CTI Interface Configuration for Webex Integration
 Feedback?
Feedback?CTI Interface and Related Configuration
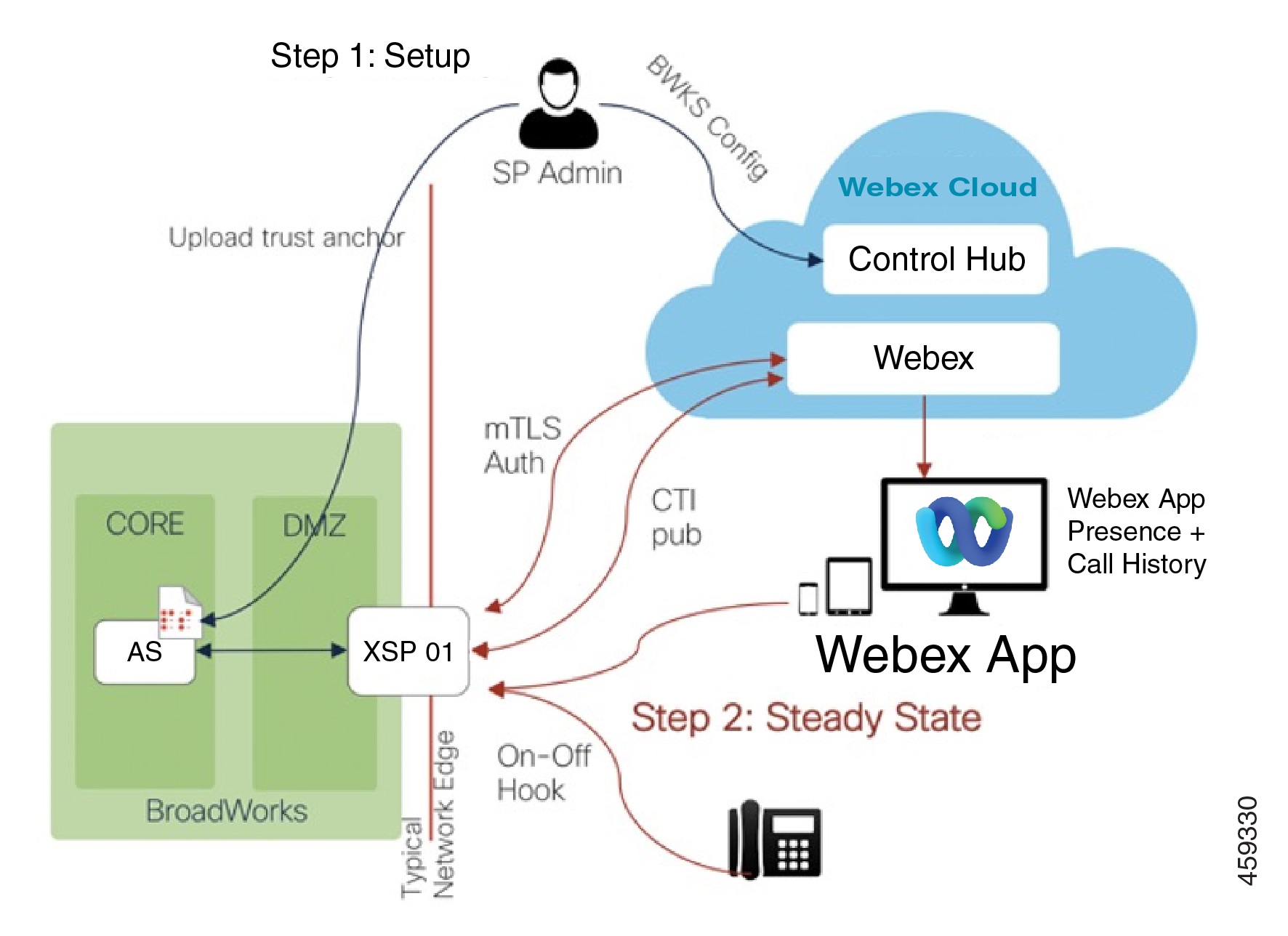
The “inmost to outmost” configuration order is listed below. Following this order is not mandatory.
-
Configure Application Server for CTI Subscriptions
-
Configure XSP|ADPs for mTLS Authenticated CTI Subscriptions
-
Open Inbound Ports for Secure CTI Interface
-
Subscribe Your Webex Organization to BroadWorks CTI Events
Configure Application Server for CTI Subscriptions
Update the ClientIdentity on Application Server with the common name (CN) of the Webex for Cisco BroadWorks CTI client certificate.
For each Application Server you are using with Webex, add the certificate identity to the ClientIdentity as follows:
AS_CLI/System/ClientIdentity> add bwcticlient.webex.com
The common name of the Webex for Cisco BroadWorks client certificate is bwcticlient.webex.com.
Configure TLS and Ciphers on the CTI Interface
The levels of configurability for the XSP|ADP CTI interface are as follows:
Most general = System > Transport > CTI Interfaces > CTI interface = Most specific
The CLI contexts you use to view or modify the different SSL settings are:
|
Specificity |
CLI Context |
|---|---|
|
System (global) (R22 and later) |
XSP|ADP_CLI/System/SSLCommonSettings/JSSE/Ciphers> XSP|ADP_CLI/System/SSLCommonSettings/JSSE/Protocols> |
|
Transport protocols for this system (R22 and later) |
XSP|ADP_CLI/System/SSLCommonSettings/OpenSSL/Ciphers> XSP|ADP_CLI/System/SSLCommonSettings/OpenSSL/Protocols> |
|
All CTI interfaces on this system (R22 and later) |
XSP|ADP_CLI/Interface/CTI/SSLCommonSettings/Ciphers> XSP|ADP_CLI/Interface/CTI/SSLCommonSettings/Protocols> |
|
A specific CTI interface on this system (R22 and later) |
XSP|ADP_CLI/Interface/CTI/CTIServer/SSLSettings/Ciphers> XSP|ADP_CLI/Interface/CTI/CTIServerSSLSettings/Protocols> |
On a fresh install, the following ciphers are installed by default at the system level. If nothing is configured at the interface level (for example, at the CTI interface or HTTP interface), this cipher list applies. Note that this list may change over time:
-
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
-
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
-
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
-
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
-
TLS_DHE_DSS_WITH_AES_128_GCM_SHA256
-
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
-
TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
-
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
-
TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256
-
TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256
-
TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
-
TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
Reading CTI TLS Interface Configuration on the XSP|ADP
-
Sign in to the XSP|ADP and navigate to
XSP|ADP_CLI/Interface/CTI/CTIServer> Enter the
getcommand and read the results. You should see the interfaces (IP addresses) and, for each, whether they require a server certificate and whether they require client authentication.XSP|ADP_CLI/Interface/CTI/CTIServer> get Interface IP Port Secure Server Certificate Client Auth Req ================================================================= 10.155.6.175 8012 true true true
Adding TLS 1.2 Protocol to the CTI Interface
The XSP|ADP CTI interface that is interacting with the Webex Cloud must be configured for TLS v1.2. The cloud does not negotiate earlier versions of the TLS protocol.
To configure the TLSv1.2 protocol on the CTI interface:
-
Sign in to the XSP|ADP and navigate to
XSP|ADP_CLI/Interface/CTI/CTIServer/SSLSettings/Protocols> -
Enter the command
get <interfaceIp>to see which protocols are already used on this interface. -
Enter the command
add <interfaceIp> TLSv1.2to ensure that interface can use TLS 1.2 when communicating with the cloud.
Editing TLS Ciphers Configuration on the CTI Interface
To configure the required ciphers on the CTI interface:
-
Sign in to the XSP|ADP and navigate to
XSP|ADP_CLI/Interface/CTI/CTIServer/SSLSettings/Ciphers> -
Enter the
getcommand to see which ciphers are already used on this interface. There must be at least one from the Cisco recommended suites (see XSP|ADP Identity and Security Requirements in the Overview section). -
Enter the command
add <interfaceIp> <cipherName>to add a cipher to the CTI interface.The XSP|ADP CLI requires the IANA standard cipher suite name, not the openSSL cipher suite name. For example, to add the openSSL cipher
ECDHE-ECDSA-CHACHA20-POLY1305to the CTI interface, you would use:XSP|ADP_CLI/Interface/CTI/CTIServer/SSLSettings/Ciphers> add 192.0.2.7 TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305See https://ciphersuite.info/ to find the suite by either name.
Trust Anchors for CTI Interface (R22 and later)
This procedure assumes the XSP|ADPs are either internet-facing or face the internet via pass-through proxy. The certificate configuration is different for a bridging proxy (see TLS Certificate Requirements for TLS-bridge Proxy).
For each XSP|ADP in your infrastructure that is publishing CTI events to Webex, do the following:
-
Sign in to Partner Hub.
-
Go to Services > Additional links and click Download Webex CA Certificate to get
CombinedCertChain2023.txton your local computer.These files contain two sets of two certificates. You need to split the files before you upload them to the XSP|ADPs. All files are required.
-
Split the certificate chain into two certificates -
combinedcertchain2023.txt-
Open
combinedcertchain2023.txtin a text editor. -
Select and cut the first block of text, including the lines
-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----, and paste the text block into a new file. -
Save the new file as
root2023.txt. -
Save the original file as
issuing2023.txt. The original file should now only have one block of text, surrounded by the lines-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----.
-
-
Copy both text files to a temporary location on the XSP|ADP you are securing, e.g.
/var/broadworks/tmp/root2023.txtand/var/broadworks/tmp/issuing2023.txt -
Sign in to the XSP|ADP and navigate to
/XSP|ADP_CLI/Interface/CTI/SSLCommonSettings/ClientAuthentication/Trusts> -
(Optional) Run
help updateTrustto see the parameters and command format. -
Upload the certificate files to new trust anchors - 2023
XSP|ADP_CLI/Interface/CTI/SSLCommonSettings/ClientAuthentication/Trusts> updateTrust webexclientroot2023 /var/broadworks/tmp/root2023.txtXSP|ADP_CLI/Interface/CTI/SSLCommonSettings/ClientAuthentication/Trusts> updateTrust webexclientissuing2023 /var/broadworks/tmp/issuing2023.txtAll aliases must have a different name.
webexclientroot2023, andwebexclientissuing2023are example aliases for the trust anchors; you can use your own as long as all entries are unique. -
Confirm the anchors are updated:
XSP|ADP_CLI/Interface/CTI/SSLCommonSettings/ClientAuthentication/Trusts> getAlias Owner Issuer ============================================================================= webexclientissuing2023 Internal Private TLS SubCA Internal Private Root webexclientroot2023 Internal Private Root Internal Private Root[self-signed] -
Allow clients to authenticate with certificates:
XSP|ADP_CLI/System/CommunicationUtility/DefaultSettings/ExternalAuthentication/CertificateAuthentication> set allowClientApp true
Add CTI Interface and Enable mTLS
-
Add the CTI SSL interface.
The CLI context depends on your BroadWorks version. The command creates a self-signed server certificate on the interface, and forces the interface to require a client certificate.
-
On BroadWorks R22 and R23:
XSP|ADP_CLI/Interface/CTI/CTIServer> add <Interface IP> 8012 true true true
-
-
Replace the server certificate and key on the XSP|ADP's CTI interfaces. You need the IP address of the CTI interface for this; you can read it from the following context:
-
On BroadWorks R22 and R23:
XSP|ADP_CLI/Interface/CTI/CTIServer> getThen run the following commands to replace the interface’s self-signed certificate with your own certificate and private key:
XSP|ADP_CLI/Interface/CTI/CTIServer/SSLSettings/Certificates> sslUpdate <interface IP> keyFile</path/to/certificate key file> certificateFile </path/to/server certificate> chainFile</path/to/chain file>
-
-
Restart the XSP|ADP.
Enable Access to BroadWorks CTI Events on Webex
You need to add and validate the CTI interface when you configure your clusters in Partner Hub. See Configure Your Partner Organization in Partner Hub for detailed instructions.
-
Specify the CTI address by which Webex can subscribe to BroadWorks CTI Events.
-
CTI subscriptions are on a per-subscriber basis and are only established and maintained while that subscriber is provisioned for Webex for Cisco BroadWorks.


