Cisco IOS XE에서 Webex Calling에 대해 로컬 게이트웨이 구성
 피드백이 있습니까?
피드백이 있습니까?개요
Webex Calling은 현재 두 가지 버전의 Local Gateway를 지원합니다.
-
로컬 게이트웨이
-
정부용 Webex 로컬 게이트웨이
-
시작하기 전에 Webex 통화에 필요한 구내 공중전화망(PSTN) 및 로컬 게이트웨이(LGW) 요구 사항을 숙지하십시오. 자세한 정보는 Webex Calling Cisco 선호하는 아키텍처를 참조하십시오.
-
이 문서는 기존의 음성 구성이 없는 전용 로컬 게이트웨이 플랫폼이 위치하는 것으로 가정합니다. 기존 PSTN 게이트웨이 또는 CUBE Enterprise 구축 환경을 Webex 통화용 로컬 게이트웨이 기능으로 사용하도록 수정하는 경우 구성에 특히 주의해야 합니다. 변경 사항으로 인해 기존 통화 흐름 및 기능이 중단되지 않도록 하십시오.
해당 절차에는 개별 명령 옵션에 대해 자세히 알아볼 수 있는 명령 참조 문서 링크가 포함되어 있습니다. 달리 명시되지 않는 한 모든 명령 참조 링크는 Webex 관리 게이트웨이 명령 참조 로 이동합니다(달리 명시된 경우 명령 링크는 Cisco IOS 음성 명령 참조로 이동합니다). 이러한 모든 가이드는 Cisco Unified Border Element Command References에서 확인할 수 있습니다.
지원되는 타사 SBC에 대한 자세한 내용은 해당 제품 참조 문서를 참조하십시오.
로컬 게이트웨이를 구성할 수 있는 두 가지 옵션이 Webex Calling 있습니다.
-
등록 기반 트렁크
-
인증서 기반 트렁크
Webex 통화 트렁크용 로컬 게이트웨이를 구성하려면 등록 기반 로컬 게이트웨이 또는 인증서 기반 로컬 게이트웨이 아래의 작업 흐름을 사용하십시오.
다양한 트렁크 유형에 대한 자세한 내용은 로컬 게이트웨이 시작하기 를 참조하세요. CLI(Command Line Interface)를 사용하여 로컬 게이트웨이 자체에서 다음 단계를 실행합니다. 저희는 트렁크 보안을 위해 SIP(Session Initiation Protocol) 및 TLS(Transport Layer Security) 전송 프로토콜을 사용하고, 로컬 게이트웨이와 Webex 통화 간의 미디어 보안을 위해 SRTP(Secure Real Time Protocol)를 사용합니다.
-
로컬 게이트웨이로 CUBE를 선택하십시오. Webex for Government는 현재 타사 세션 경계 컨트롤러(SBC)를 지원하지 않습니다. 최신 목록을 확인하려면 로컬 게이트웨이 시작하기를 참조하세요.
- 모든 Webex for Government 로컬 게이트웨이에 Cisco IOS XE Dublin 17.12.1a 이상 버전을 설치하십시오.
-
Webex for Government에서 지원하는 루트 인증 기관(CA) 목록을 검토하려면 Webex for Government용 루트 인증 기관을 참조하세요.
-
Webex for Government의 로컬 게이트웨이에 대한 외부 포트 범위에 대한 자세한 내용은 Webex for Government의 네트워크 요구 사항(FedRAMP)을 참조하세요.
정부용 Webex 로컬 게이트웨이는 다음 기능을 지원하지 않습니다.
-
STUN/ICE-Lite 미디어 경로 최적화를 위해
-
팩스 (T.38)
Webex for Government에서 Webex 통화 트렁크용 로컬 게이트웨이를 구성하려면 다음 옵션을 사용하십시오.
-
인증서 기반 트렁크
인증서 기반 로컬 게이트웨이 아래의 작업 흐름을 사용하여 Webex 통화 트렁크용 로컬 게이트웨이를 구성하십시오. 인증서 기반 로컬 게이트웨이를 구성하는 방법에 대한 자세한 내용은 인증서 기반 트렁크를 사용한 Webex 통화 구성을 참조하세요.
Webex for Government의 로컬 게이트웨이를 지원하려면 FIPS 규격을 준수하는 GCM 암호화 방식을 구성하는 것이 필수적입니다. 그렇지 않으면 통화 연결이 실패합니다. 구성 세부 정보는 Webex 통화 인증서 기반 트렁크 구성을 참조하세요.
Webex for Government는 등록 기반 로컬 게이트웨이를 지원하지 않습니다.
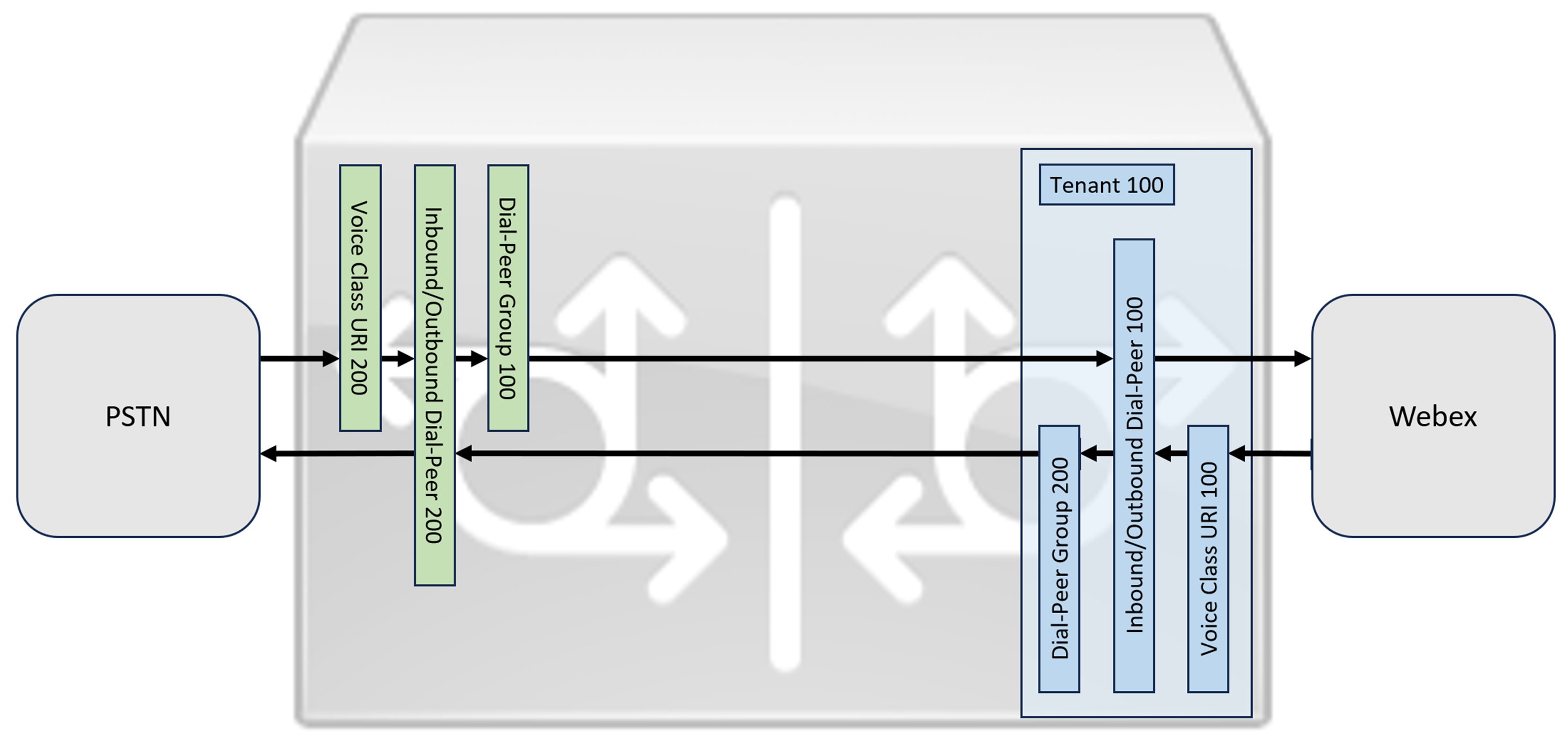
이 섹션에서는 등록된 SIP 트렁크를 사용하여 Cisco Unified Border Element(CUBE)를 Webex 통화용 로컬 게이트웨이로 구성하는 방법을 설명합니다. 이 문서의 첫 번째 부분에서는 간단한 PSTN 게이트웨이를 구성하는 방법을 설명합니다. 이 경우, PSTN에서 걸려오는 모든 통화는 Webex Calling으로 연결되고, Webex Calling에서 걸려오는 모든 통화는 PSTN으로 연결됩니다. 아래 이미지는 이 솔루션과 향후 적용될 상위 수준 통화 라우팅 구성을 보여줍니다.
이 설계에서는 다음과 같은 주요 구성이 사용됩니다.
-
음성 클래스 테넌트: 트렁크별 구성을 생성하는 데 사용됩니다.
-
음성 클래스 uri: 수신 다이얼 피어 선택을 위해 SIP 메시지를 분류하는 데 사용됩니다.
-
수신 다이얼 피어: 수신 SIP 메시지를 처리하고 다이얼 피어 그룹을 사용하여 발신 경로를 결정합니다.
-
다이얼 피어 그룹: 통화 연결 라우팅에 사용되는 발신 다이얼 피어를 정의합니다.
-
발신 다이얼 피어: 발신 SIP 메시지를 처리하고 필요한 대상으로 라우팅합니다.
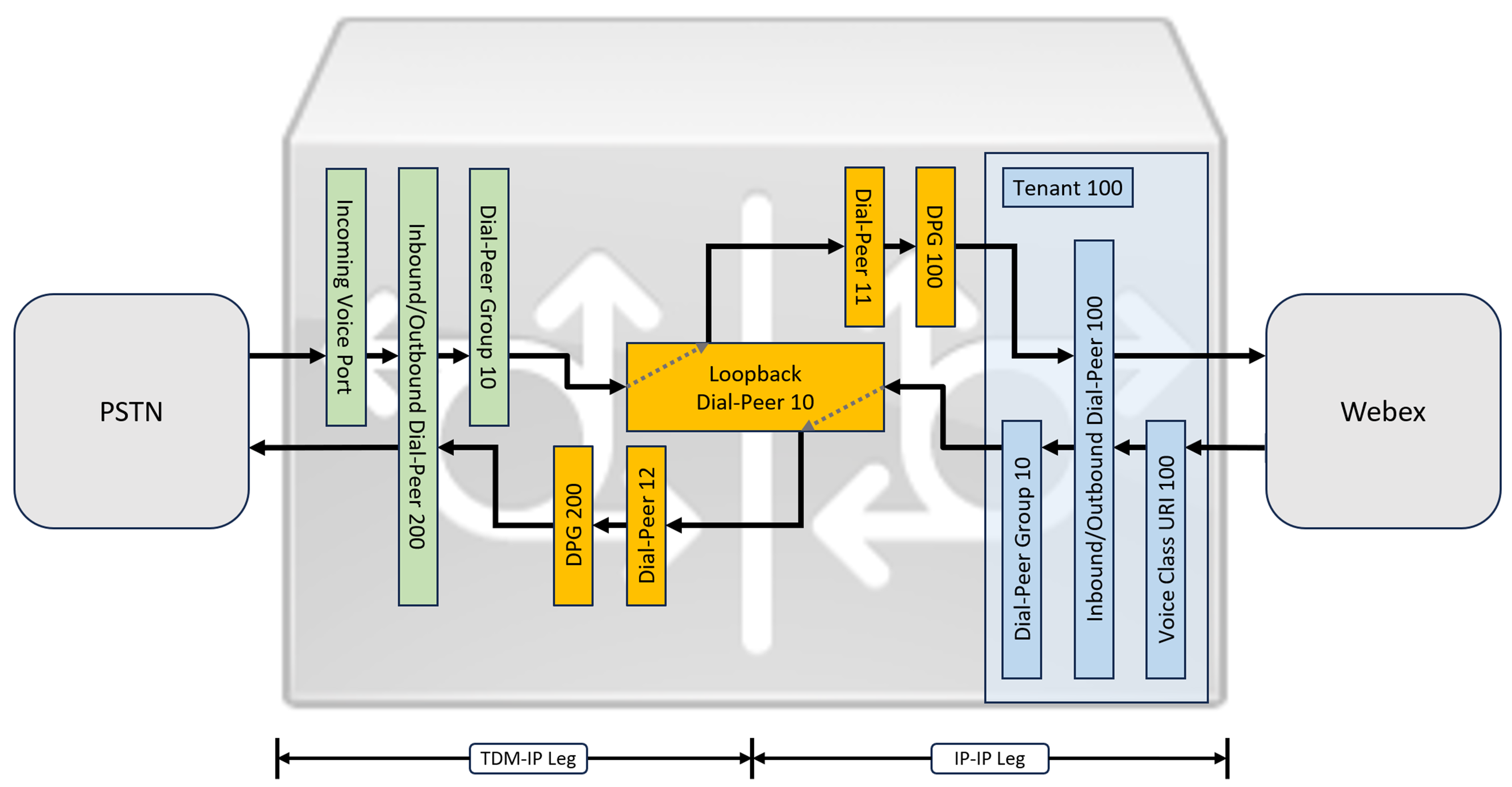
IP와 SIP가 PSTN 회선의 기본 프로토콜이 되었지만, TDM(시분할 다중화) 방식의 ISDN 회선도 여전히 널리 사용되고 있으며 Webex 통화 회선에서 지원됩니다. TDM-IP 통화 흐름을 사용하는 로컬 게이트웨이의 IP 경로에 대한 미디어 최적화를 활성화하려면 현재 2단계 통화 라우팅 프로세스를 사용해야 합니다. 이 접근 방식은 아래 이미지에 표시된 것처럼 Webex Calling과 PSTN 트렁크 사이에 내부 루프백 다이얼 피어 세트를 도입하여 위에 표시된 통화 라우팅 구성을 수정합니다.
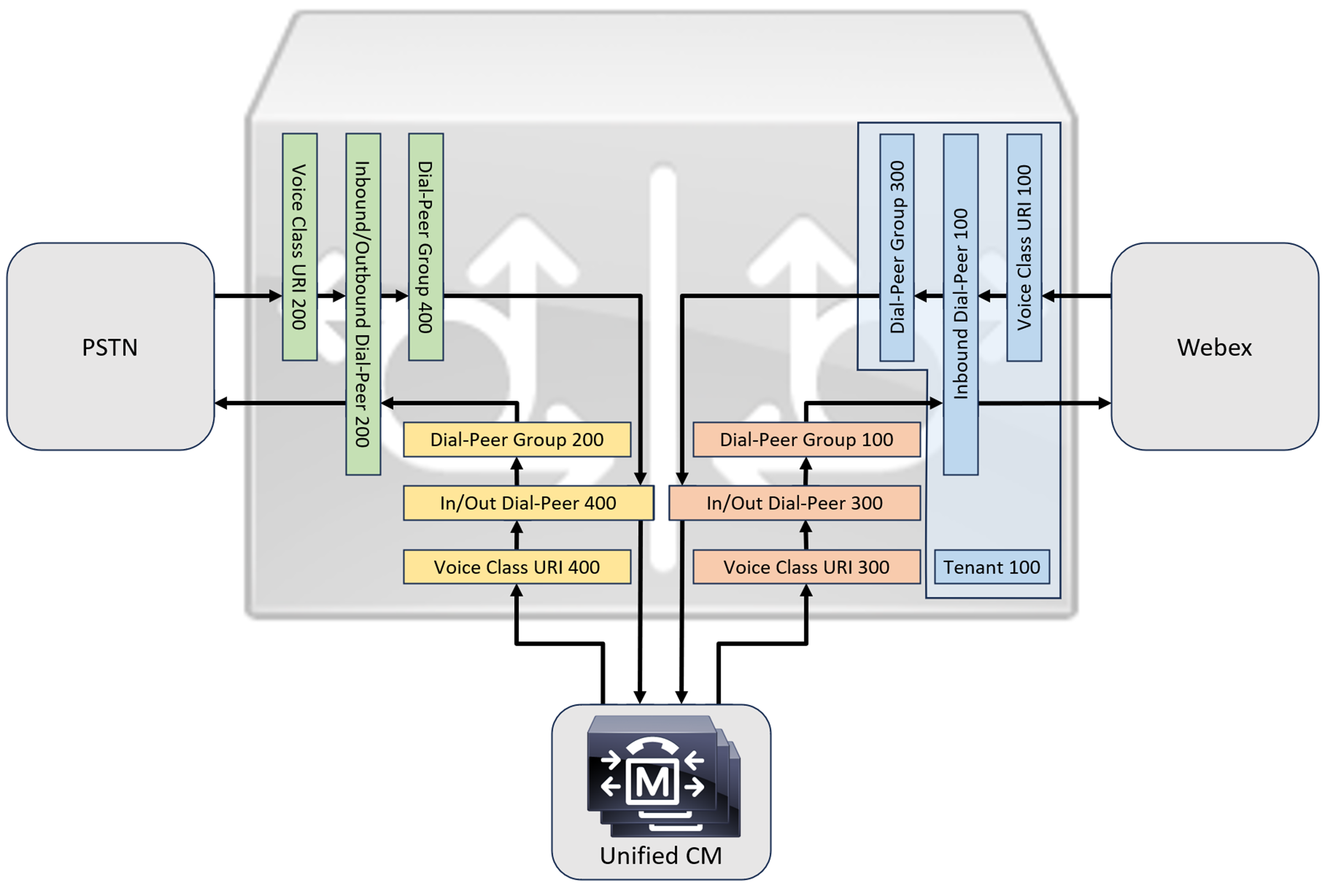
온프레미스 Cisco Unified Communications Manager 솔루션을 Webex Calling에 연결할 때, 다음 다이어그램에 나와 있는 솔루션을 구축하기 위한 기본 구성으로 간단한 PSTN 게이트웨이 구성을 사용할 수 있습니다. 이 경우 통합 커뮤니케이션 관리자는 모든 PSTN 및 Webex 통화에 대한 중앙 집중식 라우팅 및 처리를 제공합니다.
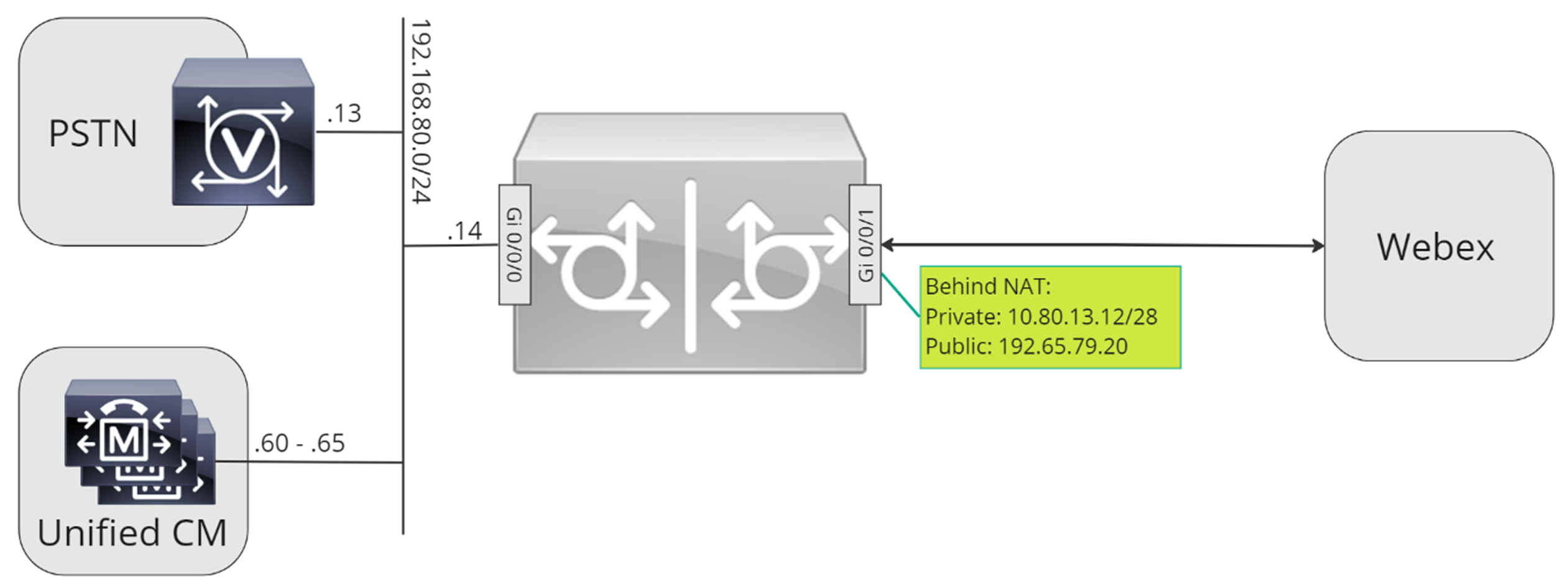
이 문서 전체에서 다음 이미지에 표시된 호스트 이름, IP 주소 및 인터페이스가 사용됩니다.
이 문서의 나머지 부분에 있는 구성 지침을 사용하여 다음과 같이 로컬 게이트웨이 구성을 완료하십시오.
-
1단계: 라우터 기본 연결 및 보안을 구성합니다.
-
2단계: Webex 통화 트렁크 구성
필요한 아키텍처에 따라 다음 중 하나를 따르십시오.
-
단계 3: SIP PSTN 트렁크를 사용하여 로컬 게이트웨이를 구성합니다.
-
단계 4: 기존의 Unified CM 환경에서 로컬 게이트웨이 구성
또는:
-
단계 3: TDM PSTN 트렁크를 사용하여 로컬 게이트웨이를 구성합니다.
기본 구성
Cisco 라우터를 Webex 통화용 로컬 게이트웨이로 준비하는 첫 번째 단계는 플랫폼을 보호하고 연결을 설정하는 기본 구성을 구축하는 것입니다.
-
등록 기반 로컬 게이트웨이 구축에는 Cisco IOS XE 17.6.1a 이상 버전이 필요합니다. Cisco IOS 17.12.2 이상 버전을 권장합니다. 권장 버전에 대해서는 Cisco 소프트웨어 연구 페이지를 참조하십시오. 플랫폼을 검색하고 개의 제안된 릴리스 중 하나를 선택하십시오.
-
ISR4000 시리즈 라우터는 통합 커뮤니케이션 및 보안 기술 라이선스를 모두 구성해야 합니다.
-
음성 카드 또는 DSP가 장착된 Catalyst Edge 8000 시리즈 라우터에는 DNA Advantage 라이선스가 필요합니다. 음성 카드나 DSP가 없는 라우터는 최소한 DNA Essentials 라이선스가 필요합니다.
-
-
회사 정책에 부합하는 플랫폼 기본 구성을 구축하세요. 특히 다음 사항을 구성하고 확인하십시오.
-
NTP
-
Acl
-
사용자 인증 및 원격 액세스
-
DNS
-
IP 라우팅
-
IP 주소
-
-
Webex 통화로 향하는 네트워크는 IPv4 주소를 사용해야 합니다.
-
Cisco 루트 CA 번들을 로컬 게이트웨이에 업로드하십시오.
구성
| 1 |
예를 들어, 모든 레이어 3 인터페이스에 유효하고 라우팅 가능한 IP 주소를 할당해야 합니다.
|
| 2 |
라우터에서 등록 및 STUN 자격 증명을 대칭 암호화를 사용하여 보호하십시오. 기본 암호화 키와 암호화 유형을 다음과 같이 구성하십시오.
|
| 3 |
임시 PKI 트러스트포인트를 생성합니다. TLS를 나중에 구성하려면 이 트러스트포인트가 필요합니다. 등록 기반 트렁크의 경우, 이 트러스트포인트에는 인증서가 필요하지 않습니다. 이는 인증서 기반 트렁크에 필요한 것과는 다른 점입니다. |
| 4 |
다음 구성 명령을 사용하여 TLS 1.2 독점성을 활성화하고 기본 트러스트포인트를 지정하십시오. 등록을 위한 안정적이고 안전한 연결을 보장하기 위해 전송 매개변수를 업데이트하십시오.
|
| 5 |
Webex 통화에서 사용하는 IdenTrust 상용 루트 CA1 인증서가 포함된 Cisco 루트 CA 번들을 설치하십시오. crypto pki trustpool import clean url 명령어를 사용하여 지정된 URL에서 루트 CA 번들을 다운로드하고 현재 CA 트러스트풀을 지운 다음 새 인증서 번들을 설치하십시오. HTTPS를 사용하여 인터넷에 접속하기 위해 프록시를 사용해야 하는 경우, CA 번들을 가져오기 전에 다음 구성을 추가하십시오. ip http 클라이언트 프록시 서버 yourproxy.com 프록시 포트 80 |
| 1 |
제어 허브에서 기존 위치에 대한 등록 기반 PSTN 트렁크를 생성합니다. 트렁크가 생성되면 제공되는 트렁크 정보를 기록해 두십시오. 그림에서 강조 표시된 세부 정보는 이 가이드의 구성 단계에서 사용됩니다. 자세한 내용은 Webex 통화용 트렁크, 라우트 그룹 및 다이얼 플랜 구성을 참조하세요. 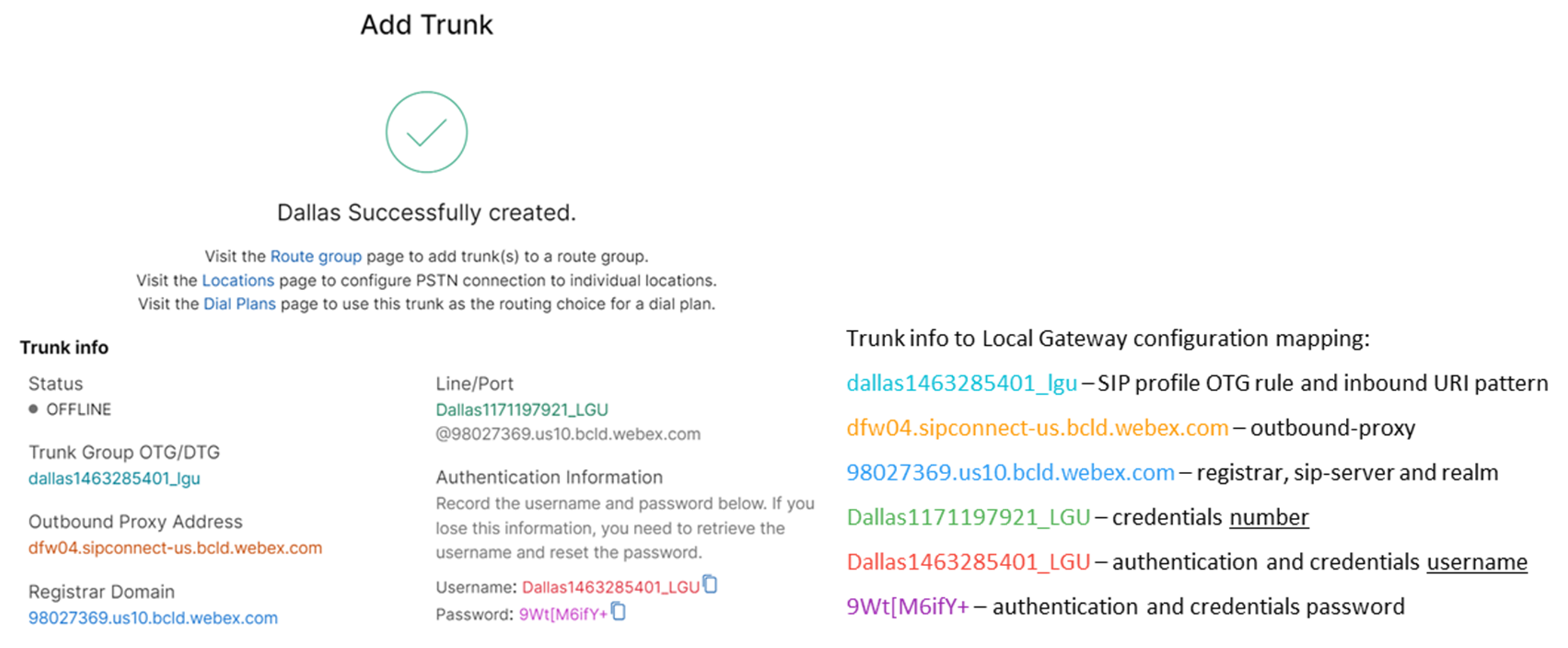 |
| 2 |
CUBE를 Webex 통화 로컬 게이트웨이로 구성하려면 다음 명령어를 입력하십시오. 구성에 대한 필드의 설명은 다음과 같습니다.
플랫폼에서 Cisco Unified Border Element(CUBE) 기능을 활성화합니다. 미디어 통계로컬 게이트웨이에서 미디어 모니터링을 가능하게 합니다. 미디어 대량 통계일괄 통화 통계에 대해 데이터가 저장되는 설문조사를 진행할 수 있습니다. 이러한 명령에 대한 자세한 내용은 미디어를 참조하십시오. allow-connections sip to sipCUBE의 기본 SIP 백투백 사용자 에이전트 기능을 활성화합니다. 자세한 내용은 연결 허용을 참조하세요. 기본적으로 T.38 팩스 전송이 활성화되어 있습니다. 자세한 내용은 팩스 프로토콜 t38(음성 서비스)을 참조하십시오. STUN(NAT를 통한 UDP 세션 트래버스)을 전역적으로 활성화합니다.
자세한 내용은 stun flowdata agent-id 및 stun flowdata shared-secret를 참조하십시오. 비대칭 페이로드 전체DTMF 및 동적 코덱 페이로드 모두에 대해 SIP 비대칭 페이로드 지원을 구성합니다. 자세한 내용은 비대칭 페이로드를 참조하세요. early-offer forced로컬 게이트웨이가 인접 피어로부터 승인을 기다리는 대신 초기 INVITE 메시지에 SDP 정보를 전송하도록 강제합니다. 이 명령에 대한 자세한 내용은 early-offer를 참조하십시오. |
| 3 |
음성 클래스 코덱 100 을 구성하여 모든 트렁크에 대해 G.711 코덱만 허용합니다. 이러한 간단한 접근 방식은 대부분의 배포 환경에 적합합니다. 필요한 경우, 송신 시스템과 수신 시스템 모두에서 지원하는 추가 코덱 유형을 목록에 추가할 수 있습니다. DSP 모듈을 사용한 트랜스코딩 을 포함하는 더 복잡한 솔루션도 지원되지만 이 가이드에는 포함되어 있지 않습니다. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 코덱 100SIP 트렁크 통화에 대해 선호하는 코덱만 허용하도록 설정하는 데 사용됩니다. 자세한 내용은 음성 클래스 코덱을 참조하세요. |
| 4 |
Webex 통화 트렁크에서 ICE를 활성화하려면 voice class stun-usage 100 을 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 기절 사용 얼음 빛Webex 통화에 연결된 모든 다이얼 피어에 ICE-Lite를 활성화하여 가능한 경우 미디어 최적화를 허용하는 데 사용됩니다. 자세한 내용은 음성 클래스 기절 사용법 및 기절 사용법 아이스 라이트를 참조하세요. 미디어 최적화는 가능한 경우 협상을 통해 이루어집니다. 통화에 녹음과 같은 클라우드 미디어 서비스가 필요한 경우, 해당 미디어를 최적화할 수 없습니다. |
| 5 |
Webex 트래픽에 대한 미디어 암호화 정책을 구성합니다. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 srtp-crypto 100오퍼 및 응답 메시지에서 CUBE가 SDP에서 제공하는 유일한 SRTP 암호화 스위트로 SHA1_80을 지정합니다. Webex 통화는 SHA1_80만 지원합니다. 자세한 내용은 음성 클래스 srtp-crypto를 참조하세요. |
| 6 |
대상 트렁크 매개변수를 기반으로 로컬 게이트웨이 트렁크로의 호출을 식별하는 패턴을 구성합니다. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 uri 100 sip수신되는 SIP 초대를 수신되는 트렁크 다이얼 피어와 일치시키는 패턴을 정의합니다. 이 패턴을 입력할 때는 dtg= 다음에 Trunk를 사용하십시오. OTG/DTG 트렁크 생성 시 컨트롤 허브에 제공된 값입니다. 자세한 내용은 음성 클래스 uri를 참조하세요. |
| 7 |
Webex 통화로 전송하기 전에 SIP 메시지를 수정하는 데 사용될 sip 프로필 100을 구성합니다.
구성에 대한 필드의 설명은 다음과 같습니다.
미국 또는 캐나다 PSTN 제공업체는 Webex 통화의 스팸 또는 사기 통화 표시 문서에 언급된 추가 구성을 통해 스팸 및 사기 통화에 대한 발신자 ID 확인을 제공할 수 있습니다. |
| 8 |
Webex 통화 트렁크 구성: |
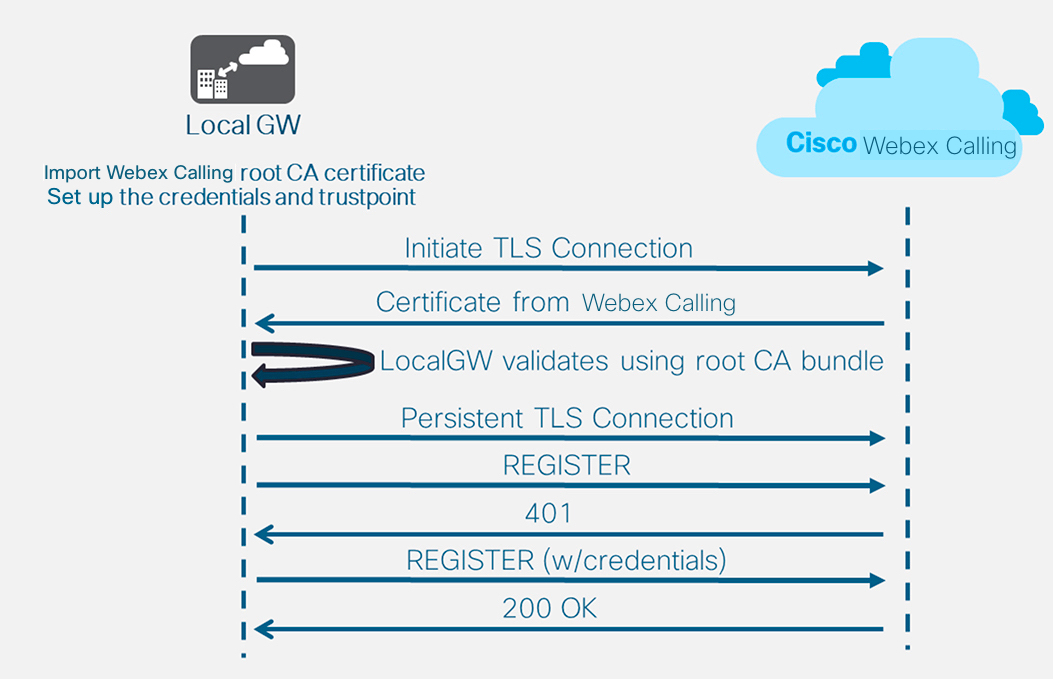
테넌트 100 를 정의하고 SIP VoIP 다이얼 피어를 구성한 후 게이트웨이는 Webex Calling을 향해 TLS 연결을 시작합니다. 이 시점에서 액세스 SBC는 로컬 게이트웨이에 인증서를 제시합니다. 로컬 게이트웨이는 이전에 업데이트된 CA 루트 번들을 사용하여 Webex 통화 액세스 SBC 인증서를 검증합니다. 인증서가 인식되면 로컬 게이트웨이와 Webex 통화 액세스 SBC 간에 영구적인 TLS 세션이 설정됩니다. 로컬 게이트웨이는 이 보안 연결을 사용하여 Webex 액세스 SBC에 등록할 수 있습니다. 등록 시 인증 문제가 발생할 경우:
-
자격 증명 ] 구성의 [] 사용자 이름, 암호및 영역 매개변수가 응답에 사용됩니다.
-
SIP 프로필 100의 수정 규칙은 SIPS URL을 SIP로 다시 변환하는 데 사용됩니다.
접속 SBC로부터 200 OK 응답을 받으면 등록이 성공적으로 완료된 것입니다.
위에서 설명한 대로 Webex 통화용 트렁크를 구축한 후, 다음 구성을 사용하여 SIP 기반 PSTN 공급자를 향한 암호화되지 않은 트렁크를 생성하십시오.
서비스 제공업체에서 보안 PSTN 회선을 제공하는 경우, 위에서 설명한 Webex 통화 회선 구성과 유사한 방식으로 구성할 수 있습니다. CUBE는 안전한 통화 라우팅을 지원합니다.
TDM을 사용하고 있다면 / ISDN PSTN 트렁크, 다음 섹션으로 건너뛰기 TDM PSTN 트렁크를 사용한 로컬 게이트웨이 구성.
Cisco TDM-SIP 게이트웨이에서 PSTN 통화 구간용 TDM 인터페이스를 구성하려면 ISDN PRI 구성을 참조하십시오.
| 1 |
PSTN 회선에서 걸려오는 수신 전화를 식별하려면 다음 음성 클래스 URI를 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 uri 200 sip수신되는 SIP 초대를 수신되는 트렁크 다이얼 피어와 일치시키는 패턴을 정의합니다. 이 패턴을 입력할 때는 IP PSTN 게이트웨이의 IP 주소를 사용하십시오. 자세한 내용은 음성 클래스 uri를 참조하세요. |
| 2 |
다음 IP PSTN 다이얼 피어를 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 태그가 200 인 VoIP 다이얼 피어를 정의하고 관리 및 문제 해결을 용이하게 하기 위해 의미 있는 설명을 제공합니다. 자세한 내용은 다이얼 피어 음성을 참조하십시오. 목적지 패턴 BAD.BAD수신 다이얼 피어 그룹을 사용하여 발신 통화를 라우팅할 때는 더미 대상 패턴이 필요합니다. 이 경우에는 유효한 목적지 패턴이라면 무엇이든 사용할 수 있습니다. 자세한 내용은 대상 패턴(인터페이스)을 참조하세요. session protocol sipv2이 다이얼 피어가 SIP 통화 연결을 처리함을 지정합니다. 자세한 내용은 세션 프로토콜(다이얼 피어)을 참조하세요. 세션 대상 IPv4: 192.168.80.13PSTN 제공업체로 전송되는 통화의 대상 주소를 지정합니다. 이는 IP 주소 또는 DNS 호스트 이름일 수 있습니다. 자세한 내용은 세션 대상(VoIP 다이얼 피어)을 참조하세요. 수신 URI 경유 200INVITE VIA 헤더 URI를 사용하여 수신 전화를 이 다이얼 피어와 일치시키는 데 사용되는 음성 클래스를 지정합니다. 자세한 내용은 수신 URL을 참조하세요. 음성 클래스 sip 주장된 ID pai
(선택 사항) P-Asserted-Identity 헤더 처리를 활성화하고 PSTN 트렁크에 이 헤더가 사용되는 방식을 제어합니다. 이 명령을 사용하면 수신 다이얼 피어에서 제공하는 발신자 ID가 발신 From 및 P-Asserted-Identity 헤더에 사용됩니다. 이 명령을 사용하지 않으면 수신 다이얼 피어에서 제공하는 발신자 ID가 발신 From 및 Remote-Party-ID 헤더에 사용됩니다. 자세한 내용은 voice-class sip asserted-id를 참조하세요. 바인드 제어 소스 인터페이스 GigabitEthernet0/0/0
PSTN으로 전송되는 메시지에 대한 소스 인터페이스와 연결된 IP 주소를 구성합니다. 자세한 내용은 bind를 참조하세요. 미디어 소스 인터페이스 바인딩 GigabitEthernet0/0/0PSTN으로 전송되는 미디어의 소스 인터페이스와 연결된 IP 주소를 구성합니다. 자세한 내용은 bind를 참조하세요. 음성 클래스 코덱 100다이얼 피어가 공통 코덱 필터 목록 100을 사용하도록 구성합니다. 자세한 내용은 음성 클래스 코덱을 참조하세요. dtmf-relay rtp-nteRTP-NTE(RFC2833)를 통화 레그에서 기대하는 DTMF 기능으로 정의합니다. 자세한 내용은 DTMF 릴레이(VoIP)를 참조하세요. no vad음성 활동 탐지를 비활성화합니다. 자세한 내용은 vad(다이얼 피어)를 참조하세요. |
| 3 |
Webex Calling과 PSTN 간의 통화만 라우팅하도록 로컬 게이트웨이를 구성하는 경우 다음 통화 라우팅 구성을 추가하십시오. 통합 커뮤니케이션 관리자 플랫폼을 사용하여 로컬 게이트웨이를 구성하는 경우 다음 섹션으로 건너뛰십시오. |
Webex 통화용 트렁크를 구축한 후, 다음 구성을 사용하여 루프백 통화 라우팅이 포함된 PSTN 서비스용 TDM 트렁크를 생성하면 Webex 통화 구간에서 미디어 최적화가 가능해집니다.
IP 미디어 최적화가 필요하지 않은 경우 SIP PSTN 트렁크 구성 단계를 따르십시오. PSTN VoIP 다이얼 피어 대신 음성 포트와 POTS 다이얼 피어를 사용하십시오(2단계 및 3단계 참조).
| 1 |
루프백 다이얼 피어 구성은 다이얼 피어 그룹과 통화 라우팅 태그를 사용하여 통화 라우팅 루프를 생성하지 않고 Webex와 PSTN 간에 통화가 올바르게 전달되도록 합니다. 통화 라우팅 태그를 추가 및 제거하는 데 사용될 다음 변환 규칙을 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 번역 규칙규칙에 정의된 정규 표현식을 사용하여 통화 라우팅 태그를 추가하거나 제거합니다. 10진수 이상의 숫자('A')는 문제 해결을 위해 명확성을 높이는 데 사용됩니다. 이 구성에서는 translation-profile 100에 의해 추가된 태그가 Webex Calling에서 루프백 다이얼 피어를 통해 PSTN으로 통화를 연결하는 데 사용됩니다. 마찬가지로, translation-profile 200에 의해 추가된 태그는 PSTN에서 Webex 통화로의 통화 연결을 안내하는 데 사용됩니다. 번역 프로필 11과 12는 각각 Webex 및 PSTN 회선으로 통화를 전달하기 전에 이러한 태그를 제거합니다. 이 예시에서는 Webex 통화에서 걸려온 번호가 다음과 같이 표시된다고 가정합니다. +E.164 체재. 규칙 100은 선행을 제거합니다. + 유효한 발신 번호를 유지하기 위해. 규칙 12는 태그를 제거할 때 국가 또는 국제 라우팅 번호를 추가합니다. 해당 지역의 ISDN 국가 다이얼링 플랜에 맞는 숫자를 사용하십시오. Webex 통화에서 전화번호가 국가 번호 형식으로 표시되는 경우, 규칙 100과 12를 수정하여 각각 라우팅 태그를 추가하고 제거하십시오. |
| 2 |
트렁크 유형 및 사용 프로토콜에 따라 TDM 음성 인터페이스 포트를 필요에 맞게 구성하십시오. 자세한 내용은 ISDN PRI 구성을 참조하세요. 예를 들어, 장치의 NIM 슬롯 2에 설치된 기본 속도 ISDN 인터페이스의 기본 구성은 다음과 같을 수 있습니다. |
| 3 |
다음과 같은 TDM PSTN 다이얼 피어를 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 태그가 200인 VoIP 다이얼 피어를 정의하고 관리 및 문제 해결을 용이하게 하기 위해 의미 있는 설명을 제공합니다. 자세한 내용은 dial-peer voice를 참조하세요. 목적지 패턴 BAD.BAD수신 다이얼 피어 그룹을 사용하여 발신 통화를 라우팅할 때는 더미 대상 패턴이 필요합니다. 이 경우에는 유효한 목적지 패턴이라면 무엇이든 사용할 수 있습니다. 자세한 내용은 대상 패턴(인터페이스)을 참조하세요. 번역 프로필 수신 200수신 전화번호에 통화 라우팅 태그를 추가하는 변환 프로필을 지정합니다. 직통 전화보조 발신음을 제공하지 않고 통화를 연결합니다. 자세한 내용은 direct-inward-dial을 참조하세요. 포트 0/2/0:15이 다이얼 피어와 연결된 물리적 음성 포트입니다. |
| 4 |
TDM-IP 통화 흐름을 사용하는 로컬 게이트웨이의 IP 경로에 대한 미디어 최적화를 활성화하려면 Webex Calling과 PSTN 트렁크 사이에 내부 루프백 다이얼 피어 세트를 추가하여 통화 라우팅을 수정할 수 있습니다. 다음 루프백 다이얼 피어를 구성하십시오. 이 경우 모든 수신 전화는 먼저 다이얼 피어 10으로 연결된 다음, 적용된 라우팅 태그에 따라 다이얼 피어 11 또는 12로 연결됩니다. 라우팅 태그가 제거되면 통화는 다이얼 피어 그룹을 사용하여 발신 트렁크로 연결됩니다. 구성에 대한 필드의 설명은 다음과 같습니다. VoIP 다이얼 피어를 정의하고 관리 및 문제 해결을 용이하게 하기 위해 의미 있는 설명을 제공합니다. 자세한 내용은 dial-peer voice를 참조하세요. 번역 프로필 수신 11이전에 정의한 변환 프로필을 적용하여 발신 트렁크로 전달하기 전에 통화 라우팅 태그를 제거합니다. 목적지 패턴 BAD.BAD수신 다이얼 피어 그룹을 사용하여 발신 통화를 라우팅할 때는 더미 대상 패턴이 필요합니다. 자세한 내용은 대상 패턴(인터페이스)을 참조하세요. session protocol sipv2이 다이얼 피어가 SIP 통화 연결을 처리함을 지정합니다. 자세한 내용은 세션 프로토콜(다이얼 피어)을 참조하세요. 세션 대상 IPv4: 192.168.80.14루프백을 위한 호출 대상으로 로컬 라우터 인터페이스 주소를 지정합니다. 자세한 내용은 세션 대상(voip 다이얼 피어)을 참조하세요. 바인드 제어 소스 인터페이스 GigabitEthernet0/0/0루프백을 통해 전송되는 메시지에 대한 소스 인터페이스 및 관련 IP 주소를 구성합니다. 자세한 내용은 bind를 참조하세요. 미디어 소스 인터페이스 바인딩 GigabitEthernet0/0/0루프백을 통해 전송되는 미디어에 대한 소스 인터페이스와 연결된 IP 주소를 구성합니다. 자세한 내용은 bind를 참조하세요. dtmf-relay rtp-nteRTP-NTE(RFC2833)를 통화 레그에서 기대하는 DTMF 기능으로 정의합니다. 자세한 내용은 DTMF 릴레이(VoIP)를 참조하세요. 코덱 g711alaw 모든 PSTN 통화에서 G.711 코덱을 사용하도록 강제합니다. 사용 중인 ISDN 서비스에서 사용하는 압축 방식에 맞춰 a-law 또는 u-law를 선택하십시오. no vad음성 활동 탐지를 비활성화합니다. 자세한 내용은 vad(다이얼 피어)를 참조하세요. |
| 5 |
다음 통화 라우팅 구성을 추가하십시오. 이로써 로컬 게이트웨이 구성이 완료되었습니다. CUBE 기능을 처음 구성하는 경우 구성을 저장하고 플랫폼을 다시 로드하십시오.
|
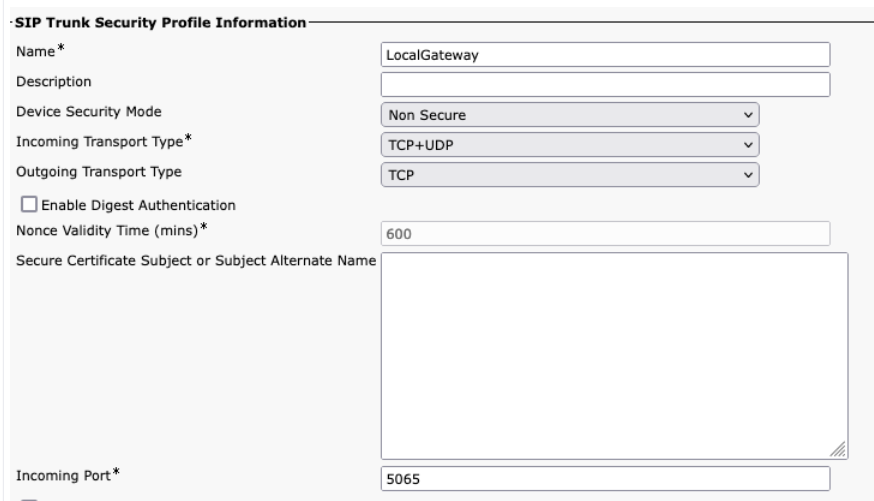
이전 섹션의 PSTN-Webex 통화 구성은 Cisco Unified Communications Manager(UCM) 클러스터에 대한 추가 트렁크를 포함하도록 수정할 수 있습니다. 이 경우 모든 통화는 Unified CM을 통해 연결됩니다. UCM에서 5060번 포트로 걸려오는 전화는 PSTN으로 연결되고, 5065번 포트로 걸려오는 전화는 Webex Calling으로 연결됩니다. 이 호출 시나리오를 포함하도록 다음과 같은 단계적 구성을 추가할 수 있습니다.
Unified CM에서 Webex 통화 트렁크를 생성할 때 SIP 트렁크 보안 프로필 설정에서 수신 포트를 5065로 구성해야 합니다. 이를 통해 5065번 포트로 들어오는 메시지를 허용하고, 로컬 게이트웨이로 메시지를 보낼 때 VIA 헤더에 해당 값을 채울 수 있습니다.
| 1 |
다음 음성 클래스 URI를 구성합니다. |
| 2 |
Unified CM 호스트에 대한 SRV 라우팅을 지정하려면 다음 DNS 레코드를 구성하십시오. IOS XE는 이러한 레코드를 사용하여 로컬에서 대상 UCM 호스트 및 포트를 결정합니다. 이 구성에서는 DNS 시스템에 레코드를 구성할 필요가 없습니다. DNS를 직접 사용하려는 경우 이러한 로컬 구성은 필요하지 않습니다. 구성에 대한 필드의 설명은 다음과 같습니다. 다음 명령은 DNS SRV 리소스 레코드를 생성합니다. 각 UCM 호스트 및 트렁크에 대한 레코드를 생성합니다. ip 호스트 _sip._udp.pstntocucm.io 서버 2 1 5060 ucmsub5.mydomain.com _sip._udp.pstntocucm.io: SRV 리소스 레코드 이름 2: SRV 리소스 레코드 우선순위 1: SRV 리소스 레코드 가중치 5060: 이 리소스 레코드에서 대상 호스트에 사용할 포트 번호입니다. ucmsub5.mydomain.com: 리소스 레코드 대상 호스트 리소스 레코드의 대상 호스트 이름을 확인하려면 로컬 DNS A 레코드를 생성해야 합니다. 예를 들면, IP 호스트 ucmsub5.mydomain.com 192.168.80.65 IP 호스트: 로컬 IOS XE 데이터베이스에 레코드를 생성합니다. ucmsub5.mydomain.com: A 레코드 호스트 이름입니다. 192.168.80.65: 호스트의 IP 주소입니다. UCM 환경 및 선호하는 통화 분배 전략을 반영하도록 SRV 리소스 레코드와 A 레코드를 생성하십시오. |
| 3 |
다음 다이얼 피어를 구성하십시오. |
| 4 |
다음 구성을 사용하여 통화 라우팅을 추가하세요. |
진단 서명(DS)은 IOS XE 기반 로컬 게이트웨이에서 일반적으로 관찰되는 문제를 사전적으로 탐지하고 이벤트의 이메일, 시스로그 또는 터미널 메시지 알림을 생성합니다. DS를 설치하면 진단 데이터 수집을 자동화하고 수집된 데이터를 Cisco TAC 케이스로 전송하여 문제 해결 시간을 단축할 수 있습니다.
진단 서명(DS)은 문제 발생에 대한 정보 및 문제를 알리고, 문제 해결 및 수정하기 위해 실행되는 작업에 대한 정보를 포함하는 XML 파일입니다. syslog 메시지, SNMP 이벤트 및 특정 show 명령 출력에 대한 주기적인 모니터링을 통해 문제 감지 로직을 정의할 수 있습니다.
작업 유형은 표시 명령어 출력 수집을 포함합니다. 다음:
-
통합 로그 파일 생성
-
사용자가 지정한 네트워크 위치(예: HTTPS, SCP, FTP 서버)에 파일을 업로드합니다.
TAC 엔지니어는 DS 파일을 작성하고 디지털로 서명하여 완전성을 보호합니다. 각 DS 파일에는 시스템이 지정한 고유한 숫자 ID가 있습니다. 진단 서명 조회 도구 (DSLT)는 다양한 문제를 모니터링하고 해결하기 위한 적용 가능한 서명을 찾을 수 있는 단일 소스입니다.
시작하기 전에:
-
DSLT에서 다운로드한 DS 파일을 편집 하지 않습니다. 완전성 검사 오류로 인해 수정한 파일 설치에 실패합니다.
-
로컬 게이트웨이가 이메일 알림을 발송하기 위해 필요한 간단한 메일 전송 프로토콜(SMTP) 서버입니다.
-
이메일 통지에 대해 보안 SMTP 서버를 사용하고자 하는 경우, 로컬 게이트웨이가 IOS XE 17.6.1 이상을 실행하고 있도록 합니다.
전제 조건
로컬 게이트웨이는 IOS XE 17.6.1a 이상 버전을 실행해야 합니다.
-
진단 서명은 기본적으로 활성화됩니다.
-
장치가 Cisco IOS XE 17.6.1a 이상 버전을 실행 중인 경우 사전 알림을 보내는 데 사용할 보안 이메일 서버를 구성하십시오.
configure terminal call-home mail-server :@ priority 1 secure tls end -
관리자의 이메일 주소를 환경 변수 ds_email 에 설정하여 알림을 받도록 하십시오.
configure terminal call-home diagnostic-signature environment ds_email end
다음은 Cisco IOS XE 17.6.1a 이상에서 실행되는 로컬 게이트웨이의 구성 예시로, 로 사전 알림을 전송하는 방법을 보여줍니다. tacfaststart@gmail.com Gmail을 보안 SMTP 서버로 사용:
Cisco IOS XE Bengaluru 17.6.x 이상 버전을 사용하시는 것을 권장합니다.
call-home
mail-server tacfaststart:password@smtp.gmail.com priority 1 secure tls
diagnostic-signature
environment ds_email "tacfaststart@gmail.com" Cisco IOS XE 소프트웨어에서 실행되는 로컬 게이트웨이는 OAuth를 지원하는 일반적인 웹 기반 Gmail 클라이언트가 아니기 때문에 특정 Gmail 계정 설정을 구성하고 장치에서 이메일을 올바르게 처리하려면 특정 권한을 제공해야 합니다.
-
을 켜고 보안 수준이 낮은 앱 액세스 설정을 활성화합니다.
-
Gmail에서 "Google이 아닌 앱을 사용하여 사용자의 계정에 로그인하는 것을 차단했습니다"라는 이메일을 수신하면 "예. 저도 그렇습니다"에 응답합니다.
사전 모니터링을 위해 진단 서명 설치
높은 CPU 이용 모니터링하기
이 DS는 SNMP OID를 사용하여 5초 동안 CPU 사용률을 추적합니다. 1.3.6.1.4.1.9.2.1.56. 사용률이 75% 이상이면 모든 디버그를 비활성화하고 로컬 게이트웨이에 설치된 모든 진단 서명을 제거합니다. 서명을 설치하려면 아래 단계를 따르십시오.
-
SNMP를 활성화하려면 show snmp 명령어를 사용하십시오. 활성화하지 않으면 snmp-server manager 명령을 구성하십시오.
show snmp %SNMP agent not enabled config t snmp-server manager end show snmp Chassis: ABCDEFGHIGK 149655 SNMP packets input 0 Bad SNMP version errors 1 Unknown community name 0 Illegal operation for community name supplied 0 Encoding errors 37763 Number of requested variables 2 Number of altered variables 34560 Get-request PDUs 138 Get-next PDUs 2 Set-request PDUs 0 Input queue packet drops (Maximum queue size 1000) 158277 SNMP packets output 0 Too big errors (Maximum packet size 1500) 20 No such name errors 0 Bad values errors 0 General errors 7998 Response PDUs 10280 Trap PDUs Packets currently in SNMP process input queue: 0 SNMP global trap: enabled -
다음과 같이 진단 서명 검색 도구에서 다음 드롭다운 옵션을 사용하여 DS 64224를 다운로드합니다.
필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Cisco CSR 1000V 시리즈
제품
Webex Calling 솔루션의 CUBE Enterprise
문제 범위
성능
문제 유형
이메일 알림에서 높은 CPU 이용.
-
DS XML 파일을 로컬 게이트웨이 플래시로 복사합니다.
LocalGateway# copy ftp://username:password@/DS_64224.xml bootflash:다음 예제는 FTP 서버에서 로컬 게이트웨이로 파일을 복사하는 방법을 보여줍니다.
copy ftp://user:pwd@192.0.2.12/DS_64224.xml bootflash: Accessing ftp://*:*@ 192.0.2.12/DS_64224.xml...! [OK - 3571/4096 bytes] 3571 bytes copied in 0.064 secs (55797 bytes/sec) -
로컬 게이트웨이에서 DS XML 파일을 설치합니다.
call-home diagnostic-signature load DS_64224.xml Load file DS_64224.xml success -
통화- 홈 진단 서명 표시 명령어를 사용하여 서명이 성공적으로 설치 있는지 확인합니다. 상태 열에는 "등록됨" 값이 표시되어야 합니다.
show call-home diagnostic-signature Current diagnostic-signature settings: Diagnostic-signature: enabled Profile: CiscoTAC-1 (status: ACTIVE) Downloading URL(s): https://tools.cisco.com/its/service/oddce/services/DDCEService Environment variable: ds_email: username@gmail.comDSes 다운로드:
DS ID
DS 이름
개정
상태
마지막 업데이트(GMT+00:00)
64224
DS_LGW_CPU_MON75
0.0.10
등록됨
2020-11-07 22:05:33
트리거되면 이 서명은 서명 자체를 포함하여 실행 중인 모든 DS를 제거합니다. 필요한 경우 DS 64224를 재설치하여 로컬 게이트웨이의 높은 CPU 사용률을 계속 모니터링하십시오.
SIP 트렁크 등록 모니터링하기
이 DS는 60초마다 SIP 트렁크 클라우드와 로컬 게이트웨이 Webex Calling 확인합니다. 등록 해제 이벤트가 감지되면 이메일 및 시스템 로그 알림이 생성되고, 두 번의 등록 해제 발생 후 자동으로 제거됩니다. 서명을 설치하려면 아래 단계를 따르십시오.
-
다음과 같이 진단 서명 검색 도구에서 다음 드롭다운 옵션을 사용하여 DS 64117를 다운로드합니다.
필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Cisco CSR 1000V 시리즈
제품
Webex Calling 솔루션의 CUBE Enterprise
문제 범위
SIP-SIP
문제 유형
SIP 트렁크 알림에 대한 등록을 변경하지 않습니다.
-
DS XML 파일을 로컬 게이트웨이로 복사합니다.
copy ftp://username:password@/DS_64117.xml bootflash: -
로컬 게이트웨이에서 DS XML 파일을 설치합니다.
call-home diagnostic-signature load DS_64117.xml Load file DS_64117.xml success LocalGateway# -
통화- 홈 진단 서명 표시 명령어를 사용하여 서명이 성공적으로 설치 있는지 확인합니다. 상태 열에는 "등록된" 값이 있어야 합니다.
비정상적인 통화 연결 끊기 모니터링 중
이 DS는 10분마다 SNMP 폴링을 사용하여 SIP 오류 403, 488 및 503으로 인한 비정상적인 통화 끊김을 감지합니다. 마지막 폴링 이후 오류 횟수 증가가 5 이상이면 시스템 로그와 이메일 알림을 생성합니다. 아래 단계를 따라 서명을 설치하십시오.
-
SNMP가 활성화되어 있는지 확인하려면 ` show snmp` 명령어를 사용하십시오. 활성화되어 있지 않은 경우 snmp-server manager 명령을 구성하십시오.
show snmp %SNMP agent not enabled config t snmp-server manager end show snmp Chassis: ABCDEFGHIGK 149655 SNMP packets input 0 Bad SNMP version errors 1 Unknown community name 0 Illegal operation for community name supplied 0 Encoding errors 37763 Number of requested variables 2 Number of altered variables 34560 Get-request PDUs 138 Get-next PDUs 2 Set-request PDUs 0 Input queue packet drops (Maximum queue size 1000) 158277 SNMP packets output 0 Too big errors (Maximum packet size 1500) 20 No such name errors 0 Bad values errors 0 General errors 7998 Response PDUs 10280 Trap PDUs Packets currently in SNMP process input queue: 0 SNMP global trap: enabled -
진단 서명 검색 도구에서 다음 옵션을 사용하여 DS 65221을 다운로드합니다.
필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Cisco CSR 1000V 시리즈
제품
Webex Calling 솔루션의 CUBE Enterprise
문제 범위
성능
문제 유형
이메일 및 시스로그 알림에서 SIP 비정상적인 통화 연결 끊기 탐지.
-
DS XML 파일을 로컬 게이트웨이로 복사합니다.
copy ftp://username:password@/DS_65221.xml bootflash: -
로컬 게이트웨이에서 DS XML 파일을 설치합니다.
call-home diagnostic-signature load DS_65221.xml Load file DS_65221.xml success -
통화- 홈 진단 서명 표시 명령어를 사용하여 서명이 성공적으로 설치 있는지 확인합니다. 상태 열에는 "등록된" 값이 있어야 합니다.
진단 서명을 설치하여 문제를 해결
진단 서명(DS)을 사용하여 빠르게 문제를 해결합니다. Cisco TAC 엔지니어는 주어진 문제를 해결하기 위해 필요한 디버그를 활성화하고, 문제점 발생 탐지, 진단 데이터의 올바른 집합을 수집, Cisco TAC 사례로 데이터를 자동으로 전송하는 다양한 서명을 생성했습니다. 진단 시그니처(DS)를 사용하면 문제 발생 여부를 수동으로 확인할 필요가 없어지고, 간헐적이거나 일시적인 문제에 대한 문제 해결이 훨씬 쉬워집니다.
진단 서명 찾기 도구를 사용하여 해당하는 서명을 찾고 설치하여 주어진 문제를 자체 해결하거나, TAC 엔지니어가 지원 참여의 일부로 권장하는 서명을 설치할 수 있습니다.
다음 항목을 탐지하기 위해 DS를 찾고 설치하는 방법의 예제는 다음과 같습니다. “%VOICE_IEC-3-GW: CCAPI: 내부 오류 (통화 spike 임계값): IEC=1.1.181.1.29.0" 시스로그 및 다음 단계를 사용하여 진단 데이터 수집을 자동화합니다.
-
수집된 진단 데이터가 업로드될 Cisco TAC 파일 서버 경로(cxd.cisco.com)를 추가 DS 환경 ds_fsurl_prefix변수 로 구성하십시오. 파일 경로의 사용자 이름은 케이스 번호이고 암호는 파일 업로드 토큰입니다. 파일 업로드 토큰은 다음 명령을 사용하여 지원 케이스 관리자에서 가져올 수 있습니다. 필요에 따라 지원 케이스 관리자의 첨부 파일 섹션에서 파일 업로드 토큰 을 생성할 수 있습니다.
configure terminal call-home diagnostic-signature LocalGateway(cfg-call-home-diag-sign)environment ds_fsurl_prefix "scp://:@cxd.cisco.com" end예:
call-home diagnostic-signature environment ds_fsurl_prefix " environment ds_fsurl_prefix "scp://612345678:abcdefghijklmnop@cxd.cisco.com" -
show snmp 명령어를 사용하여 SNMP가 활성화되어 있는지 확인하십시오. 활성화되어 있지 않은 경우 snmp-server manager 명령을 구성하십시오.
show snmp %SNMP agent not enabled config t snmp-server manager end -
높은 CPU 모니터링 DS 64224를 사전 대책으로 설치하여 높은 CPU 사용률 동안 모든 디버그 및 진단 서명을 비활성화합니다. 진단 서명 검색 도구에서 다음 옵션을 사용하여 DS 64224을 다운로드합니다.
필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Cisco CSR 1000V 시리즈
제품
Webex Calling 솔루션의 CUBE Enterprise
문제 범위
성능
문제 유형
이메일 알림에서 높은 CPU 이용.
-
진단 서명 검색 도구에서 다음 옵션을 사용하여 DS 65095을 다운로드합니다.
필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Cisco CSR 1000V 시리즈
제품
Webex Calling 솔루션의 CUBE Enterprise
문제 범위
시스로그
문제 유형
Syslog - %VOICE_IEC-3-GW: CCAPI: 내부 오류 (통화 spike 임계값): IEC=1.1.181.1.29.0
-
DS XML 파일을 로컬 게이트웨이에 복사합니다.
copy ftp://username:password@/DS_64224.xml bootflash: copy ftp://username:password@/DS_65095.xml bootflash: -
높은 CPU 모니터링 DS 64224를 설치한 후 로컬 게이트웨이에 DS 65095 XML 파일을 설치합니다.
call-home diagnostic-signature load DS_64224.xml Load file DS_64224.xml success call-home diagnostic-signature load DS_65095.xml Load file DS_65095.xml success -
show call-home diagnostic-signature 명령어를 사용하여 서명이 성공적으로 설치되었는지 확인하십시오. 상태 열에는 "등록된" 값이 있어야 합니다.
show call-home diagnostic-signature Current diagnostic-signature settings: Diagnostic-signature: enabled Profile: CiscoTAC-1 (status: ACTIVE) Downloading URL(s): https://tools.cisco.com/its/service/oddce/services/DDCEService Environment variable: ds_email: username@gmail.com ds_fsurl_prefix: scp://612345678:abcdefghijklmnop@cxd.cisco.com다운로드된 DSes:
DS ID
DS 이름
개정
상태
마지막 업데이트(GMT+00:00)
64224
00:07:45
DS_LGW_CPU_MON75
0.0.10
등록됨
2020-11-08
65095
00:12:53
DS_LGW_IEC_Call_spike_threshold
0.0.12
등록됨
2020-11-08
진단 서명 실행 확인
다음 명령에서 로컬 게이트웨이가 서명 내에 정의된 작업을 실행하는 동안 show call-home diagnostic-signature 명령의 "상태" 열이 "실행 중"으로 변경됩니다. 통화-홈 진단 서명 통계 표시의 출력은 진단 서명이 관심 있는 이벤트를 탐지하고 해당 작업을 실행하는지 확인하는 최선의 방법입니다. "트리거(Triggered/Max/Deinstall) 열은 부여된 서명이 이벤트를 트리거한 횟수, 이벤트를 탐지하기 위해 정의된 최대 횟수 및 최대 트리거된 이벤트의 수를 탐지한 후 서명이 자동으로 제거되는지 여부를 나타냅니다.
show call-home diagnostic-signature
Current diagnostic-signature settings:
Diagnostic-signature: enabled
Profile: CiscoTAC-1 (status: ACTIVE)
Downloading URL(s): https://tools.cisco.com/its/service/oddce/services/DDCEService
Environment variable:
ds_email: carunach@cisco.com
ds_fsurl_prefix: scp://612345678:abcdefghijklmnop@cxd.cisco.com 다운로드된 DSes:
|
DS ID |
DS 이름 |
개정 |
상태 |
마지막 업데이트(GMT+00:00) |
|---|---|---|---|---|
| 64224 |
DS_LGW_CPU_MON75 |
0.0.10 |
등록됨 |
2020-11-08 00:07:45 |
|
65095 |
DS_LGW_IEC_Call_spike_threshold |
0.0.12 |
실행 중 |
2020-11-08 00:12:53 |
통화 홈 진단 서명 통계 표시
|
DS ID |
DS 이름 |
트리거됨/Max/Deinstall |
평균 실행 시간(초) |
최대 실행 시간(초) |
|---|---|---|---|---|
| 64224 |
DS_LGW_CPU_MON75 |
0/0/N |
0.000 |
0.000 |
|
65095 |
DS_LGW_IEC_Call_spike_threshold |
1/20/Y |
23.053 |
23.053 |
진단 알림 이메일 실행 중에 발송되는 관리 장치에는 문제 유형, 장치 세부 사항, 소프트웨어 버전, 실행 중인 구성 및 해당 문제와 관련된 명령어 출력을 표시하는 등의 주요 정보가 포함되어 있습니다.
진단 서명 제거
문제 해결을 위해 진단 서명 사용은 일반적으로 일부 문제점을 탐지한 후에 제거하기로 정의됩니다. 서명을 수동으로 제거하려면 show call-home diagnostic-signature 명령의 출력에서 DS ID를 가져온 다음 다음 명령을 실행하십시오.
call-home diagnostic-signature deinstall
예:
call-home diagnostic-signature deinstall 64224
배포에서 일반적으로 관찰되는 문제에 기반하여 새로운 서명은 진단 서명 검색 도구에 주기적으로 추가됩니다. 현재 TAC는 새 사용자 정의 서명을 만드는 요청을 지원하지 않습니다.
Cisco IOS XE 게이트웨이를 보다 효율적으로 관리하려면 Control Hub를 통해 게이트웨이를 등록하고 관리하는 것이 좋습니다. 이는 선택 사항 구성입니다. 등록 후에는 제어 허브의 구성 유효성 검사 옵션을 사용하여 로컬 게이트웨이 구성을 검증하고 구성 문제를 식별할 수 있습니다. 현재로서는 등록 기반 트렁크에서만 이 기능을 지원합니다.
더 자세한 내용은 다음을 참조하십시오.
이 섹션에서는 인증서 기반 상호 TLS(mTLS) SIP 트렁크를 사용하여 Cisco Unified Border Element(CUBE)를 Webex 통화용 로컬 게이트웨이로 구성하는 방법을 설명합니다. 이 문서의 첫 번째 부분에서는 간단한 PSTN 게이트웨이를 구성하는 방법을 설명합니다. 이 경우, PSTN에서 걸려오는 모든 통화는 Webex Calling으로 연결되고, Webex Calling에서 걸려오는 모든 통화는 PSTN으로 연결됩니다. 다음 이미지는 이 솔루션과 향후 적용될 상위 수준 통화 라우팅 구성을 보여줍니다.
이 설계에서는 다음과 같은 주요 구성이 사용됩니다.
-
음성 클래스 테넌트: Used 트렁크별 구성을 생성하기 위해.
-
음성 클래스 uri: 수신 다이얼 피어 선택을 위해 SIP 메시지를 분류하는 데 사용됩니다.
-
인바운드 다이얼 피어: 수신 SIP 메시지를 처리하고 다이얼 피어 그룹을 사용하여 발신 경로를 결정합니다.
-
다이얼 피어 그룹: 통화 연결 라우팅에 사용되는 발신 다이얼 피어를 정의합니다.
-
아웃바운드 다이얼 피어: 발신 SIP 메시지를 처리하고 필요한 대상으로 라우팅합니다.

온프레미스 Cisco Unified Communications Manager 솔루션을 Webex Calling에 연결할 때, 다음 다이어그램에 나와 있는 솔루션을 구축하기 위한 기본 구성으로 간단한 PSTN 게이트웨이 구성을 사용할 수 있습니다. 이 경우 통합 커뮤니케이션 관리자는 모든 PSTN 및 Webex 통화에 대한 중앙 집중식 라우팅 및 처리를 제공합니다.

이 문서 전체에서 다음 이미지에 표시된 호스트 이름, IP 주소 및 인터페이스가 사용됩니다. 공용 또는 사설(NAT 뒤) 주소 지정 옵션이 제공됩니다. SRV DNS 레코드는 여러 CUBE 인스턴스에 걸쳐 로드 밸런싱을 수행하는 경우가 아니면 선택 사항입니다.
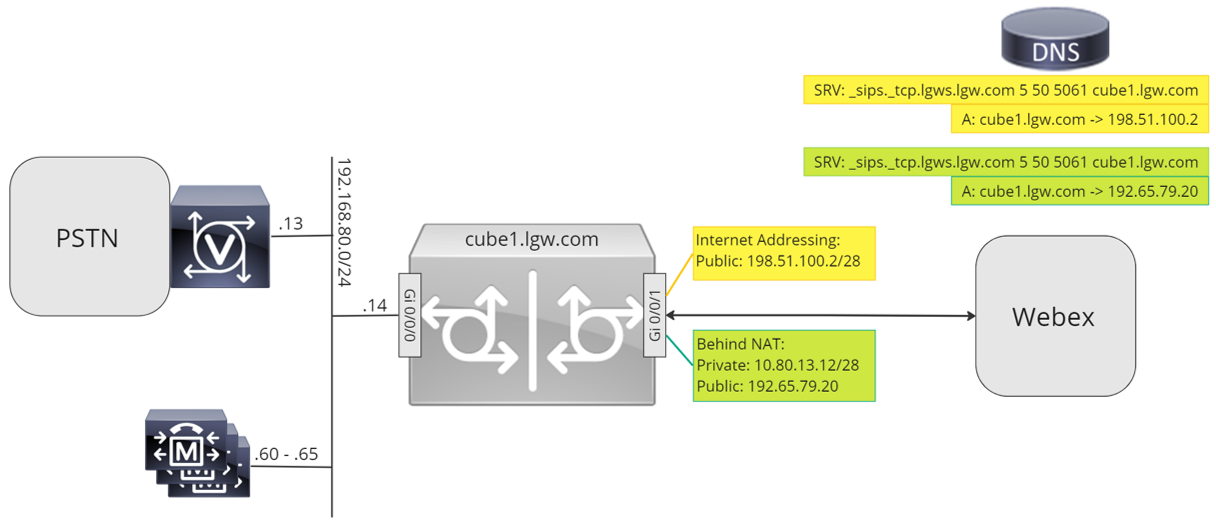
이 문서의 나머지 부분에 있는 구성 지침을 사용하여 다음과 같이 로컬 게이트웨이 구성을 완료하십시오.
기본 구성
Cisco 라우터를 Webex 통화용 로컬 게이트웨이로 준비하는 첫 번째 단계는 플랫폼을 보호하고 연결을 설정하는 기본 구성을 구축하는 것입니다.
-
인증서 기반 로컬 게이트웨이 구축에는 Cisco IOS XE 17.9.1a 이상 버전이 필요합니다. Cisco IOS XE 17.12.2 이상 버전을 권장합니다. 권장 버전에 대해서는 Cisco 소프트웨어 연구 페이지를 참조하십시오. 플랫폼을 검색하고 개의 제안된 릴리스 중 하나를 선택하십시오.
-
ISR4000 시리즈 라우터는 통합 커뮤니케이션 및 보안 기술 라이선스를 모두 구성해야 합니다.
-
음성 카드 또는 DSP가 장착된 Catalyst Edge 8000 시리즈 라우터에는 DNA Advantage 라이선스가 필요합니다. 음성 카드나 DSP가 없는 라우터는 최소한 DNA Essentials 라이선스가 필요합니다.
-
대용량 처리가 필요한 경우, 고보안(HSEC) 라이선스와 추가 처리량 권한이 필요할 수 있습니다.
자세한 내용은 인증 코드 를 참조하십시오.
-
-
회사 정책에 부합하는 플랫폼 기본 구성을 구축하세요. 특히 다음 사항을 구성하고 확인하십시오.
-
NTP
-
Acl
-
사용자 인증 및 원격 액세스
-
DNS
-
IP 라우팅
-
IP 주소
-
-
Webex 통화로 향하는 네트워크는 IPv4 주소를 사용해야 합니다. 컨트롤 허브에 구성된 로컬 게이트웨이의 정규화된 도메인 이름(FQDN) 또는 서비스 레코드(SRV) 주소는 인터넷상의 공용 IPv4 주소로 확인되어야 합니다.
-
Webex에 연결된 로컬 게이트웨이 인터페이스의 모든 SIP 및 미디어 포트는 인터넷에서 직접 또는 정적 NAT를 통해 액세스할 수 있어야 합니다. 방화벽을 적절히 업데이트했는지 확인하십시오.
-
로컬 게이트웨이에 서명된 인증서를 설치하려면 아래에 제공된 자세한 구성 단계를 따르십시오.
-
Cisco Webex 오디오 및 비디오 플랫폼 통화에 지원되는 루트 인증 기관은 무엇입니까? 에 자세히 설명된 대로 공용 인증 기관(CA)이 장치 인증서에 서명해야 합니다.
-
인증서 주체 일반 이름(CN) 또는 주체 대체 이름(SAN) 중 하나는 제어 허브에 구성된 FQDN과 동일해야 합니다. 예를 들면,
-
조직의 컨트롤 허브에 구성된 트렁크에 다음과 같은 문제가 있는 경우 cube1.lgw.com:5061 로컬 게이트웨이의 FQDN으로 사용하려면 라우터 인증서의 CN 또는 SAN에 cube1.lgw.com이 포함되어야 합니다.
-
조직의 제어 허브에 구성된 트렁크에서 해당 트렁크를 통해 접근 가능한 로컬 게이트웨이의 SRV 주소가 lgws.lgw.com인 경우, 라우터 인증서의 CN 또는 SAN에도 lgws.lgw.com이 포함되어야 합니다. SAN에서 SRV 주소(CNAME, A 레코드 또는 IP 주소)를 확인한 레코드는 선택 사항입니다.
-
트렁크에 FQDN을 사용하든 SRV를 사용하든 관계없이 로컬 게이트웨이에서 전송되는 모든 새 SIP 대화의 연락처 주소는 컨트롤 허브에 구성된 이름을 사용해야 합니다.
-
-
클라이언트와 서버 모두에서 사용할 수 있도록 인증서에 서명이 되어 있는지 확인하십시오.
-
-
Cisco 루트 CA 번들을 로컬 게이트웨이에 업로드하십시오. 이 패키지에는 Webex 플랫폼 인증에 사용되는 CA 루트 인증서가 포함되어 있습니다.
구성
| 1 |
예를 들어, 모든 레이어 3 인터페이스에 유효하고 라우팅 가능한 IP 주소를 할당해야 합니다.
|
| 2 |
라우터에서 STUN 자격 증명을 대칭 암호화를 사용하여 보호하십시오. 기본 암호화 키와 암호화 유형을 다음과 같이 구성하십시오. |
| 3 |
지원되는 인증 기관(CA)에서 서명한 도메인용 인증서를 사용하여 암호화 트러스트포인트를 생성합니다. |
| 4 |
호스트 인증서를 인증하기 위해 중간 서명 CA의 인증서를 제공하십시오. 다음 실행 또는 구성 명령을 입력하십시오.
|
| 5 |
다음 실행 명령 또는 구성 명령을 사용하여 서명된 호스트 인증서를 가져옵니다.
|
| 6 |
다음 구성 명령을 사용하여 TLS 1.2 독점성을 활성화하고 음성 애플리케이션에 사용할 기본 트러스트포인트를 지정하십시오.
|
| 7 |
Webex 통화에서 사용하는 IdenTrust 상용 루트 CA 1 인증서가 포함된 Cisco 루트 CA 번들을 설치하십시오. crypto pki trustpool import clean url url 명령어를 사용하여 지정된 URL에서 루트 CA 번들을 다운로드하고 현재 CA 트러스트풀을 지운 다음 새 인증서 번들을 설치하십시오. HTTPS를 사용하여 인터넷에 접속하기 위해 프록시를 사용해야 하는 경우, CA 번들을 가져오기 전에 다음 구성을 추가하십시오. ip http 클라이언트 프록시 서버 yourproxy.com 프록시 포트 80 |
| 1 |
컨트롤 허브에서 기존 위치에 대한 CUBE 인증서 기반 PSTN 트렁크를 생성합니다. 자세한 내용은 Webex 통화용 트렁크, 라우트 그룹 및 다이얼 플랜 구성을 참조하세요. 트렁크를 생성할 때 트렁크 정보를 기록해 두세요. 다음 그림에서 강조 표시된 이러한 세부 정보는 이 가이드의 구성 단계에서 사용됩니다. 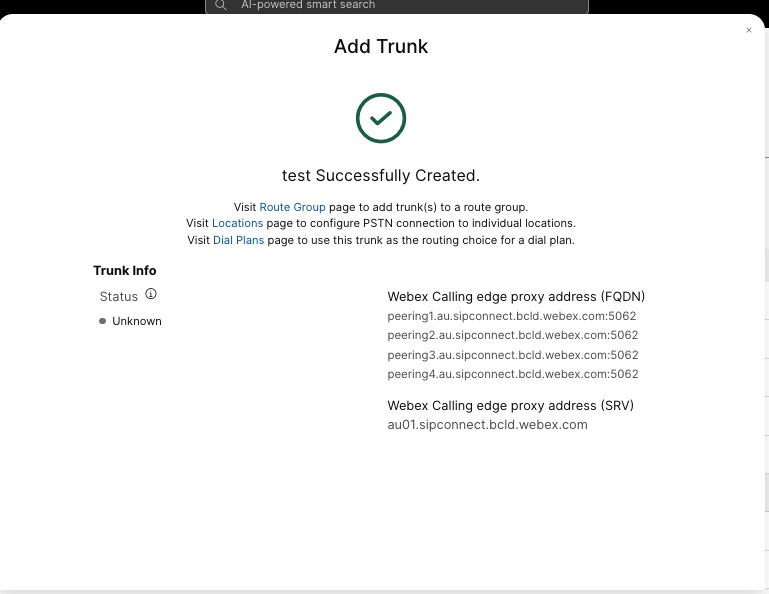 |
| 2 |
CUBE를 Webex 통화 로컬 게이트웨이로 구성하려면 다음 명령어를 입력하십시오. 구성에 대한 필드의 설명은 다음과 같습니다.
이 기능을 통해 플랫폼에서 Cisco Unified Border Element(CUBE) 기능을 활성화할 수 있습니다. allow-connections sip to sipCUBE 기본 SIP 백투백 사용자 에이전트 기능을 활성화합니다. 자세한 내용은 연결 허용을 참조하세요. 기본적으로 T.38 팩스 전송이 활성화되어 있습니다. 자세한 내용은 팩스 프로토콜 t38(음성 서비스)을 참조하십시오. STUN(NAT를 통한 UDP 세션 트래버스)을 전역적으로 활성화합니다. 이러한 전역 STUN 명령은 로컬 게이트웨이를 NAT 뒤에 배포할 때만 필요합니다.
자세한 내용은 stun flowdata agent-id및 stun flowdata shared-secret를 참조하십시오. 비대칭 페이로드 전체DTMF 및 동적 코덱 페이로드 모두에 대해 SIP 비대칭 페이로드 지원을 구성합니다. 이 명령에 대한 자세한 내용은 비대칭 페이로드를 참조하십시오. early-offer forced로컬 게이트웨이가 인접 피어로부터 승인을 기다리는 대신 초기 INVITE 메시지에 SDP 정보를 전송하도록 강제합니다. 이 명령에 대한 자세한 내용은 early-offer를 참조하십시오. sip-profiles 인바운드CUBE가 SIP 프로필을 사용하여 메시지를 수신하는 즉시 수정할 수 있도록 합니다. 프로필은 다이얼 피어 또는 테넌트를 통해 적용됩니다. |
| 3 |
음성 클래스 코덱 100 을 구성하여 모든 트렁크에 대해 G.711 코덱만 허용합니다. 이러한 간단한 접근 방식은 대부분의 배포 환경에 적합합니다. 필요한 경우, 송신 시스템과 수신 시스템 모두에서 지원하는 추가 코덱 유형을 목록에 추가하십시오. DSP 모듈을 사용한 트랜스코딩 을 포함하는 더 복잡한 솔루션도 지원되지만 이 가이드에는 포함되어 있지 않습니다. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 코덱 100SIP 트렁크 통화에 대해 선호하는 코덱만 허용하도록 설정하는 데 사용됩니다. 자세한 내용은 음성 클래스 코덱을 참조하세요. |
| 4 |
Webex 통화 트렁크에서 ICE를 활성화하려면 voice class stun-usage 100 을 구성하십시오. (이 단계는 Webex for Government에는 적용되지 않습니다.) 구성에 대한 필드의 설명은 다음과 같습니다. 기절 사용 얼음 빛Webex 통화에 연결된 모든 다이얼 피어에 ICE-Lite를 활성화하여 가능한 경우 미디어 최적화를 허용하는 데 사용됩니다. 자세한 내용은 음성 클래스 기절 사용법 및 기절 사용법 아이스 라이트를 참조하세요. stun usage firewall-traversal flowdata명령은 로컬 게이트웨이를 NAT 뒤에 배포할 때만 필요합니다. 미디어 최적화는 가능한 경우 협상을 통해 이루어집니다. 통화에 녹음과 같은 클라우드 미디어 서비스가 필요한 경우, 해당 미디어를 최적화할 수 없습니다. |
| 5 |
Webex 트래픽에 대한 미디어 암호화 정책을 구성합니다. (이 단계는 Webex for Government에는 적용되지 않습니다.) 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 srtp-crypto 100오퍼 및 응답 메시지에서 CUBE가 SDP에서 제공하는 유일한 SRTP 암호화 스위트로 SHA1_80을 지정합니다. Webex 통화는 SHA1_80만 지원합니다. 자세한 내용은 음성 클래스 srtp-crypto를 참조하세요. |
| 6 |
FIPS 규격 GCM 암호화를 구성합니다. (이 단계는 Webex for Government에만 적용됩니다.). 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 srtp-crypto 100CUBE에서 제공하는 암호화 스위트로 GCM을 지정합니다. 정부용 Webex의 로컬 게이트웨이에 GCM 암호화 방식을 설정하는 것은 필수입니다. |
| 7 |
대상 FQDN 또는 SRV를 기반으로 로컬 게이트웨이 트렁크로 들어오는 통화를 고유하게 식별하도록 패턴을 구성합니다. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 uri 100 sip수신되는 SIP 초대를 수신되는 트렁크 다이얼 피어와 일치시키는 패턴을 정의합니다. 이 패턴을 입력할 때는 컨트롤 허브에 트렁크에 대해 구성된 트렁크 FQDN 또는 SRV를 사용하십시오. 인증서 기반 트렁크를 구성할 때 로컬 게이트웨이에서 SRV 기반 Webex 통화 에지 주소를 사용하십시오. |
| 8 |
SIP 메시지 조작 프로필을 구성합니다. 게이트웨이가 공용 IP 주소로 구성된 경우 다음과 같이 프로필을 구성하거나 NAT를 사용하는 경우 다음 단계로 건너뛰십시오. 이 예시에서 cube1.lgw.com은 로컬 게이트웨이에 대해 구성된 FQDN입니다. 구성에 대한 필드의 설명은 다음과 같습니다. 규칙 10과 20Webex가 로컬 게이트웨이에서 전송되는 메시지를 인증할 수 있도록 하려면 SIP 요청 및 응답 메시지의 'Contact' 헤더에 Control Hub의 트렁크에 대해 프로비저닝된 값이 포함되어 있어야 합니다. 이는 단일 호스트의 FQDN이거나 장치 클러스터에 사용되는 SRV 이름일 수 있습니다. |
| 9 |
게이트웨이가 정적 NAT 뒤에 있는 사설 IP 주소로 구성된 경우, 다음과 같이 인바운드 및 아웃바운드 SIP 프로필을 구성하십시오. 이 예에서 cube1.lgw.com은 로컬 게이트웨이에 대해 구성된 FQDN이고, "10.80.13.12"는 Webex 통화에 사용되는 인터페이스 IP 주소이며, "192.65.79.20"은 NAT 공용 IP 주소입니다. Webex 통화로 발신하는 메시지용 SIP 프로필
구성에 대한 필드의 설명은 다음과 같습니다. 규칙 10과 20Webex가 로컬 게이트웨이에서 전송된 메시지를 인증할 수 있도록 하려면 SIP 요청 및 응답 메시지의 'Contact' 헤더에 Control Hub의 트렁크에 대해 프로비저닝된 값이 포함되어 있어야 합니다. 이는 단일 호스트의 FQDN이거나 장치 클러스터에 사용되는 SRV 이름일 수 있습니다. 규칙 30~81개인 주소 참조를 사이트의 외부 공용 주소로 변환하여 Webex가 후속 메시지를 올바르게 해석하고 라우팅할 수 있도록 합니다. Webex 통화에서 수신되는 메시지용 SIP 프로필구성에 대한 필드의 설명은 다음과 같습니다. 규칙 10~80공용 주소 참조를 구성된 개인 주소로 변환하여 CUBE가 Webex의 메시지를 처리할 수 있도록 합니다. 자세한 내용은 음성 클래스 sip-profiles를 참조하세요. 미국 또는 캐나다 PSTN 제공업체는 Webex 통화의 스팸 또는 사기 통화 표시 문서에 언급된 추가 구성을 통해 스팸 및 사기 통화에 대한 발신자 ID 확인을 제공할 수 있습니다. |
| 10 |
헤더 수정 프로필을 사용하여 SIP 옵션 유지(keepalive)를 구성합니다.
|
| 11 |
Webex 통화 트렁크 구성: |
위에서 설명한 대로 Webex 통화용 트렁크를 구축한 후, 다음 구성을 사용하여 SIP 기반 PSTN 공급자를 향한 암호화되지 않은 트렁크를 생성하십시오.
서비스 제공업체에서 보안 PSTN 회선을 제공하는 경우, 위에서 설명한 Webex 통화 회선 구성과 유사한 방식으로 구성할 수 있습니다. CUBE는 안전한 통화 라우팅을 지원합니다.
TDM을 사용하고 있다면 / ISDN PSTN 트렁크, 다음 섹션으로 건너뛰기 TDM PSTN 트렁크를 사용한 로컬 게이트웨이 구성.
Cisco TDM-SIP 게이트웨이에서 PSTN 통화 구간용 TDM 인터페이스를 구성하려면 ISDN PRI 구성을 참조하십시오.
| 1 |
PSTN 회선에서 걸려오는 수신 전화를 식별하려면 다음 음성 클래스 URI를 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 클래스 uri 200 sip수신되는 SIP 초대를 수신되는 트렁크 다이얼 피어와 일치시키는 패턴을 정의합니다. 이 패턴을 입력할 때는 IP PSTN 게이트웨이의 IP 주소를 사용하십시오. 자세한 내용은 음성 클래스 uri를 참조하세요. |
| 2 |
다음 IP PSTN 다이얼 피어를 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 태그가 200 인 VoIP 다이얼 피어를 정의하고 관리 및 문제 해결을 용이하게 하기 위해 의미 있는 설명을 제공합니다. 자세한 내용은 다이얼 피어 음성을 참조하십시오. 목적지 패턴 BAD.BAD수신 다이얼 피어 그룹을 사용하여 발신 통화를 라우팅할 때는 더미 대상 패턴이 필요합니다. 이 경우에는 유효한 목적지 패턴이라면 무엇이든 사용할 수 있습니다. 자세한 내용은 대상 패턴(인터페이스)을 참조하세요. session protocol sipv2이 다이얼 피어가 SIP 통화 연결을 처리함을 지정합니다. 자세한 내용은 세션 프로토콜(다이얼 피어)을 참조하세요. 세션 대상 IPv4: 192.168.80.13PSTN 제공업체로 전송되는 통화의 대상 주소를 지정합니다. 이는 IP 주소 또는 DNS 호스트 이름일 수 있습니다. 자세한 내용은 세션 대상(VoIP 다이얼 피어)을 참조하세요. 수신 URI 경유 200INVITE VIA 헤더 URI를 사용하여 수신 전화를 이 다이얼 피어와 일치시키는 데 사용되는 음성 클래스를 지정합니다. 자세한 내용은 수신 URL을 참조하세요. 음성 클래스 sip 주장된 ID pai
(선택 사항) P-Asserted-Identity 헤더 처리를 활성화하고 PSTN 트렁크에 이 헤더가 사용되는 방식을 제어합니다. 이 명령을 사용하면 수신 다이얼 피어에서 제공하는 발신자 ID가 발신 From 및 P-Asserted-Identity 헤더에 사용됩니다. 이 명령을 사용하지 않으면 수신 다이얼 피어에서 제공하는 발신자 ID가 발신 From 및 Remote-Party-ID 헤더에 사용됩니다. 자세한 내용은 voice-class sip asserted-id를 참조하세요. 바인드 제어 소스 인터페이스 GigabitEthernet0/0/0
PSTN으로 전송되는 메시지에 대한 소스 인터페이스와 연결된 IP 주소를 구성합니다. 자세한 내용은 bind를 참조하세요. 미디어 소스 인터페이스 바인딩 GigabitEthernet0/0/0PSTN으로 전송되는 미디어의 소스 인터페이스와 연결된 IP 주소를 구성합니다. 자세한 내용은 bind를 참조하세요. 음성 클래스 코덱 100다이얼 피어가 공통 코덱 필터 목록 100을 사용하도록 구성합니다. 자세한 내용은 음성 클래스 코덱을 참조하세요. dtmf-relay rtp-nteRTP-NTE(RFC2833)를 통화 레그에서 기대하는 DTMF 기능으로 정의합니다. 자세한 내용은 DTMF 릴레이(VoIP)를 참조하세요. no vad음성 활동 탐지를 비활성화합니다. 자세한 내용은 vad(다이얼 피어)를 참조하세요. |
| 3 |
Webex Calling과 PSTN 간의 통화만 라우팅하도록 로컬 게이트웨이를 구성하는 경우 다음 통화 라우팅 구성을 추가하십시오. 통합 커뮤니케이션 관리자 플랫폼을 사용하여 로컬 게이트웨이를 구성하는 경우 다음 섹션으로 건너뛰십시오. |
Webex 통화용 트렁크를 구축한 후, 다음 구성을 사용하여 루프백 통화 라우팅이 포함된 PSTN 서비스용 TDM 트렁크를 생성하면 Webex 통화 구간에서 미디어 최적화가 가능해집니다.
IP 미디어 최적화가 필요하지 않은 경우 SIP PSTN 트렁크 구성 단계를 따르십시오. PSTN VoIP 다이얼 피어 대신 음성 포트와 POTS 다이얼 피어를 사용하십시오(2단계 및 3단계 참조).
| 1 |
루프백 다이얼 피어 구성은 다이얼 피어 그룹과 통화 라우팅 태그를 사용하여 통화 라우팅 루프를 생성하지 않고 Webex와 PSTN 간에 통화가 올바르게 전달되도록 합니다. 통화 라우팅 태그를 추가 및 제거하는 데 사용될 다음 변환 규칙을 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 음성 번역 규칙규칙에 정의된 정규 표현식을 사용하여 통화 라우팅 태그를 추가하거나 제거합니다. 10진수 이상의 숫자('A')는 문제 해결을 위해 명확성을 높이는 데 사용됩니다. 이 구성에서는 translation-profile 100에 의해 추가된 태그가 Webex Calling에서 루프백 다이얼 피어를 통해 PSTN으로 통화를 연결하는 데 사용됩니다. 마찬가지로, translation-profile 200에 의해 추가된 태그는 PSTN에서 Webex 통화로의 통화 연결을 안내하는 데 사용됩니다. 번역 프로필 11과 12는 각각 Webex 및 PSTN 회선으로 통화를 전달하기 전에 이러한 태그를 제거합니다. 이 예시에서는 Webex 통화에서 걸려온 번호가 다음과 같이 표시된다고 가정합니다. +E.164 체재. 규칙 100은 선행을 제거합니다. + 유효한 발신 번호를 유지하기 위해. 규칙 12는 태그를 제거할 때 국가 또는 국제 라우팅 번호를 추가합니다. 해당 지역의 ISDN 국가 다이얼링 플랜에 맞는 숫자를 사용하십시오. Webex 통화에서 전화번호가 국가 번호 형식으로 표시되는 경우, 규칙 100과 12를 수정하여 각각 라우팅 태그를 추가하고 제거하십시오. |
| 2 |
트렁크 유형 및 사용 프로토콜에 따라 TDM 음성 인터페이스 포트를 필요에 맞게 구성하십시오. 자세한 내용은 ISDN PRI 구성을 참조하세요. 예를 들어, 장치의 NIM 슬롯 2에 설치된 기본 속도 ISDN 인터페이스의 기본 구성은 다음과 같을 수 있습니다. |
| 3 |
다음과 같은 TDM PSTN 다이얼 피어를 구성하십시오. 구성에 대한 필드의 설명은 다음과 같습니다. 태그가 200인 VoIP 다이얼 피어를 정의하고 관리 및 문제 해결을 용이하게 하기 위해 의미 있는 설명을 제공합니다. 자세한 내용은 dial-peer voice를 참조하세요. 목적지 패턴 BAD.BAD수신 다이얼 피어 그룹을 사용하여 발신 통화를 라우팅할 때는 더미 대상 패턴이 필요합니다. 이 경우에는 유효한 목적지 패턴이라면 무엇이든 사용할 수 있습니다. 자세한 내용은 대상 패턴(인터페이스)을 참조하세요. 번역 프로필 수신 200수신 전화번호에 통화 라우팅 태그를 추가하는 변환 프로필을 지정합니다. 직통 전화보조 발신음을 제공하지 않고 통화를 연결합니다. 자세한 내용은 direct-inward-dial을 참조하세요. 포트 0/2/0:15이 다이얼 피어와 연결된 물리적 음성 포트입니다. |
| 4 |
TDM-IP 통화 흐름을 사용하는 로컬 게이트웨이의 IP 경로에 대한 미디어 최적화를 활성화하려면 Webex Calling과 PSTN 트렁크 사이에 내부 루프백 다이얼 피어 세트를 추가하여 통화 라우팅을 수정할 수 있습니다. 다음 루프백 다이얼 피어를 구성하십시오. 이 경우 모든 수신 전화는 먼저 다이얼 피어 10으로 연결된 다음, 적용된 라우팅 태그에 따라 다이얼 피어 11 또는 12로 연결됩니다. 라우팅 태그가 제거되면 통화는 다이얼 피어 그룹을 사용하여 발신 트렁크로 연결됩니다. 구성에 대한 필드의 설명은 다음과 같습니다. VoIP 다이얼 피어를 정의하고 관리 및 문제 해결을 용이하게 하기 위해 의미 있는 설명을 제공합니다. 자세한 내용은 dial-peer voice를 참조하세요. 번역 프로필 수신 11이전에 정의한 변환 프로필을 적용하여 발신 트렁크로 전달하기 전에 통화 라우팅 태그를 제거합니다. 목적지 패턴 BAD.BAD수신 다이얼 피어 그룹을 사용하여 발신 통화를 라우팅할 때는 더미 대상 패턴이 필요합니다. 자세한 내용은 대상 패턴(인터페이스)을 참조하세요. session protocol sipv2이 다이얼 피어가 SIP 통화 연결을 처리함을 지정합니다. 자세한 내용은 세션 프로토콜(다이얼 피어)을 참조하세요. 세션 대상 IPv4: 192.168.80.14루프백을 위한 호출 대상으로 로컬 라우터 인터페이스 주소를 지정합니다. 자세한 내용은 세션 대상(voip 다이얼 피어)을 참조하세요. 바인드 제어 소스 인터페이스 GigabitEthernet0/0/0루프백을 통해 전송되는 메시지에 대한 소스 인터페이스 및 관련 IP 주소를 구성합니다. 자세한 내용은 bind를 참조하세요. 미디어 소스 인터페이스 바인딩 GigabitEthernet0/0/0루프백을 통해 전송되는 미디어에 대한 소스 인터페이스와 연결된 IP 주소를 구성합니다. 자세한 내용은 bind를 참조하세요. dtmf-relay rtp-nteRTP-NTE(RFC2833)를 통화 레그에서 기대하는 DTMF 기능으로 정의합니다. 자세한 내용은 DTMF 릴레이(VoIP)를 참조하세요. 코덱 g711alaw 모든 PSTN 통화에서 G.711 코덱을 사용하도록 강제합니다. 사용 중인 ISDN 서비스에서 사용하는 압축 방식에 맞춰 a-law 또는 u-law를 선택하십시오. no vad음성 활동 탐지를 비활성화합니다. 자세한 내용은 vad(다이얼 피어)를 참조하세요. |
| 5 |
다음 통화 라우팅 구성을 추가하십시오. 이로써 로컬 게이트웨이 구성이 완료되었습니다. CUBE 기능을 처음 구성하는 경우 구성을 저장하고 플랫폼을 다시 로드하십시오.
|
이전 섹션의 PSTN-Webex 통화 구성은 Cisco Unified Communications Manager(UCM) 클러스터에 대한 추가 트렁크를 포함하도록 수정할 수 있습니다. 이 경우 모든 통화는 Unified CM을 통해 연결됩니다. UCM에서 5060번 포트로 걸려오는 전화는 PSTN으로 연결되고, 5065번 포트로 걸려오는 전화는 Webex 통화로 연결됩니다. 이 호출 시나리오를 포함하도록 다음과 같은 단계적 구성을 추가할 수 있습니다.
| 1 |
다음 음성 클래스 URI를 구성합니다. |
| 2 |
Unified CM 호스트에 대한 SRV 라우팅을 지정하려면 다음 DNS 레코드를 구성하십시오. IOS XE는 이러한 레코드를 사용하여 로컬에서 대상 UCM 호스트 및 포트를 결정합니다. 이 설정을 사용하면 DNS 시스템에 레코드를 구성할 필요가 없습니다. DNS를 직접 사용하려는 경우 이러한 로컬 구성은 필요하지 않습니다. 구성에 대한 필드의 설명은 다음과 같습니다. 다음 명령은 DNS SRV 리소스 레코드를 생성합니다. 각 UCM 호스트 및 트렁크에 대한 레코드를 생성합니다. ip 호스트 _sip._udp.pstntocucm.io 서버 2 1 5060 ucmsub5.mydomain.com _sip._udp.pstntocucm.io: SRV 리소스 레코드 이름 2: SRV 리소스 레코드 우선순위 1: SRV 리소스 레코드 가중치 5060: 이 리소스 레코드에서 대상 호스트에 사용할 포트 번호입니다. ucmsub5.mydomain.com: 리소스 레코드 대상 호스트 리소스 레코드의 대상 호스트 이름을 확인하려면 로컬 DNS A 레코드를 생성해야 합니다. 예를 들면, IP 호스트 ucmsub5.mydomain.com 192.168.80.65 IP 호스트: 로컬 IOS XE 데이터베이스에 레코드를 생성합니다. ucmsub5.mydomain.com: A 레코드 호스트 이름입니다. 192.168.80.65: 호스트의 IP 주소입니다. UCM 환경 및 선호하는 통화 분배 전략을 반영하도록 SRV 리소스 레코드와 A 레코드를 생성하십시오. |
| 3 |
다음 다이얼 피어를 구성하십시오. |
| 4 |
다음 구성을 사용하여 통화 라우팅을 추가하세요. |
진단 서명(DS)은 Cisco IOS XE 기반 로컬 게이트웨이에서 일반적으로 관찰되는 문제를 사전적으로 탐지하고 이벤트의 이메일, 시스로그 또는 터미널 메시지 알림을 생성합니다. 또한, DS를 설치하여 진단 데이터 수집을 자동화하고 수집한 데이터를 Cisco TAC 사례로 전송하여 해결 시간을 가속화할 수 있습니다.
진단 서명(DS)은 문제 트리거 이벤트 및 문제를 알리고, 문제를 해결, 수정하기 위한 작업에 대한 정보를 포함하는 XML 파일입니다. 시스로그 메시지, SNMP 이벤트 및 특정 표시 명령어 출력의 주기적으로 모니터링을 통해 문제점 탐지 논리를 정의합니다. 작업 유형에는 다음이 포함됩니다.
-
표시 명령 출력 수집 중
-
통합 로그 파일 생성
-
HTTPS, SCP, FTP 서버 등 사용자가 제공한 네트워크 위치로 파일을 업로드하기
TAC 엔지니어는 DS 파일을 작성하고 디지털로 서명하여 완전성을 보호합니다. 각 DS 파일에는 시스템이 지정한 고유한 숫자 ID가 있습니다. 진단 서명 조회 도구 (DSLT)는 다양한 문제를 모니터링하고 해결하기 위한 적용 가능한 서명을 찾을 수 있는 단일 소스입니다.
시작하기 전에:
-
DSLT에서 다운로드한 DS 파일을 편집 하지 않습니다. 완전성 검사 오류로 인해 수정한 파일 설치에 실패합니다.
-
로컬 게이트웨이가 이메일 알림을 발송하기 위해 필요한 간단한 메일 전송 프로토콜(SMTP) 서버입니다.
-
이메일 통지에 대해 보안 SMTP 서버를 사용하고자 하는 경우, 로컬 게이트웨이가 IOS XE 17.6.1 이상을 실행하고 있도록 합니다.
전제 조건
IOS XE 17.6.1 이상을 실행하는 로컬 게이트웨이
-
진단 서명은 기본적으로 활성화됩니다.
-
장치에서 IOS XE 17.6.1 이상을 실행하고 있는 경우, 사전 통지를 보내기 위해 사용하는 보안 이메일 서버를 구성합니다.
configure terminal call-home mail-server :@ priority 1 secure tls end -
통지할 관리자 ds_email 의 이메일 주소로 환경 변수를 구성합니다.
configure terminal call-home diagnostic-signature LocalGateway(cfg-call-home-diag-sign)environment ds_email end
사전 모니터링을 위해 진단 서명 설치
높은 CPU 이용 모니터링하기
이 DS는 SNMP OID 1.3.6.1.4.1.9.2.1.56을 사용하여 5초 CPU 이용을 추적합니다. 사용률이 75% 이상이면 모든 디버그를 비활성화하고 로컬 게이트웨이에 설치한 모든 진단 서명을 제거합니다. 서명을 설치하려면 아래 단계를 따르십시오.
-
명령어 show snmp를 사용하여 SNMP를 활성화하는지 확인합니다. SNMP가 활성화되어 있지 않으면 snmp-server manager 명령을 구성하십시오.
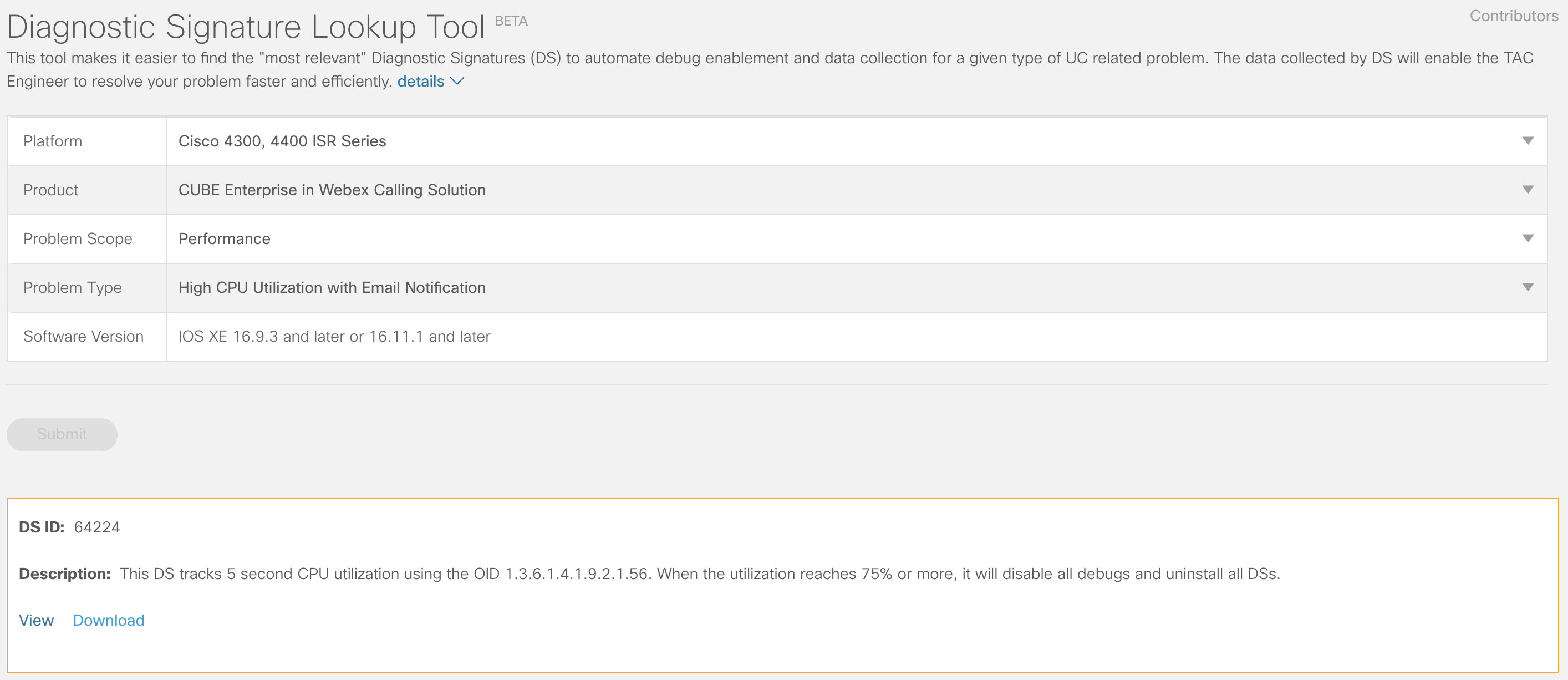
show snmp %SNMP agent not enabled config t snmp-server manager end show snmp Chassis: ABCDEFGHIGK 149655 SNMP packets input 0 Bad SNMP version errors 1 Unknown community name 0 Illegal operation for community name supplied 0 Encoding errors 37763 Number of requested variables 2 Number of altered variables 34560 Get-request PDUs 138 Get-next PDUs 2 Set-request PDUs 0 Input queue packet drops (Maximum queue size 1000) 158277 SNMP packets output 0 Too big errors (Maximum packet size 1500) 20 No such name errors 0 Bad values errors 0 General errors 7998 Response PDUs 10280 Trap PDUs Packets currently in SNMP process input queue: 0 SNMP global trap: enabled 다음과 같이 진단 서명 검색 도구에서 다음 드롭다운 옵션을 사용하여 DS 64224를 다운로드합니다.
copy ftp://username:password@/DS_64224.xml bootflash:필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Catalyst 8000V 엣지 소프트웨어
제품
Webex 통화 솔루션의 CUBE Enterprise
문제 범위
성능
문제 유형
이메일 알림을 통한 높은 CPU 사용률
-
DS XML 파일을 로컬 게이트웨이 플래시로 복사합니다.
copy ftp://username:password@/DS_64224.xml bootflash:다음 예제는 FTP 서버에서 로컬 게이트웨이로 파일을 복사하는 방법을 보여줍니다.
copy ftp://user:pwd@192.0.2.12/DS_64224.xml bootflash: Accessing ftp://*:*@ 192.0.2.12/DS_64224.xml...! [OK - 3571/4096 bytes] 3571 bytes copied in 0.064 secs (55797 bytes/sec) -
로컬 게이트웨이에서 DS XML 파일을 설치합니다.
call-home diagnostic-signature load DS_64224.xml Load file DS_64224.xml success -
통화- 홈 진단 서명 표시 명령어를 사용하여 서명이 성공적으로 설치 있는지 확인합니다. 상태 열에는 "등록된" 값이 있어야 합니다.
show call-home diagnostic-signature Current diagnostic-signature settings: Diagnostic-signature: enabled Profile: CiscoTAC-1 (status: ACTIVE) Downloading URL(s): https://tools.cisco.com/its/service/oddce/services/DDCEService Environment variable: ds_email: username@gmail.comDSes 다운로드:
DS ID
DS 이름
개정
상태
마지막 업데이트(GMT+00:00)
64224
DS_LGW_CPU_MON75
0.0.10
등록됨
2020-11-07 22:05:33
트리거되면 이 서명은 서명 자체를 포함하여 실행 중인 모든 DS를 제거합니다. 필요한 경우, 로컬 게이트웨이에서 높은 CPU 이용률을 계속 모니터하기 위해 DS 64224를 다시 설치하십시오.
비정상적인 통화 연결 끊기 모니터링 중
이 DS는 10분마다 SNMP 폴링을 사용하여 SIP 오류 403, 488 및 503으로 인한 비정상적인 통화 끊김을 감지합니다. 마지막 폴링 이후 오류 횟수 증가가 5 이상이면 시스템 로그와 이메일 알림을 생성합니다. 아래 단계를 따라 서명을 설치하십시오.
-
명령어 show snmp를 사용하여 SNMP가 활성화되어 있도록 합니다. SNMP가 활성화되어 있지 않으면 snmp-server manager 명령을 구성하십시오.
show snmp %SNMP agent not enabled config t snmp-server manager end show snmp Chassis: ABCDEFGHIGK 149655 SNMP packets input 0 Bad SNMP version errors 1 Unknown community name 0 Illegal operation for community name supplied 0 Encoding errors 37763 Number of requested variables 2 Number of altered variables 34560 Get-request PDUs 138 Get-next PDUs 2 Set-request PDUs 0 Input queue packet drops (Maximum queue size 1000) 158277 SNMP packets output 0 Too big errors (Maximum packet size 1500) 20 No such name errors 0 Bad values errors 0 General errors 7998 Response PDUs 10280 Trap PDUs Packets currently in SNMP process input queue: 0 SNMP global trap: enabled -
진단 서명 검색 도구에서 다음 옵션을 사용하여 DS 65221을 다운로드합니다.
필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Catalyst 8000V 엣지 소프트웨어
제품
Webex Calling 솔루션의 CUBE Enterprise
문제 범위
성능
문제 유형
이메일 및 시스로그 알림에서 SIP 비정상적인 통화 연결 끊기 탐지.
-
DS XML 파일을 로컬 게이트웨이로 복사합니다.
copy ftp://username:password@/DS_65221.xml bootflash: -
로컬 게이트웨이에서 DS XML 파일을 설치합니다.
call-home diagnostic-signature load DS_65221.xml Load file DS_65221.xml success -
show call-home diagnostic-signature 명령어를 사용하여 서명이 성공적으로 설치되었는지 확인하십시오. 상태 열에는 "등록됨" 값이 표시되어야 합니다.
진단 서명을 설치하여 문제를 해결
진단 서명(DS)을 사용하여 빠르게 문제를 해결할 수도 있습니다. Cisco TAC 엔지니어는 주어진 문제를 해결하기 위해 필요한 디버그를 활성화하고, 문제점 발생 탐지, 진단 데이터의 올바른 집합을 수집, Cisco TAC 사례로 데이터를 자동으로 전송하는 다양한 서명을 생성했습니다. 따라서 문제 발생을 수동으로 확인하지 않아도 되고 간헐적 및 일시적인 문제를 보다 쉽게 해결할 수 있습니다.
진단 서명 찾기 도구를 사용하여 해당하는 서명을 찾고 해당 문제를 셀프 해결하기 위해 설치할 수 있습니다. 또는 TAC 엔지니어가 지원 참여의 일부로 권장하는 서명을 설치할 수 있습니다.
다음 항목을 탐지하기 위해 DS를 찾고 설치하는 방법의 예제는 다음과 같습니다. “%VOICE_IEC-3-GW: CCAPI: 내부 오류 (통화 spike 임계값): IEC=1.1.181.1.29.0" 시스로그 및 다음 단계를 사용하여 진단 데이터 수집을 자동화합니다.
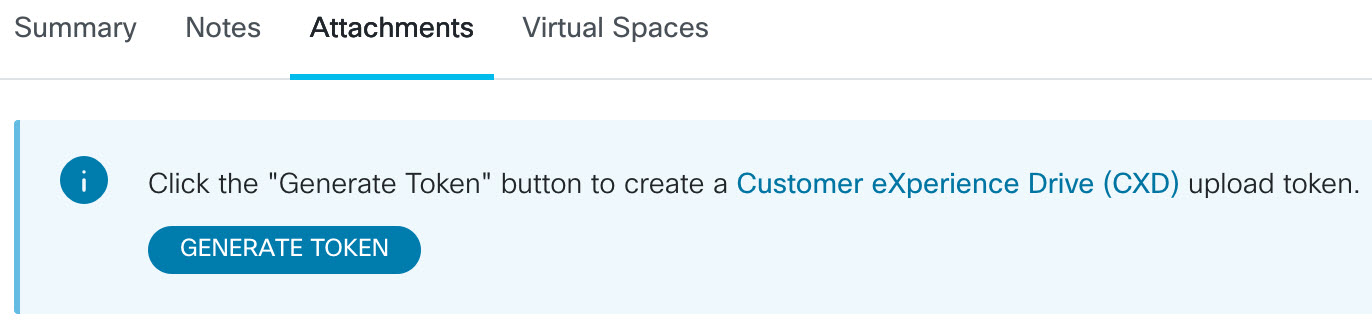
진단 데이터를 업로드하기 위해 다른 DS 환경 변수 ds_fsurl_prefix를 Cisco TAC 파일 서버 경로(cxd.cisco.com)로 구성하십시오. 파일 경로의 사용자 이름은 케이스 번호이고 암호는 파일 업로드 토큰입니다. 파일 업로드 토큰은 다음 그림과 같이 지원 케이스 관리자 에서 가져올 수 있습니다. 파일 업로드 토큰은 필요에 따라 지원 케이스 관리자의 첨부 파일 섹션에서 생성할 수 있습니다.
configure terminal call-home diagnostic-signature LocalGateway(cfg-call-home-diag-sign)environment ds_fsurl_prefix "scp://:@cxd.cisco.com" end예:
call-home diagnostic-signature environment ds_fsurl_prefix " environment ds_fsurl_prefix "scp://612345678:abcdefghijklmnop@cxd.cisco.com"-
명령어 show snmp를 사용하여 SNMP가 활성화되어 있도록 합니다. SNMP가 활성화되어 있지 않으면 snmp-server manager 명령을 구성하십시오.
show snmp %SNMP agent not enabled config t snmp-server manager end -
높은 CPU 모니터링 DS 64224를 사전 대책으로 설치하여 높은 CPU 사용률 중에 모든 디버그 및 진단 서명을 비활성화할 것이 좋습니다. 진단 서명 검색 도구에서 다음 옵션을 사용하여 DS 64224을 다운로드합니다.
필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Catalyst 8000V 엣지 소프트웨어
제품
Webex Calling 솔루션의 CUBE Enterprise
문제 범위
성능
문제 유형
이메일 알림에서 높은 CPU 이용.
-
진단 서명 검색 도구에서 다음 옵션을 사용하여 DS 65095을 다운로드합니다.
필드명
필드 값
플랫폼
Cisco 4300, 4400 ISR 시리즈 또는 Catalyst 8000V 엣지 소프트웨어
제품
Webex Calling 솔루션의 CUBE Enterprise
문제 범위
시스로그
문제 유형
Syslog - %VOICE_IEC-3-GW: CCAPI: 내부 오류 (통화 spike 임계값): IEC=1.1.181.1.29.0
-
DS XML 파일을 로컬 게이트웨이에 복사합니다.
copy ftp://username:password@/DS_64224.xml bootflash: copy ftp://username:password@/DS_65095.xml bootflash: -
로컬 게이트웨이에 CPU 사용량 모니터링용 DS 64224 및 DS 65095 XML 파일을 설치하십시오.
call-home diagnostic-signature load DS_64224.xml Load file DS_64224.xml success call-home diagnostic-signature load DS_65095.xml Load file DS_65095.xml success -
show call-home diagnostic-signature를 사용하여 서명이 성공적으로 설치되었는지 확인합니다. 상태 열에는 "등록됨" 값이 표시되어야 합니다.
show call-home diagnostic-signature Current diagnostic-signature settings: Diagnostic-signature: enabled Profile: CiscoTAC-1 (status: ACTIVE) Downloading URL(s): https://tools.cisco.com/its/service/oddce/services/DDCEService Environment variable: ds_email: username@gmail.com ds_fsurl_prefix: scp://612345678:abcdefghijklmnop@cxd.cisco.com다운로드된 DSes:
DS ID
DS 이름
개정
상태
마지막 업데이트(GMT+00:00)
64224
00:07:45
DS_LGW_CPU_MON75
0.0.10
등록됨
2020-11-08:00:07:45
65095
00:12:53
DS_LGW_IEC_Call_spike_threshold
0.0.12
등록됨
2020-11-08:00:12:53
진단 서명 실행 확인
다음 명령어에서 명령어의 "상태" 열은 콜-홈 진단 서명 이 "실행 중"으로 변경되는 반면, 로컬 게이트웨이는 서명 내에 정의된 작업을 실행합니다. 통화-홈 진단 서명 통계 표시의 출력은 진단 서명이 관심 있는 이벤트를 탐지하고 해당 작업을 실행하는지 확인하는 최선의 방법입니다. "트리거(Triggered/Max/Deinstall) 열은 부여된 서명이 이벤트를 트리거한 횟수, 이벤트를 탐지하기 위해 정의된 최대 횟수 및 최대 트리거된 이벤트의 수를 탐지한 후 서명이 자동으로 제거되는지 여부를 나타냅니다.
show call-home diagnostic-signature
Current diagnostic-signature settings:
Diagnostic-signature: enabled
Profile: CiscoTAC-1 (status: ACTIVE)
Downloading URL(s): https://tools.cisco.com/its/service/oddce/services/DDCEService
Environment variable:
ds_email: carunach@cisco.com
ds_fsurl_prefix: scp://612345678:abcdefghijklmnop@cxd.cisco.com 다운로드된 DSes:
|
DS ID |
DS 이름 |
개정 |
상태 |
마지막 업데이트(GMT+00:00) |
|---|---|---|---|---|
|
64224 |
DS_LGW_CPU_MON75 |
0.0.10 |
등록됨 |
2020-11-08 00:07:45 |
|
65095 |
DS_LGW_IEC_Call_spike_threshold |
0.0.12 |
실행 중 |
2020-11-08 00:12:53 |
통화 홈 진단 서명 통계 표시
|
DS ID |
DS 이름 |
트리거됨/Max/Deinstall |
평균 실행 시간(초) |
최대 실행 시간(초) |
|---|---|---|---|---|
| 64224 |
DS_LGW_CPU_MON75 |
0/0/N |
0.000 |
0.000 |
|
65095 |
DS_LGW_IEC_Call_spike_threshold |
1/20/Y |
23.053 |
23.053 |
진단 알림 이메일 실행 중에 발송되는 도구에는 문제 유형, 장치 세부 사항, 소프트웨어 버전, 구성 실행 및 해당 문제와 관련된 명령어 출력을 표시하는 등의 주요 정보가 포함되어 있습니다.
진단 서명 제거
문제를 해결하기 위해 진단 서명을 사용하면 일반적으로 일부 문제점을 탐지한 후에 제거하기로 정의됩니다. 수동으로 서명을 제거하려면 통화 홈 진단 서명 표시의 출력에서 DS ID 를 검색하고 다음 명령어를 실행합니다.
call-home diagnostic-signature deinstall 예:
call-home diagnostic-signature deinstall 64224
배포에서 관찰된 문제에 따라 새로운 서명은 진단 서명 검색 도구에 주기적으로 추가됩니다. 현재 TAC는 새 사용자 정의 서명을 만드는 요청을 지원하지 않습니다.


