- Home
- /
- Article






Site survivability for Webex Calling
 In this article
In this article Feedback?
Feedback?Site Survivability ensures your business remains reachable even if the connection to Webex is lost. It uses a local network gateway to provide fallback calling services to on-site endpoints during network outages.
Deployment considerations
By default, Webex Calling endpoints operate in Active mode, connecting to the Webex cloud for SIP registration and call control. If the network connection to Webex is lost, endpoints automatically switch to Survivability mode and register with the local Survivability Gateway. In this mode, the gateway provides basic backup calling services. Once the network connection to Webex is restored, call control and registrations switch back to the Webex cloud.
The following calls are supported in Survivability mode:
-
Internal calling (intrasite) between supported Webex Calling endpoints
-
External calling (incoming and outgoing) using a local PSTN circuit or SIP trunk to external numbers and E911 providers
To use this feature, you must configure a Cisco IOS XE router in the local network as a Survivability Gateway. The Survivability Gateway syncs calling information daily from the Webex cloud for endpoints at that location. If the endpoints switch to Survivability mode, the gateway can use this information to take over SIP registrations and provide basic calling services.
Single location set up
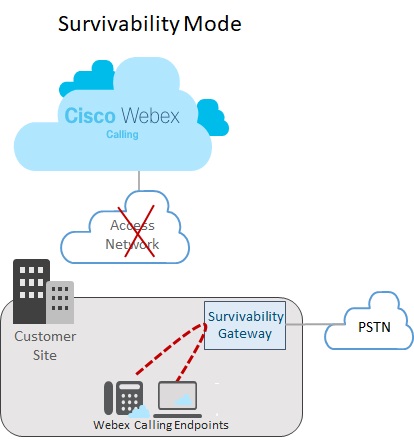
The following image shows a network failure scenario where the connection to Webex is broken and endpoints at the Webex site are operating in Survivability mode. In the image, the Survivability Gateway routes an internal call between two on-site endpoints without requiring a connection to Webex. In this case, the Survivability Gateway is configured with a local PSTN connection. As a result, on-site endpoints in Survivability mode can use the PSTN for incoming and outgoing calls to external numbers and E911 providers.
Key conditions for Site Survivability
The following conditions apply to the Survivability Gateway:
-
The Webex cloud includes the Survivability Gateway IP address, hostname, and port in the device configuration file. As a result, endpoints are able to reach out to the Survivability Gateway for registration if the connection to Webex breaks.
-
The daily call data sync between the Webex cloud and the Survivability Gateway includes authentication information for registered users. As a result, endpoints can maintain secure registrations, even while operating in Survivability mode. The sync also includes routing information for those users.
-
The Survivability Gateway can route internal calls automatically using the routing information that Webex provides. Add a PSTN trunk configuration to the Survivability Gateway to provide external calling.
-
Each site that deploys Site Survivability requires a Survivability Gateway within the local network.
-
Registrations and call control both revert to the Webex cloud once the Webex network connection resumes for at least 30 seconds.
Colocation with Unified SRST
The Survivability Gateway supports the colocation of a Webex Survivability configuration and a Unified SRST configuration on the same gateway. The gateway can support survivability for both Webex Calling endpoints and for endpoints that register to Unified Communications Manager. To configure colocation:
-
Configure Unified SRST support for endpoints that register to Unified Communications Manager. For the configuration, see Cisco Unified SRST Administration Guide.
-
On the same gateway, follow the Site Survivability Configration Task Flow in this article to configure the gateway with Site Survivability for Webex Calling endpoints.
Call routing considerations for colocation
Consider the following when configuring call routing for colocation scenarios:
-
The Survivability Gateway routes internal calls automatically provided that both endpoints in the call are registered to the Survivability Gateway. Internal calls are automatically routed between any registered clients (SRST or Webex Calling).
-
It's possible to have a situation where the connection to one call control system goes down while the connection to the other call control system remains up. As a result, one set of endpoints registers to the Survivability Gateway while another set of endpoints at the same site registers to primary call control. In this case, you may need to route calls between the two sets of endpoints to a SIP trunk or PSTN circuit.
-
External calls and E911 calls can be routed to a SIP trunk or PSTN circuit.
Supported features and components
The following table provides information on supported features.
| Feature | MPP devices and Webex App | VG4xx ATA |
|---|---|---|
|
Intrasite Extension Calling |
Supported automatically with no specific routing configuration required on the Survivability Gateway. |
Supported automatically with no specific routing configuration required on the Survivability Gateway. Alternate numbers aren’t supported. |
|
Intersite and PSTN Calling (Inbound and Outbound) |
PSTN Calling based on telco circuit or SIP trunk. |
PSTN Calling based on telco circuit or SIP trunk. |
|
E911 Call Handling |
E911 Calling requires a PSTN circuit or SIP trunk. Outbound calls use a specific registered Emergency Location Identification Number (ELIN) for a defined Emergency Response Location (ERL). If the emergency operator returns a disconnected call, the Survivability Gateway directs the call to the last device that called the emergency number. |
E911 Calling requires a PSTN circuit or SIP trunk. Outbound calls use a specific registered Emergency Location Identification Number (ELIN) for a defined Emergency Response Location (ERL). If the emergency operator returns a disconnected call, the Survivability Gateway directs the call to the last device that called the emergency number. |
|
Call Hold and Resume |
Supported If you're using Music on Hold (MOH), provision the Survivability Gateway manually with a MOH file. |
VG4xx ATA analog lines can’t put calls on hold or resume. This feature is supported only when an incoming call is received on VG4xx ATA. |
|
Attended Call Transfer |
Supported |
This feature is supported only when an incoming call is received on VG4xx ATA. |
|
Blind Call Transfer |
Supported |
This feature is supported only when an incoming call is received on VG4xx ATA. |
|
Inbound Caller ID (Name) |
Supported |
Supported |
|
Inbound Caller ID (Name & Number) |
Supported |
Supported |
|
Point-to-point Video Call |
Supported |
Not supported |
|
Three-way Calling |
Not supported |
Not supported |
|
Shared Lines |
Supported |
Supported |
|
Virtual Lines |
Supported |
Not supported |
On configuring the feature, Site Survivability is available for the following supported endpoints.
| Type | Models | Minimum Version |
|---|---|---|
| Cisco IP Phone with Multiplatform (MPP) Firmware |
6821, 6841, 6851, 6861, 6861 Wi-Fi, 6871 7811, 7821, 7841, 7861 8811, 8841, 8851, 8861 8845 (audio only), 8865 (audio only), 8875(video) 9800 For more information on supported Cisco IP Phones with Multiplatform (MPP) Firmware, see: |
12.0(1) For 8875 phones - Phone OS 3.2 and later versions For 9800 series- PhoneOS 3.2(1) |
|
Cisco IP Conference Phone |
7832, 8832 |
12.0(1) |
|
Cisco Webex App |
Windows, Mac |
43.2 |
|
Analog Endpoints |
VG400 ATA, VG410 ATA, and VG420 ATA Cisco ATA 191 and 192 |
17.16.1a 11.3(1) for ATA 191 and 192 |
Third party devices are not supported with Survivability Gateway.
The following table helps to configure Cisco IOS XE routers as a Survivability Gateway. This table lists the maximum number of endpoints that each platform supports and the minimum IOS XE version.
Webex Calling Survivability Gateway features are available with Cisco IOS XE Dublin 17.12.3 version or later releases.
| Model | Maximum Endpoint registrations | Minimum Version |
|---|---|---|
|
Integrated Services Router 4321 | 50 |
Cisco IOS XE Dublin 17.12.3 or later releases |
|
Integrated Services Router 4331 | 100 | |
|
Integrated Services Router 4351 | 700 | |
|
Integrated Services Router 4431 | 1200 | |
|
Integrated Services Router 4451-X | 2000 | |
|
Integrated Services Router 4461 | 2000 | |
|
Catalyst Edge 8200L-1N-4T | 1500 | |
|
Catalyst Edge 8200-1N-4T | 2500 | |
|
Catalyst Edge 8300-1N1S-6T | 2500 | |
|
Catalyst Edge 8300-2N2S-6T | 2500 | |
|
Catalyst Edge 8300-1N1S-4T2X | 2500 | |
|
Catalyst Edge 8300-2N2S-4T2X | 2500 | |
|
Catalyst Edge 8000V software small configuration | 500 | |
|
Catalyst Edge 8000V software medium configuration | 1000 | |
|
Catalyst Edge 8000V software large configuration | 2000 |
Port reference information for Survivability Gateway
|
Connection purpose |
Source addresses |
Source ports |
Protocol |
Destination addresses |
Destination ports |
|---|---|---|---|---|---|
|
Call signaling to Survivability Gateway (SIP TLS) |
Devices |
5060-5080 |
TLS |
Survivability Gateway |
8933 |
|
Call media to Survivability Gateway (SRTP) |
Devices |
19560-19660 |
UDP |
Survivability Gateway |
8000-14198 (SRTP over UDP) |
|
Call signaling to PSTN gateway (SIP) |
Survivability Gateway |
Ephemeral |
TCP or UDP |
Your ITSP PSTN gateway |
5060 |
|
Call media to PSTN gateway (SRTP) |
Survivability Gateway |
8000-48198 |
UDP |
Your ITSP PSTN gateway |
Ephemeral |
|
Time synchronization (NTP) |
Survivability Gateway |
Ephemeral |
UDP |
NTP server |
123 |
|
Name resolution (DNS) |
Survivability Gateway |
Ephemeral |
UDP |
DNS server |
53 |
|
Cloud Management |
Connector |
Ephemeral |
HTTPS |
Webex services |
443, 8433 |
For operational guidance on the cloud-mode, refer to the Port Reference Information for Webex Calling Help article.
You can customize port setting values on Cisco IOS XE routers. This table uses default values to provide guidance.
Feature configuration
Site survivability configuration task flow
Complete the following tasks to add Site Survivability for an existing Webex Calling location. If the connection to the Webex cloud breaks, a Survivability Gateway in the local network can provide backup call control for endpoints at that location.
Before you begin
If you need to provision a new gateway to act as the Survivability Gateway, refer to the Webex article Enroll Cisco IOS Managed Gateways to Webex Cloud to add the gateway to Control Hub.
| Steps | Command or Action | Purpose |
|---|---|---|
|
1 | Assign survivability service to a gateway |
In Control Hub, assign the Survivability Gateway service to a gateway. |
|
2 | Download config template |
Download the configuration template from Control Hub. You'll need the template when you configure the gateway command line. |
|
3 |
Configure licenses for the Survivability Gateway. | |
|
4 |
Configure certificates for the Survivability Gateway. | |
|
5 |
Use the configuration template that you downloaded earlier as a guide to configuring the gateway command line. Complete all of the mandatory configurations that are in the template. |
Assign survivability service to a gateway
Before you begin
| 1 |
Go to Calling under Services, and then click the Managed Gateways tab. The Managed Gateways view displays the list of gateways that you manage through Control Hub.
|
| 2 |
Select the gateway that you want to assign as a Survivability Gateway, and choose one of the following, based on the value of the Service field:
|
| 3 |
From the service type drop-down, select Survivability Gateway and complete the following fields:
Once you complete the enrollment, the location details appear in the Managed gateways page. |
| 4 |
Click Assign. The Managed Gateways view displays the list of locations that are assigned to the gateway.
|
Download config template
| 1 |
Sign in to Control Hub. If you’re a partner organization, Partner Hub launches. To open Control Hub, click the Customer view in Partner Hub and select the applicable customer, or select My Organization to open Control Hub settings for the partner organization. |
| 2 |
Go to . |
| 3 |
Click on the applicable Survivability Gateway. |
| 4 |
Click Download Config Template and download the template to your desktop or laptop. |
Configure licensing
| 1 |
Enter global configuration mode on the router: |
| 2 |
Configure licenses using the commands that apply only to your specific platform.
When configuring throughput higher than 250Mbp, you require an HSEC platform license. |
Configure Certificates
Configure certificates on Cisco IOS XE
Complete the following steps to request and create certificates for the Survivability Gateway. Use certificates signed by a publicly known Certificate Authority.
Survivability Gateway platform only supports publicly known CA certificates. Private or enterprise CA certificates can’t be used for Survivability Gateway.
For a list of root certificate authorities that are supported for Webex Calling, see What Root Certificate Authorities are Supported for Calls to Cisco Webex Audio and Video Platforms?.
Survivability Gateway platform doesn’t support the wildcard certificate.
Run the commands from the sample code to complete the steps. For additional information on these commands, along with more configuration options, see the “ SIP TLS Support” chapter in the Cisco Unified Border Element Configuration Guide.
| 1 |
Enter global configuration mode by running the following commands: |
| 2 |
Generate the RSA private key by running the following command. The private key modulus must be at least 2048 bits. |
| 3 |
Configure a trustpoint to hold the Survivability Gateway certificate. The gateway fully qualified domain name (fqdn) must use the same value that you used when assigning the survivability service to the gateway. |
| 4 |
Generate a Certificate Signing Request by running the When prompted, enter After the CSR displays on screen, use Notepad to copy the certificate to a file that you can send to a supported certificate authority (CA). If your certificate signing provider requires a CSR in PEM (Privacy Enhanced Mail) format, add a header and footer before submitting. For example: |
| 5 |
After the CA issues you a certificate, run the When prompted, paste the base 64 CER/PEM issuing CA certificate contents (not the device certificate) into the terminal. |
| 6 |
Import the signed host certificate to the trustpoint using the When prompted, paste the base 64 CER/PEM certificate into the terminal. |
| 7 |
Check that the root CA certificate is available: Only publicly known certificate authorities are supported with the Webex Calling solution. Private or enterprise CA certificates aren’t supported. |
| 8 |
If your root CA certificate isn’t included in the bundle, acquire the certificate and import it to a new trustpoint. Perform this step if a publicly known CA root certificate isn’t available with your Cisco IOS XE gateway. When prompted, paste the base 64 CER/PEM certificate contents into the terminal. |
| 9 |
Using configuration mode, specify the default trust point, TLS version and SIP-UA defaults with the following commands. |
Import certificates along with keypairs
You can import CA certificates and keypairs as a bundle using the PKCS12 format (.pfx or .p12). You can import the bundle from a local file system or a remote server. PKCS12 is a special type of certificate format. It bundles the entire certificate chain from the root certificate through the identity certificate, along with the RSA keypair. That is, the PKCS12 bundle you import would include the keypair, host certificates, and intermediate certificates. Import a PKCS12 bundle for the following scenarios:
-
Export from another Cisco IOS XE router and import into your Survivability Gateway router
-
Generation of the PKCS12 bundle outside Cisco IOS XE router using OpenSSL
Complete the following steps to create, export, and import certificates and keypairs for your Survivability Gateway router.
| 1 |
(Optional) Export the PKCS12 bundle required for your Survivability Gateway router. This step is applicable only if you export from another Cisco IOS XE router. |
| 2 |
(Optional) Create a PKCS12 bundle using OpenSSL. This step is applicable only if you generate a PKCS12 bundle outside Cisco IOS XE using OpenSSL. |
| 3 |
Import the file bundle in PKCS12 format. The following is a sample configuration for the command and details regarding the configurable parameters:
The crypto pki import command automatically builds the trustpoint to accommodate the certificate. |
| 4 |
Using configuration mode, specify the default trust point, TLS version and SIP-UA defaults with the following commands. |
Configure Survivability Gateway
Configure gateway as a survivability gateway
Use the configuration template that you downloaded earlier as a guide to configuring the gateway command line. Complete the mandatory configurations in the template.
The following steps contain sample commands along with an explanation of the commands. Edit the settings to fit your deployment. The angled brackets (for example, <settings>) identify settings where you should enter values that apply to your deployment. The various <tag> settings use numerical values to identify and assign sets of configurations.
- Unless stated otherwise, this solution requires that you complete all the configurations in this procedure.
- When applying settings from the template, replace
%tokens%with your preferred values before you copy to the gateway. - For more information on the commands, see Webex Managed Gateway Command Reference. Use this guide unless the command description refers you to a different document.
| 1 |
Enter into global configuration mode. where:
|
| 2 |
Perform the voice service configurations:
Explanation of commands:
|
| 3 |
Enable Survivability on the router: Explanation of commands:
|
| 4 |
Configure NTP servers:
|
| 5 |
(Optional). Configure general Class of Restriction call permissions: The preceding example creates a set of custom class of restriction named categories (for example, |
| 6 |
Configure a list of preferred codecs. For example, the following list specifies g711ulaw as the preferred codec, followed by g711alaw. Explanation of commands:
|
| 7 |
Configure default voice register pools per location: Explanation of commands:
|
| 8 |
Configure emergency calling: Explanation of commands:
If the WiFi overlay doesn't match to IP subnets accurately, then emergency calling for nomadic devices may not have the correct ELIN mapping. |
| 9 |
Configure dial peers for the PSTN. For an example of the dial peer configuration, see PSTN connection examples. |
| 10 |
Optional. Enable Music on Hold for the router. You must store a music file in the router flash memory in G.711 format. The file can be in .au or .wav file format, but the file format must contain 8-bit 8-kHz data (for example, ITU-T A-law or mu-law data format). Explanation of commands:
|
Complete on-demand sync
Optional. Complete this procedure only if you want to complete an immediate on-demand sync. This procedure isn’t mandatory as the Webex cloud syncs call data to the Survivability Gateway once per day, automatically.
| 1 |
Sign in to Control Hub. If you’re a partner organization, Partner Hub launches. To open Control Hub, click the Customer view in Partner Hub and select the applicable customer, or select My Organization to open Control Hub settings for the partner organization. |
| 2 |
Go to . |
| 3 |
Click on the applicable Survivability Gateway to open the Survivability Service view for that gateway. |
| 4 |
Click the Sync button. |
| 5 |
Click Submit. It may take up to 10 minutes to complete the sync.
|
Edit Survivability Gateway properties
| 1 |
Sign in to Control Hub. If you’re a partner organization, Partner Hub launches. To open Control Hub, click the Customer view in Partner Hub and select the applicable customer, or select My Organization to open Control Hub settings for the partner organization. |
| 2 |
Go to . |
| 3 |
Click on the applicable Survivability Gateway to open the Survivability Service view for that gateway. |
| 4 |
Click the Edit button and update settings for the following.
|
| 5 |
Click Submit. If you want to delete a Survivability Gateway from Control Hub, unassign the Survivability Gateway service first. For more details, see Assign Services to Managed Gateways. |
Configurations to enable CDRs on survivability gateway
The connector automatically configures CDR-related commands to facilitate the collection of call count metrics.
At the end of a survivability event, the connector processes the CDRs generated during the event period, along with the configuration data, to identify various call counts. The metrics include counts of total calls, emergency calls, and external calls, and are used to monitor internal feature usage. Only the call count metrics are sent to the Webex cloud while the actual CDRs are not transmitted.
The following is a sample configuration:
!
gw-accounting file
primary ifs bootflash:guest-share/cdrs/
acct-template callhistory-detail
maximum cdrflush-timer 5
cdr-format detailed
!
Explanation of the commands:
-
primary ifs bootflash:guest-share/cdrs/- This command is to store the CDR files under the guest-share folder to allow access by the connector. -
acct-template callhistory-detail- This command is required to include the dial-peer tag in the CDR. -
maximum cdrflush-timer 5- The default is 60 minutes, but setting it to 5 minutes allows CDRs to be logged to the file more quickly. -
cdr-format detailed- This is the default format. The compact format is not suitable as it does not include the dial-peer tag.
Limitations and restrictions
-
Public Switched Telephone Network (PSTN) service availability depends on the SIP trunks or PSTN circuits available during a network outage.
-
Devices with 4G and 5G connectivity (for example, Webex App for mobile or tablet) could still be able to register to Webex Calling during outages. As a result, they could be unable to call other numbers from the same site location during an outage.
-
Dialing patterns could work differently in Survivability mode than Active mode.
-
The Survivability Gateway must use an IPv4 address. IPv6 isn't supported.
-
An on-demand sync status update in the Control Hub could take up to 30 minutes.
-
The Calling dock is not supported in Survivability mode.
-
Don't configure SIP bind command in voice service voip configuration mode. It leads to registration failure of MPP phones with Survivability Gateway.
-
Ensure that Equipment Serial Numbers (ESNs) across different physical locations are unique, to avoid conflicts and improve traceability, redundancy, and failover reliability.
While in Survivability mode:
-
MPP Softkeys such as Park, Unpark, Barge, Pickup, Group Pickup, and Call Pull buttons aren’t supported. However, they don’t appear disabled.
-
Calls made to shared lines can ring on all devices. However, other shared line functionality such as Remote Line State Monitoring, Hold, Resume, Synchronized DND, and Call Forwarding settings aren’t available.
-
Conferencing or Three-way Calling isn’t available.
-
Calls made are stored in the local call history for both MPP devices and Webex App.
User experience during failover
If a site in your company loses internet connectivity and you’re at that site, you can still make and receive calls, both internally in your company and externally to customers. See Webex App | Site survivability.
Configuration examples
PSTN connection examples
For external calling, configure a connection to the PSTN. This topic outlines some of the options and provides sample configurations. The two main options are:
-
Voice Interface Card (VIC) connection to PSTN
-
SIP trunk to PSTN gateway
Voice interface card connection to PSTN
You can install a Voice Interface Card (VIC) on the router and configure a port connection to the PSTN.
-
For details on how to install the VIC on the router, refer to the hardware install guide for your router model.
-
For details on how to configure the VIC, along with examples, see Voice Port Configuration Guide, Cisco IOS Release 3S.
SIP trunk to PSTN gateway
You can configure a SIP trunk connection that points to a PSTN gateway. To configure the trunk connection on the gateway, use the voice-class-tenant configuration. Following is a sample configuration.
voice class tenant 300
sip-server ipv4:<ip_address>:<port>
session transport udp
bind all source-interface GigabitEthernet0/0/1
Dial peer configuration
For trunk connections, configure inbound and outbound dial peers for the trunk connection. The configuration depends on your requirements. For detailed configuration information, see Dial Peer Configuration Guide, Cisco IOS Release 3S.
Following are sample configurations:
Outbound dial-peers to the PSTN with UDP and RTP
dial-peer voice 300 voip
description outbound to PSTN
destination-pattern +1[2-9]..[2-9]......$
translation-profile outgoing 300
rtp payload-type comfort-noise 13
session protocol sipv2
session target sip-server
voice-class codec 1
voice-class sip tenant 300
dtmf-relay rtp-nte
no vad
Inbound dial-peer from the PSTN using UDP with RTP
voice class uri 350 sip
host ipv4:<ip_address>
!
dial-peer voice 190 voip
description inbound from PSTN
translation-profile incoming 350
rtp payload-type comfort-noise 13
session protocol sipv2
voice-class codec 1
voice-class sip tenant 300
dtmf-relay rtp-nte
no vad
Number translations
For PSTN connections, you may need to use translation rules to translate internal extensions to an E.164 number that the PSTN can route. Following are sample configurations:
From PSTN translation rule with non +E164
voice translation-rule 350
rule 1 /^\([2-9].........\)/ /+1\1/
voice translation-profile 300
translate calling 300
translate called 300
From phone system translation rule with +E164
voice translation-rule 300
rule 1 /^\+1\(.*\)/ /\1/
voice translation-profile 300
translate calling 300
translate called 300
Emergency calling example
The following example contains an example of an emergency calling configuration.
If the WiFi overlay doesn't match to IP subnets accurately, then emergency calling for nomadic devices may not have a correct ELIN mapping.
Emergency response locations (ERLs)
voice emergency response location 1
elin 1 14085550100
subnet 1 192.168.100.0 /26
!
voice emergency response location 2
elin 1 14085550111
subnet 1 192.168.100.64 /26
!
voice emergency response zone 1
location 1
location 2
Outgoing dial peers
voice class e164-pattern-map 301
description Emergency services numbers
e164 911
e164 988
!
voice class e164-pattern-map 351
description Emergency ELINs
e164 14085550100
e164 14085550111
!
dial-peer voice 301 pots
description Outbound dial-peer for E911 call
emergency response zone 1
destination e164-pattern-map 301
!
dial-peer voice 301 pots
description Inbound dial-peer for E911 call
emergency response callback
incoming called e164-pattern-map 351
direct-inward-dial


