End-to-end encryption for Webex Meetings and Webex Calling
 Feedback?
Feedback?
Compare Webex End-to-End Encryption and Zero-Trust End-to-End Encryption
The Webex Suite offers two types of end-to-end encryption (E2EE):
-
Webex End-to-End Encryption — Default security for user-generated content shared in standard meetings and Webex Messaging.
-
Zero-Trust End-to-End Encryption — Enhanced security for media and user-generated content in Webex end-to-end encrypted meetings. This article focuses mainly on Zero-Trust End-to-End Encryption.
Both types of end-to-end encryption provide an extra layer of encryption that safeguards data from interception attacks, but they differ in the levels of confidentiality that they offer.
Webex End-to-End Encryption
Webex End-to-End Encryption uses the Webex Key Management System* (KMS) to generate and manage encryption keys. These Webex KMS keys are used to encrypt chat messages, files, whiteboards and annotations created by Webex apps and Cisco video devices. Originally used with Webex Messaging, Webex End-to-End Encryption is now also used to encrypt user-generated content in standard Webex Meetings on the Webex Suite meeting platform. With Webex End-to-End Encryption:
-
Data is encrypted in transit and at rest.
-
Webex apps and Cisco devices encrypt all user-generated content, such as messages, files, annotations, and whiteboards, before transmitting them over encrypted TLS.
-
This encrypted content is stored on encrypted content servers in the Webex cloud.
This additional layer of security protects user data in transit from TLS interception attacks, and stored user data from potential bad actors in the Webex cloud.
By default, our cloud-based KMS generates and distributes encryption keys. You also have an option with Webex Hybrid Data Security (HDS) to manage your own, on-premises version of the key management system. For more detail, see Deployment guide for Webex Hybrid Data Security.
The Webex cloud can access and use KMS encryption keys, but only to decrypt data as required for core services, such as:
- Message indexing for search functions
- Data loss prevention
- File transcoding
- eDiscovery
- Data archival
For more information on Webex KMS-based End-to-End Encryption, see Webex Messaging Security Technical Paper.
Zero-Trust End-to-End Encryption
Webex uses Zero-Trust End-to-End Encryption to offer higher levels of security and confidentiality for media and user-generated content (chat, files, whiteboards, and annotations) in Webex End-to-End Encrypted meetings.
Zero-Trust End-to-End Encryption uses the Messaging Layer Security (MLS) protocol to exchange information so that participants in a Webex Meeting can create a common meeting encryption key.
The meeting encryption key is only accessible to the participants in the meeting. The Webex service can't access the meeting key—hence "Zero-Trust."
Scope of Zero-Trust security for Webex Meetings
Zero-Trust end-to-end encrypted Webex meetings support the following:
-
Standards-based protocols (MLS, SFrame) with formally verified cryptography.
- Webex desktop apps for Windows, MacOS, and Linux.
- Webex mobile apps for iOS and Android.
-
Cisco video devices (Room Series, Desk Series, and Webex Board).
-
End-to-end encryption (E2EE) in Personal Room meetings.
-
End-to-end encryption (E2EE) for scheduled meetings.
-
A security icon which lets all meeting participants know at a glance that their meeting is secure, and when end-to-end encryption is enabled for the meeting.
-
Verbal verification of meeting attendees using a new Security Verification Code.
-
Up to 1000 participants.
-
Local recording.
-
In-meeting chat, file transfer, whiteboarding, and annotation.
-
Remote Desktop Control.
-
In Webex App, you can join the meeting using your computer audio only (PSTN-based Call me/Call is not supported).
Zero-Trust security does not support the following in meetings:
-
Older Webex devices, such as the SX, DX, and MX Series.
-
Web browser-based Webex App (web.webex.com).
-
Saving meeting chat, files, whiteboards, and annotations.
-
Saving session data, transcripts, and meeting notes to the cloud.
-
Features provided by Cisco cloud services that require access to decrypted media, including:
-
Network-Based Recording (NBR)
-
Transcoding media
-
In-meeting Webex AI Assistant
-
Automated closed captioning
-
Transcription, etc.
-
-
Calls to and from the Public Switched Telephone Network (PSTN)
-
Calls to and from SIP devices
-
End-to-End Encryption for Webex Calling
Webex Calling currently encrypts calls using Secure Real-time Transport Protocol (SRTP) for media. With the introduction of Webex Calling E2EE, the Webex platform extends its robust end-to-end encryption capabilities, ensuring that only the participants in a communication can decrypt its content, not even the service provider. This enhancement is particularly relevant for markets with high security demands. Webex Calling E2EE operates opportunistically. This means:
-
Opportunistic engagement—Calls begin with SRTP media and automatically upgrade to E2EE when clients support it and no conditions prevent E2EE.
-
Dynamic downgrade—If conditions change during a call (for example, a feature is invoked that requires media processing by the Webex service), the call can temporarily downgrade to SRTP.
-
User notification—Webex App notifies users of transitions between SRTP and E2EE states, ensuring transparency.
When a Webex Calling call is escalated to a Webex Meeting, the original E2EE Calling session is terminated, and the call transitions into the Webex Meeting environment. This means opportunistic Calling E2EE is no longer in effect and all participants from the call are reconnected into the Meeting. The availability of E2EE in the Meeting depends on the default meeting type configured by the customer.
If a Webex Calling call introduces a conference mixer, such as a three-way or n-way call then the opportunistic E2EE also cannot be maintained.
-
The call includes participants outside the organization.
-
At least one participant is not using a Webex App that supports E2EE.
-
The Webex Calling service introduces a media function, such as ad-hoc conferencing or call recording.
Webex Calling does not enable E2EE for certain call types, such as one-on-one PSTN calls (including those between organizations) and one-on-one on-premises trunk (hybrid) calls.
When a Webex service needs to process media, it disables E2EE. This applies to features like Auto Attendant, Call Queue (although the system may enable E2EE after an agent connects), and Voice Portal (for example, voicemail deposit or retrieval). The system also doesn’t support E2EE for pre-answer early media. If privacy settings or policies block or hide the remote party’s identity, such as with Connected Line Identity Privacy or when an assistant answers for an executive, Webex will not enable E2EE.
E2EE works only on primary lines, not on shared or virtual lines.
Enable end-to-end encryption for Webex Calling
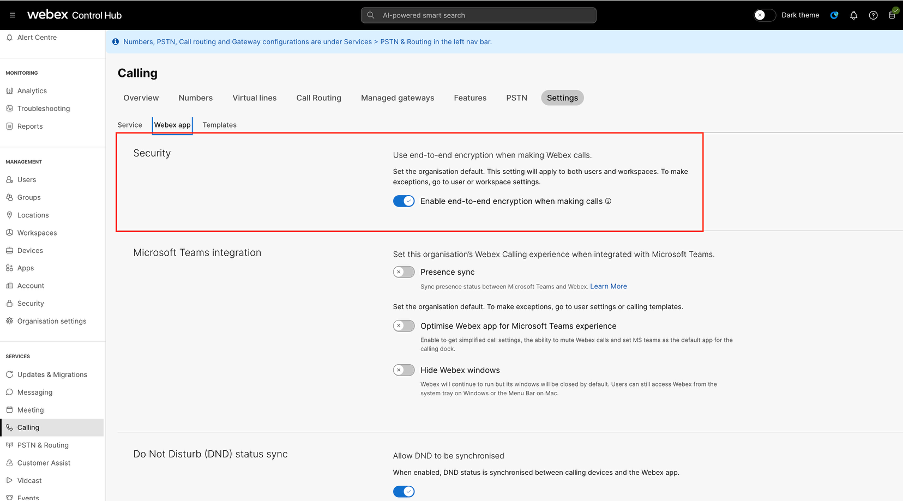
E2EE for Webex Calling is disabled by default. Enable E2EE for Webex Calling to protect user communications across the organization.
- Sign in to Control Hub.
- Go to and switch to Webex App tab.
- In the Security section, turn on Enable end-end encryption when making calls and click Save.
This section is for customers with Full-Featured Meetings.
To join an E2EE meeting from your Webex Board, Room, or Desk device, tap Join Webex and enter the meeting number that is listed in the Webex Meetings invite. Then, tap Join to join the meeting.
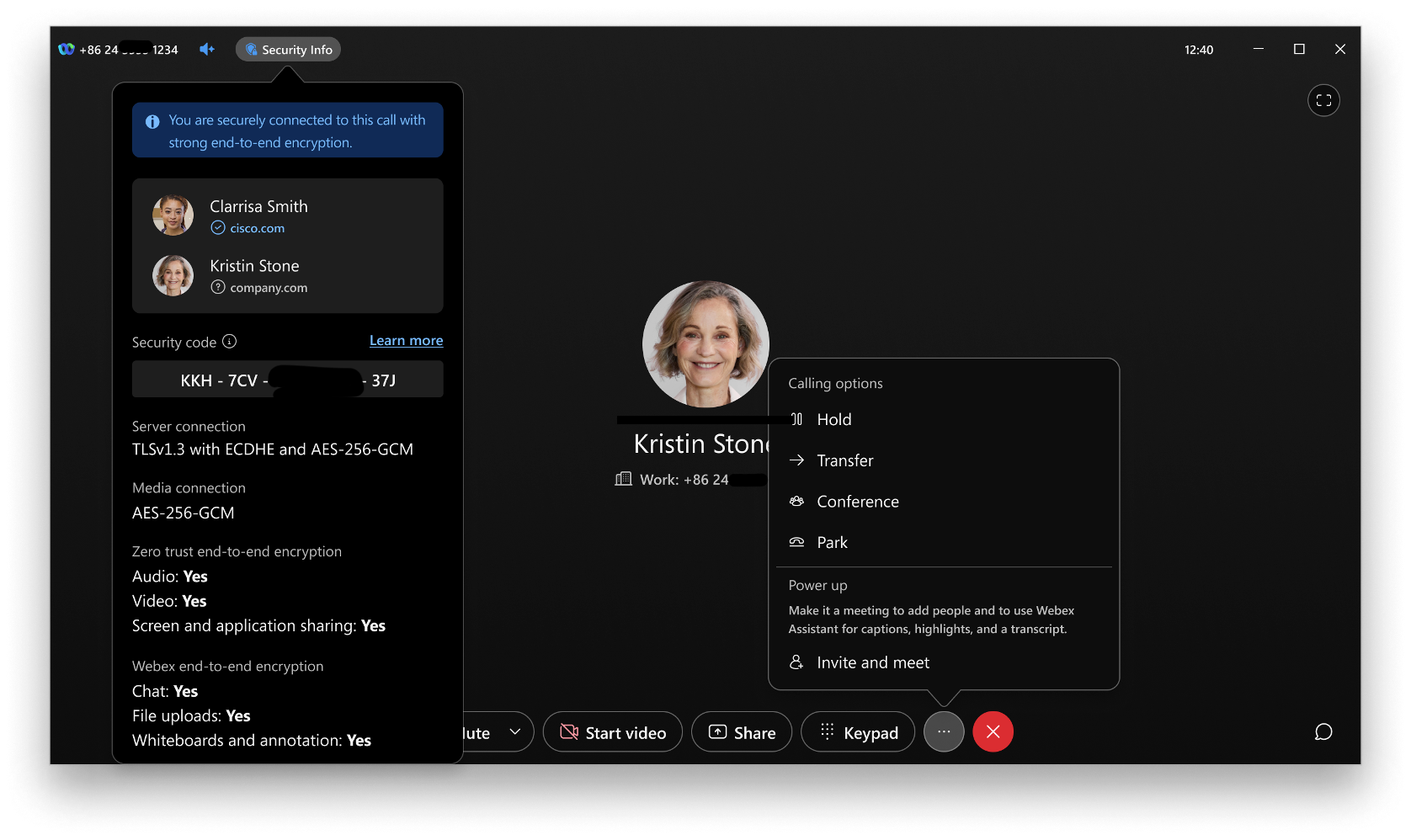
In the meeting, you can check whether the meeting is end-to-end encrypted by looking at the shield icon in the header.
-
 – The meeting is end-to-end encrypted.
– The meeting is end-to-end encrypted. -
 – The connection between your Webex desktop app and the Webex server is secure, but the meeting is not end-to-end encrypted.
– The connection between your Webex desktop app and the Webex server is secure, but the meeting is not end-to-end encrypted.
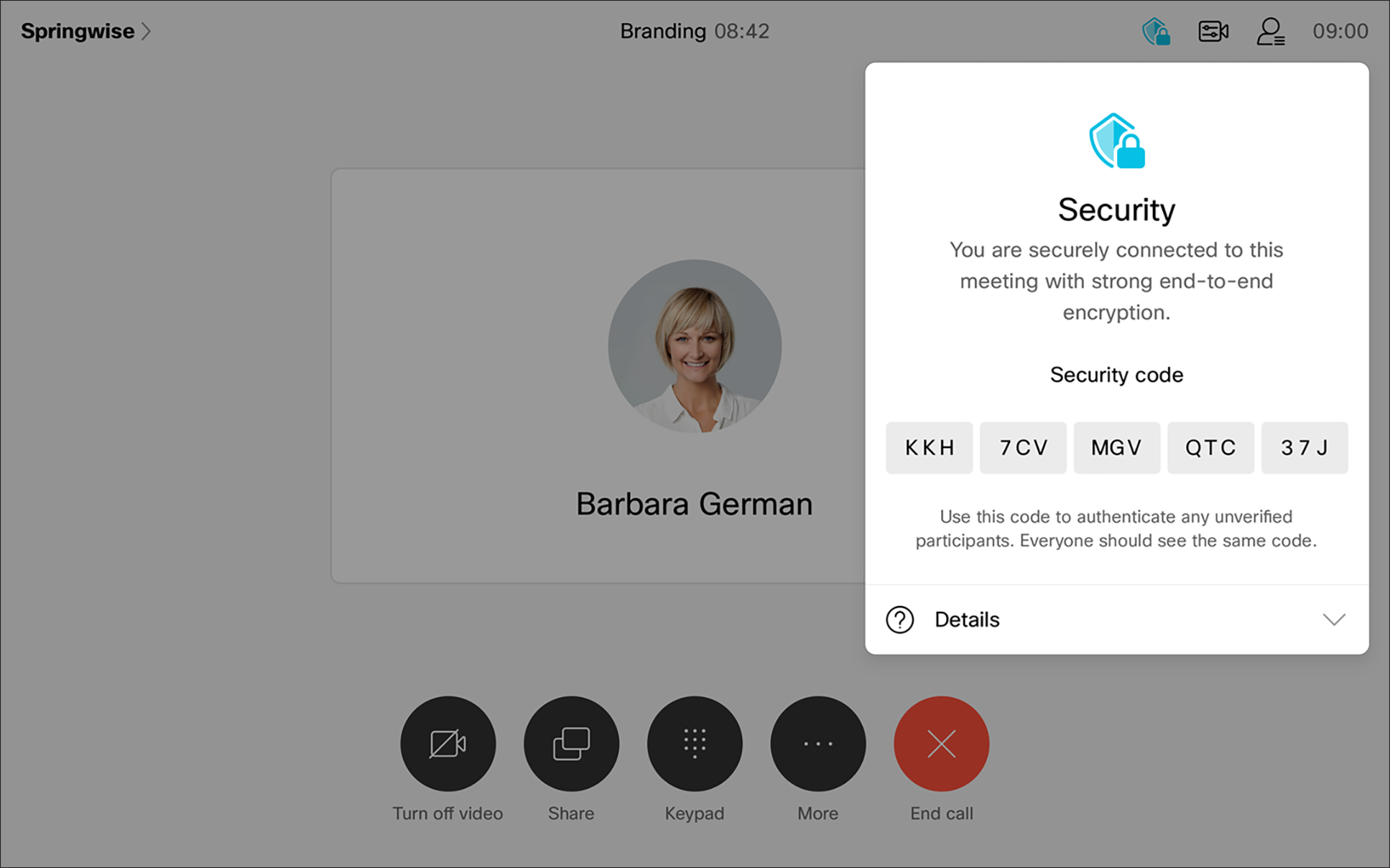
A security code is provided to allow participants to verify that their connection is secure.
Tap the  icon to see the security code and other security information for the meeting. The security code changes each time a participant enters the meeting.
icon to see the security code and other security information for the meeting. The security code changes each time a participant enters the meeting.
All the meeting participants should see the same security code. If one person sees a different security code, their connection is not secure.
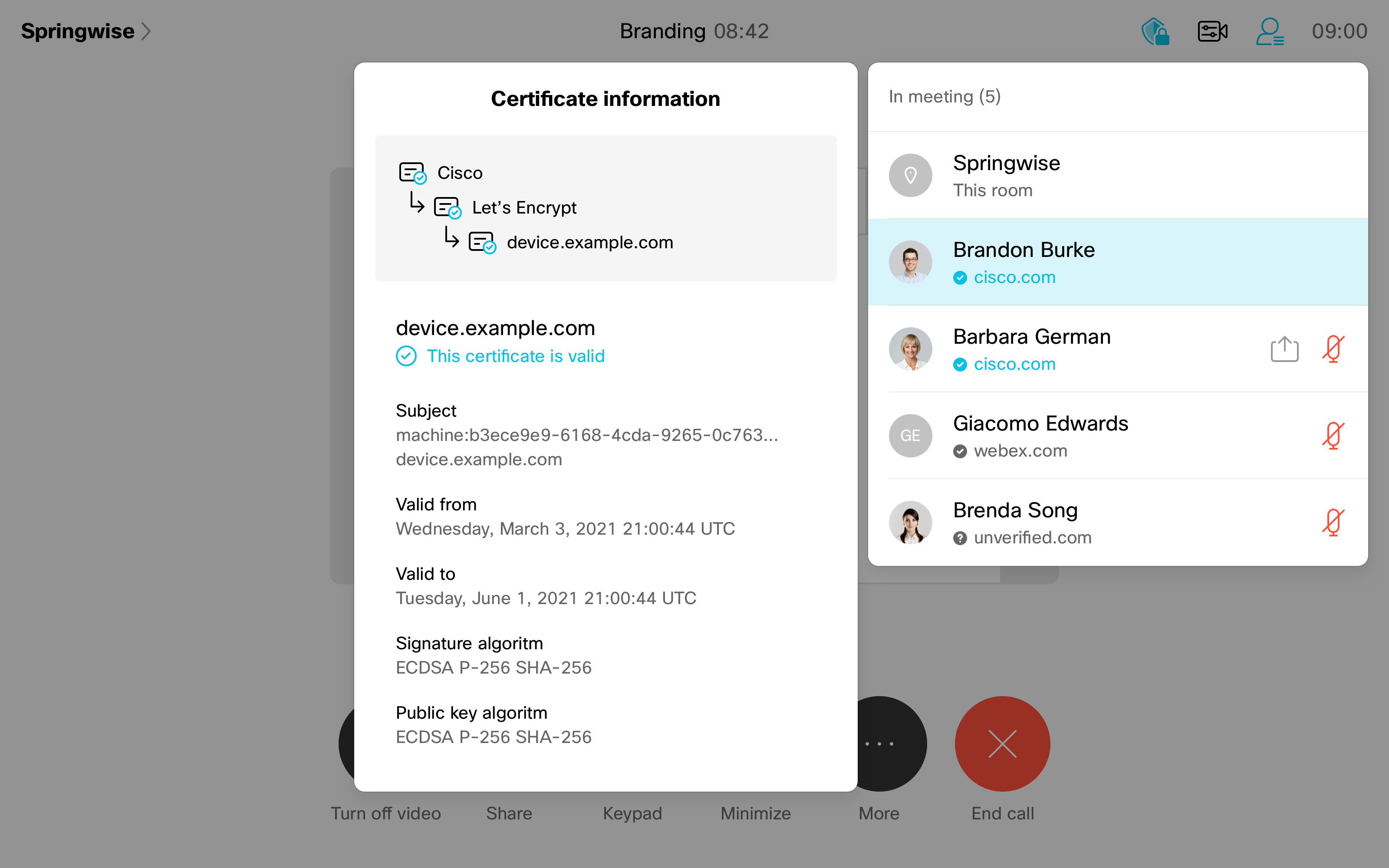
In the participants list, you can see information about the authentication status of each participant: verified or unverified.
-
 – Participant's identity has been verified externally by a Webex Partner Certificate Authority (CA). This requires configuring an external certificate on your personal device.
– Participant's identity has been verified externally by a Webex Partner Certificate Authority (CA). This requires configuring an external certificate on your personal device. -
 – Participant's identity has been verified internally by Webex CA.
– Participant's identity has been verified internally by Webex CA. -
 – Participant's identity is unverified.
– Participant's identity is unverified.
More detailed information about the certificate provider is available by tapping a participant’s name and selecting Show Certificate.

User experience for Webex Calling
The user experience for Webex Calling E2EE aligns with and builds upon the E2EE user experience implemented for Meeting. When a Webex Calling call is End-to-End Encrypted, Webex App (desktop and mobile) displays clear visual indicators. Users also receive distinct visual and audio alerts for transitions between SRTP and E2EE during a call.