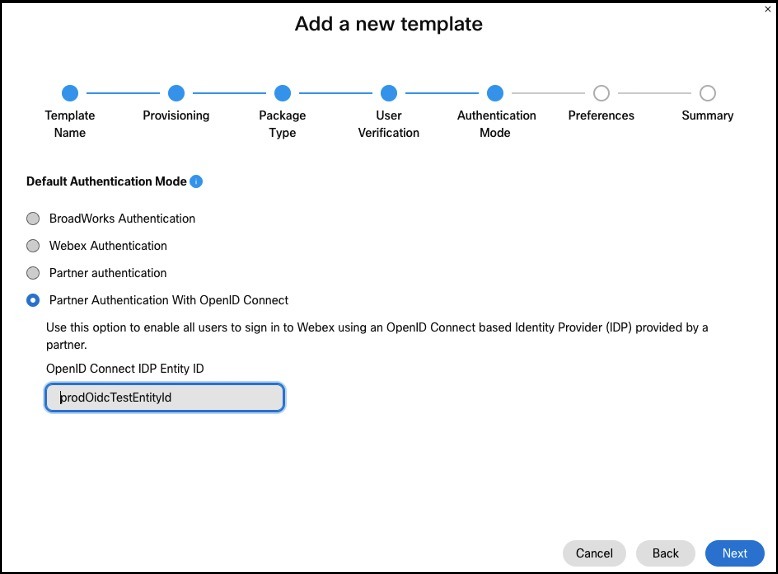
-
Create a new user in a new customer organization that uses the template.
-
Very that the user can log in using the SSO authentication flow.


