- Accueil
- /
- Article


Informations de référence sur les ports pour l’appel Webex
 Dans cet article
Dans cet article Un commentaire ?
Un commentaire ?Cet article s'adresse aux administrateurs réseau, et plus particulièrement aux administrateurs de pare-feu et de sécurité proxy qui utilisent les services d'appel Webex au sein de leur organisation. Il décrit les exigences réseau et répertorie les adresses, les ports et les protocoles utilisés pour connecter vos téléphones, l'application Webex et les passerelles vers les services d'appel Webex.
Un pare-feu et un proxy correctement configurés sont essentiels au bon déroulement du déploiement d'un système d'appel. Webex Calling utilise les protocoles SIP et HTTPS pour la signalisation des appels, ainsi que les adresses et ports associés pour les médias, la connexion réseau et la connectivité de la passerelle, car Webex Calling est un service mondial.
Toutes les configurations de pare-feu ne nécessitent pas l'ouverture des ports. Toutefois, si vous utilisez des règles de trafic interne-externe, vous devez ouvrir les ports nécessaires aux protocoles requis pour permettre aux services de sortir.
Traduction d'adresses réseau (NAT)
Les fonctionnalités de traduction d'adresses réseau (NAT) et de traduction d'adresses de port (PAT) sont appliquées à la frontière entre deux réseaux pour traduire les espaces d'adressage ou pour éviter la collision des espaces d'adressage IP.
Les organisations utilisent des technologies de passerelle telles que des pare-feu et des proxys qui fournissent des services NAT ou PAT pour permettre l'accès Internet aux applications Webex App ou aux appareils Webex qui se trouvent sur un espace d'adressage IP privé. Ces passerelles permettent de faire apparaître le trafic provenant d'applications ou d'appareils internes vers Internet comme provenant d'une ou plusieurs adresses IP routables publiquement.
-
Si vous déployez NAT, il n'est pas obligatoire d'ouvrir un port entrant sur le pare-feu.
-
Vérifiez la taille du pool NAT requise pour la connectivité des applications ou des appareils lorsque plusieurs utilisateurs et appareils accèdent à Webex Calling. & Services compatibles Webex utilisant NAT ou PAT. Veillez à attribuer un nombre suffisant d'adresses IP publiques aux pools NAT afin d'éviter l'épuisement des ports. La saturation des ports empêche les utilisateurs et appareils internes de se connecter aux services Webex Calling et Webex Aware.
-
Définissez des périodes de liaison raisonnables et évitez de manipuler le protocole SIP sur le périphérique NAT.
-
Configurez un délai d'expiration NAT minimal pour garantir le bon fonctionnement des périphériques. Exemple : Les téléphones Cisco envoient un message de rafraîchissement REGISTER de suivi toutes les 1 à 2 minutes.
-
Si votre réseau utilise NAT ou SPI, définissez un délai d'expiration plus long (d'au moins 30 minutes) pour les connexions. Ce délai d'expiration permet une connectivité fiable tout en réduisant la consommation de batterie des appareils mobiles des utilisateurs.
Passerelle de couche application SIP
Si un routeur ou un pare-feu est compatible SIP, ce qui implique que la passerelle de couche application SIP (ALG) ou une fonction similaire est activée, nous vous recommandons de désactiver cette fonctionnalité pour un fonctionnement correct du service. Bien que tout le trafic d'appel Webex soit chiffré, certaines implémentations SIP ALG peuvent entraîner des problèmes de traversée du pare-feu. Par conséquent, nous recommandons de désactiver le SIP ALG afin de garantir un service de haute qualité.
Consultez la documentation du fabricant concerné pour connaître la procédure de désactivation du SIP ALG sur les appareils spécifiques.
Prise en charge des proxys pour les appels Webex
Les organisations déploient un pare-feu Internet ou un proxy Internet et un pare-feu pour inspecter, restreindre et contrôler le trafic HTTP qui entre et sort de leur réseau. Protégeant ainsi leur réseau contre diverses formes de cyberattaques.
Les proxys remplissent plusieurs fonctions de sécurité telles que :
-
Autoriser ou bloquer l'accès à des URL spécifiques.
-
Authentification de l’utilisateur
-
IP address/domain/hostname/URI vérification de réputation
-
Décryptage et inspection du trafic
La configuration de la fonction proxy s'applique à toutes les applications utilisant le protocole HTTP.
L'application Webex et les applications pour appareils Webex comprennent les éléments suivants :
-
Services Webex
-
Procédures d'activation des appareils clients (CDA) utilisant la plateforme de provisionnement Cisco Cloud, telles que GDS, activation et provisionnement des appareils EDOS & Intégration à Webex Cloud.
-
Authentification par certificat
-
Mises à jour du firmware
-
Rapports d'état
-
Téléchargements PRT
-
Services XSI
Si une adresse de serveur proxy est configurée, alors seul le trafic de signalisation sera concerné. (HTTP/HTTPS) est envoyé au serveur proxy. Les clients qui utilisent le protocole SIP pour s'inscrire au service d'appel Webex et les médias associés ne sont pas envoyés au proxy. Par conséquent, autorisez ces clients à traverser directement le pare-feu.
Options de proxy prises en charge, configuration & Types d'authentification
Les types de proxy pris en charge sont :
-
Proxy explicite (avec ou sans inspection) — Configurez l’application ou l’appareil client avec un proxy explicite pour spécifier le serveur à utiliser.
-
Proxy transparent (non inspectant) — Les clients ne sont pas configurés pour utiliser une adresse de serveur proxy spécifique et ne nécessitent aucune modification pour fonctionner avec un proxy non inspectant.
-
Proxy transparent (inspection) — Les clients ne sont pas configurés pour utiliser une adresse de serveur proxy spécifique. Aucune modification de la configuration HTTP n'est nécessaire ; cependant, vos clients (application ou appareils) ont besoin d'un certificat racine pour faire confiance au proxy. L'équipe informatique utilise des serveurs proxy d'inspection pour appliquer des politiques concernant les sites web à visiter et les types de contenu interdits.
Configurez manuellement les adresses proxy pour les périphériques Cisco et l'application Webex à l'aide de :
-
Système d'exploitation de la plateforme
-
Interface utilisateur de l'appareil
-
Détecté automatiquement à l'aide de mécanismes de proxy Web tels que :
-
Découverte automatique de proxy Web (WPAD) - Protocole de découverte automatique de proxy Web
-
Fichiers de configuration automatique du proxy (PAC) - Fichiers de configuration automatique du proxy
-
Lors de la configuration de vos types de produits préférés, choisissez parmi les configurations de proxy suivantes : & types d'authentification dans le tableau :
|
Produit |
Configuration du proxy |
Type d’authentification |
|---|---|---|
|
Webex pour Mac |
Manuelle, WPAD, PAC |
Aucune authentification, Basique, NTLM,† |
|
Webex pour Windows |
Manuelle, WPAD, PAC, GPO |
Aucune authentification, Basique, NTLM, †, Négocier † |
|
Webex pour iOS |
Manuelle, WPAD, PAC |
Aucune authentification, basique, Digest, NTLM |
|
Webex pour Android |
Manuelle, PAC |
Aucune authentification, basique, Digest, NTLM |
|
Application Web Webex |
Prise en charge par le système d'exploitation |
Aucune authentification, Basique, Digest, NTLM, Négocier † |
|
Périphériques Webex |
WPAD, PAC, ou manuelle |
Aucune authentification, basique, Digest |
|
Téléphones IP Cisco |
Manuelle, WPAD, PAC |
Aucune authentification, basique, Digest |
|
Nœud de maillage vidéo WebEx |
Manuelle |
Aucune authentification, basique, Digest, NTLM |
Pour les légendes du tableau :
-
†Authentification NTLM Mac - La machine n'a pas besoin d'être connectée au domaine, l'utilisateur est invité à saisir un mot de passe
-
†Authentification NTLM Windows - Prise en charge uniquement si la machine est connectée au domaine
-
Négocier †- Kerberos avec authentification de secours NTLM.
-
Pour connecter un appareil Cisco Webex Board, Desk ou Room Series à un serveur proxy, consultez Connectez votre appareil Board, Desk ou Room Series à un serveur proxy.
-
Pour les téléphones IP Cisco, voir Configurer un serveur proxy comme exemple de configuration du serveur proxy et des paramètres.
Pour No Authentication, configurez le client avec une adresse proxy qui ne prend pas en charge l'authentification. Lors de l'utilisation de Proxy Authentication, configurez avec des informations d'identification valides. Les proxys qui inspectent le trafic Web peuvent interférer avec les connexions Web Socket. Si ce problème survient, contourner le trafic non inspecté vers *.Webex.com pourrait résoudre le problème. Si vous voyez déjà d'autres entrées, ajoutez un point-virgule après la dernière entrée, puis saisissez l'exception Webex.
Paramètres de proxy pour Windows
Microsoft Windows prend en charge deux bibliothèques réseau pour le trafic HTTP (WinINet et WinHTTP) qui permettent la configuration de proxy. WinINet est un sur-ensemble de WinHTTP.
-
WinInet est conçu pour les applications clientes de bureau mono-utilisateur.
-
WinHTTP est principalement conçu pour les applications multi-utilisateurs basées sur serveur.
Lors du choix entre les deux, sélectionnez WinINet pour vos paramètres de configuration de proxy. Pour plus de détails, voir wininet-vs-winhttp.
Consultez la section Configurer une liste de domaines autorisés à accéder à Webex sur votre réseau d'entreprise pour plus de détails sur les points suivants :
-
Afin de garantir que les utilisateurs ne se connectent aux applications qu'à l'aide de comptes provenant d'une liste prédéfinie de domaines.
-
Utilisez un serveur proxy pour intercepter les requêtes et limiter les domaines autorisés.
Inspection du proxy et épinglage du certificat
L'application et les appareils Webex valident les certificats des serveurs lors de l'établissement des sessions TLS. Les contrôles de certificats, tels que la vérification de l'émetteur du certificat et la signature numérique, reposent sur la vérification de la chaîne de certificats jusqu'au certificat racine. Pour effectuer les contrôles de validation, l'application et les appareils Webex utilisent un ensemble de certificats d'autorité de certification racine de confiance installés dans le magasin de certificats de confiance du système d'exploitation.
Si vous avez déployé un proxy d'inspection TLS pour intercepter, décrypter et inspecter le trafic d'appels Webex. Assurez-vous que le certificat présenté par le proxy (au lieu du certificat de service Webex) est signé par une autorité de certification et que le certificat racine est installé dans le magasin de certificats de confiance de votre application Webex ou de votre appareil Webex.
-
Pour l'application Webex : installez le certificat d'autorité de certification utilisé pour signer le certificat par le proxy dans le système d'exploitation de l'appareil.
-
Pour les appareils Webex Room et les téléphones IP multiplateformes Cisco : ouvrez une demande de service auprès de l’équipe TAC pour installer le certificat CA.
Ce tableau présente l'application Webex et les appareils Webex qui prennent en charge l'inspection TLS par les serveurs proxy.
|
Produit |
Prend en charge les autorités de certification de confiance personnalisées pour l’inspection TLS |
|---|---|
|
Application Webex (Windows, Mac, iOS, Android, Web) |
Oui |
|
Périphériques Webex Room |
Oui |
|
Téléphones Cisco IP Multiplatform (MPP) |
Oui |
Configuration du pare-feu
Cisco prend en charge les services Webex Calling et Webex Aware dans les centres de données sécurisés de Cisco et d'Amazon Web Services (AWS). Amazon a réservé ses sous-réseaux IP à l'usage exclusif de Cisco et a sécurisé les services situés dans ces sous-réseaux au sein du cloud privé virtuel AWS.
Configurez votre pare-feu pour permettre la communication entre vos appareils, les applications de l'application et les services exposés à Internet afin qu'ils fonctionnent correctement. Cette configuration permet d'accéder à tous les services cloud Webex Calling et Webex Aware pris en charge, ainsi qu'aux noms de domaine, adresses IP, ports et protocoles.
Autoriser ou autoriser l'accès aux éléments suivants pour que les services Webex Calling et Webex Aware fonctionnent correctement.
-
Le URLs/Domains mentionné dans la section Domaines et URL pour les services d'appel Webex
-
Les sous-réseaux IP, les ports et les protocoles répertoriés dans la section Sous-réseaux IP pour les services d'appel Webex sont utilisés à de multiples fins, notamment la signalisation des appels, le trafic multimédia vers et depuis Webex Calling, la synchronisation du protocole de temps réseau (NTP) et les tests de préparation du réseau CScan pour ces sous-réseaux IP.
-
Si votre organisation utilise la suite de services de collaboration cloud Webex, y compris Webex Meetings, Messaging, Webex Attendant Console et d'autres services connexes, assurez-vous que les sous-réseaux IP, les domaines et les URL spécifiés dans les articles Configuration réseau requise pour les services Webex et Configuration réseau requise pour la console Attendant sont autorisés sur votre réseau. Ceci est nécessaire pour garantir une connectivité et un fonctionnement corrects de ces services Webex.
Si vous utilisez uniquement un pare-feu, le filtrage du trafic Webex Calling à l'aide des seules adresses IP n'est pas pris en charge, car certains pools d'adresses IP sont dynamiques et peuvent changer à tout moment. Mettez à jour vos règles régulièrement ; ne pas mettre à jour votre liste de règles de pare-feu pourrait impacter l'expérience de vos utilisateurs. Cisco ne recommande pas le filtrage d'un sous-ensemble d'adresses IP en fonction d'une région géographique ou d'un fournisseur de services cloud particulier. Le filtrage par région peut entraîner une dégradation importante de l'expérience d'appel.
Cisco ne gère pas de pools d'adresses IP à évolution dynamique, c'est pourquoi il n'est pas mentionné dans cet article.
Si votre pare-feu ne prend pas en charge Domain/URL Si vous devez filtrer les données, utilisez l'option de serveur proxy d'entreprise. Cette option filters/allows par URL/domain le trafic de signalisation HTTPS destiné aux services Webex Calling et Webex Aware sur votre serveur proxy, avant d'être transféré vers votre pare-feu.
Vous pouvez configurer le trafic en utilisant le filtrage des ports et des sous-réseaux IP pour les médias d'appel. Étant donné que le trafic multimédia nécessite un accès direct à Internet, choisissez l'option de filtrage d'URL pour le trafic de signalisation.
Pour les appels Webex, UDP est le protocole de transport privilégié de Cisco pour les médias, et il est recommandé d'utiliser uniquement SRTP sur UDP. Les protocoles de transport TCP et TLS pour les médias ne sont pas pris en charge par Webex Calling en environnement de production. La nature orientée connexion de ces protocoles affecte la qualité des médias sur les réseaux à perte. Si vous avez des questions concernant le protocole de transport, veuillez ouvrir un ticket d'assistance.
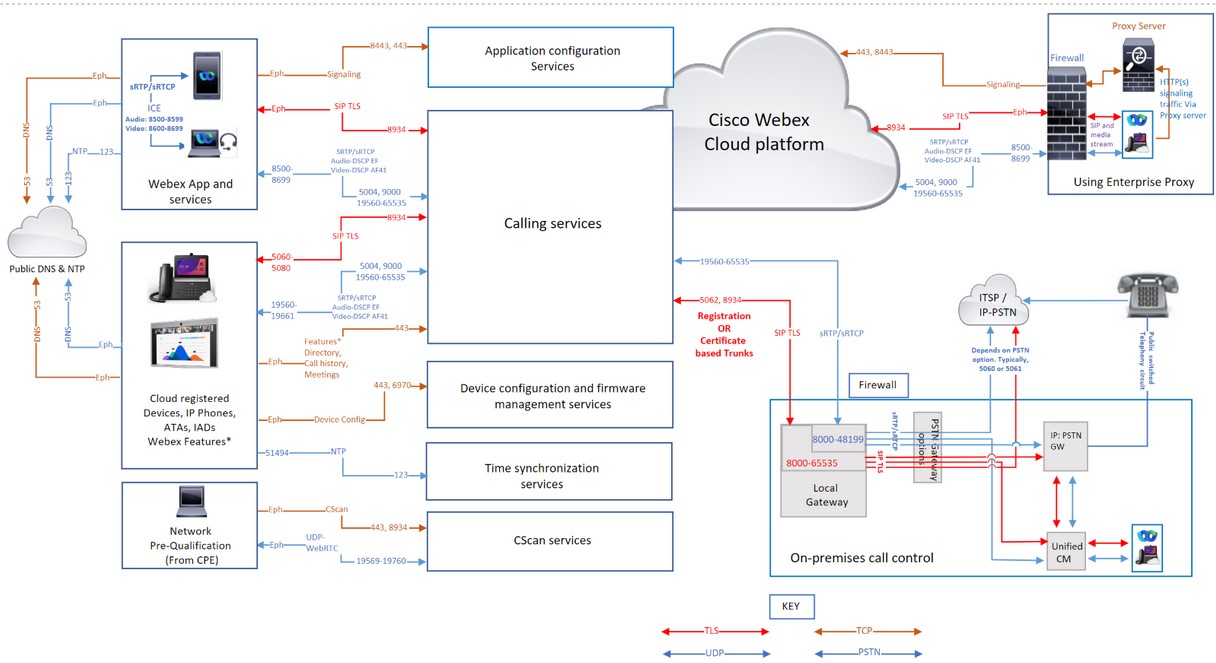
Domaines et URL pour les services d'appel Webex
UN * affiché au début d'une URL (par exemple, *.webex.com) indique que les services du domaine de premier niveau et de tous les sous-domaines sont accessibles.
|
Domaine/URL |
Description |
Applications et périphériques Webex utilisant ces domaines/URLs |
|---|---|---|
|
Services Webex Cisco | ||
|
*.broadcloudpbx.com |
Microservices d’autorisation Webex pour le lancement croisé de Control Hub vers le portail d’administration d’appel. |
Control Hub |
|
*.broadcloud.com.au |
Services d’appel Webex en Australie. |
Tous |
|
*.broadcloud.eu |
Services d’appels Webex en Europe. |
Tous |
|
*.broadcloudpbx.net |
Services de configuration et de gestion des clients appelants. |
Applications Webex |
|
*.webex.com *.cisco.com |
Appels Webex de base & Services Webex Aware
Lorsqu'un téléphone se connecte à un réseau pour la première fois ou après une réinitialisation d'usine sans options DHCP définies, il contacte un serveur d'activation de périphérique pour un provisionnement sans intervention. Les nouveaux téléphones utilisent activate.cisco.com et les téléphones avec une version de firmware antérieure à 11.2(1) continuent d'utiliser webapps.cisco.com pour le provisionnement. Téléchargez le firmware et les mises à jour de localisation de l'appareil depuis binaries.webex.com. Autoriser les téléphones multiplateformes Cisco (MPP) antérieurs à la version 12.0.3 à accéder à sudirenewal.cisco.com via le port 80 pour renouveler le certificat installé par le fabricant (MIC) et obtenir un identifiant unique sécurisé de périphérique (SUDI). Pour plus de détails, voir Avis de terrain. Si vous n'utilisez pas de serveur proxy et que vous utilisez uniquement un pare-feu pour filtrer les URL, ajoutez |
Tous |
|
*.ucmgmt.cisco.com |
Services d’appel Webex |
Control Hub |
|
*.wbx2.com et *.ciscospark.com |
Utilisé pour la sensibilisation au cloud afin de contacter Webex Calling & Services Webex Aware pendant et après l'intégration. Ces services sont nécessaires pour
|
Tous |
|
*.webexapis.com |
Les microservices Webex qui gèrent vos applications Webex App et vos appareils Webex.
|
Tous |
|
*.webexcontent.com |
Services de messagerie Webex liés au stockage général de fichiers, notamment :
|
Services de messagerie Webex Apps. Le stockage de fichiers via webexcontent.com a été remplacé par clouddrive.com en octobre 2019. |
|
*.accompany.com |
Intégration des connaissances sur les personnes |
Applications Webex |
|
Services Webex supplémentaires( Domaines tiers ) | ||
|
*.appdynamics.com *.eum-appdynamics.com |
Suivi des performances, capture des erreurs et des pannes, mesures des sessions. |
Application Webex, application Webex Webex |
|
*.sipflash.com |
Services de gestion des appareils. Mises à jour du firmware et finalités d'intégration sécurisée. |
Applications Webex |
|
*.walkme.com *.walkmeusercontent.com |
Client de guidage des utilisateurs de Webex. Fournit des visites guidées pour l’intégration et l’utilisation pour les nouveaux utilisateurs. Pour plus d'informations concernant Walkme, cliquez ici. |
Applications Webex |
|
*.google.com *.googleapis.com |
Notifications aux applications Webex sur les appareils mobiles (Exemple : nouveau message (lorsque l'appel est pris) Pour les sous-réseaux IP, consultez ces liens. Service Google Firebase Cloud Messaging (FCM) Apple Push Notification Service (APNS)/Service de notification Apple Push Pour APNS, Apple répertorie les sous-réseaux IP de ce service. | Application Webex |
Sous-réseaux IP pour les services d'appels Webex
|
Sous-réseaux IP pour les services d'appel Webex*† | ||
|---|---|---|
|
23.89.0.0/16 |
62.109.192.0/18 |
85.119.56.0/23 |
|
128.177.14.0/24 |
128.177.36.0/24 |
135.84.168.0/21 |
|
139.177.64.0/21 |
139.177.72.0/23 |
144.196.0.0/16 |
|
150.253.128.0/17 |
163.129.0.0/17 |
170.72.0.0/16 |
|
170.133.128.0/18 |
185.115.196.0/22 |
199.19.196.0/23 |
|
199.19.199.0/24 |
199.59.64.0/21 | |
|
Configuration du dispositif et gestion du firmware (périphériques Cisco) | ||
|
3.14.211.49 |
3.20.185.219 |
3.130.87.169 |
|
3.134.166.179 |
52.26.82.54 |
62.109.192.0/18 |
|
72.163.10.96/27 |
72.163.15.64/26 |
72.163.15.128/26 |
|
72.163.24.0/23 |
72.163.10.128/25 |
173.37.146.128/25 |
|
173.36.127.0/26 |
173.36.127.128/26 |
173.37.26.0/23 |
|
173.37.149.96/27 |
192.133.220.0/26 |
192.133.220.64/26 |
|
Configuration de l'application Webex | ||
|
62.109.192.0/18 |
64.68.96.0/19 |
150.253.128.0/17 |
|
207.182.160.0/19 | ||
|
Objet de la connexion | Adresses sources | Ports source | HTTPS et WSS pour la signalisation et la messagerie. | Adresses de destination | Ports de destination | Remarques | |
|---|---|---|---|---|---|---|---|
| Signalisation des appels à Webex Calling (SIP TLS) | Passerelle locale externe (NIC) | 8000-65535 | TCP | Reportez-vous à Sous-réseaux IP pour les services d’appel Webex. | 5062, 8934 |
Ces IPs/ports sont nécessaires pour la signalisation des appels SIP-TLS sortants depuis les passerelles locales, les appareils et les applications Webex App (source) vers Webex Calling Cloud (destination). Port 5062 (requis pour le trunk basé sur un certificat). Et le port 8934 (requis pour le trunk basé sur l'enregistrement) | |
| Périphériques | 5060-5080 | 8934 | |||||
| Série Room | Éphémère | ||||||
| Application Webex | Ephémère (dépend du système d’exploitation) | ||||||
| Signalisation d'appel de Webex Calling (SIP TLS) vers la passerelle locale |
Plage d'adresses d'appel Webex. Consultez la sectionSous-réseaux IP pour les services d'appel Webex | 8934 | TCP | L'adresse IP ou les plages d'adresses IP choisies par le client pour sa passerelle locale | Port ou plage de ports choisis par le client pour sa passerelle locale |
S'applique aux passerelles locales basées sur des certificats. Il est nécessaire d'établir une connexion entre Webex Calling et une passerelle locale. Une passerelle locale basée sur l'enregistrement fonctionne en réutilisant une connexion créée à partir de la passerelle locale. Le port de destination est choisi par le client Configurer les liaisons | |
| Appelez les médias vers Webex Calling (STUN, SRTP/SRTCP, T38, DTLS) | Passerelle locale NIC externe | 8000-48199†* | UDP | Reportez-vous à Sous-réseaux IP pour les services d’appel Webex. |
5004, 9000 (Ports STUN) Audio : 8500-8599 Vidéo : 8600-8699 19560-65535 (SRTP sur UDP) |
| |
| Appareils†* | 19560-19661 | ||||||
| Série de chambres†* | Audio 52050-52099 Vidéo52200-52299 | ||||||
|
Périphériques VG400 ATA | 19560-19849 | ||||||
| Application Webex†* |
Audio : 8500-8599 Vidéo : 8600-8699 | ||||||
|
WebRTC | Éphémère (conformément à la politique du navigateur) | ||||||
| Appelez des médias depuis Webex Calling (SRTP/SRTCP, T38) |
Plage d'adresses d'appel Webex. Consultez la sectionSous-réseaux IP pour les services d'appel Webex | 19560-65535 (SRTP sur UDP) | UDP | Adresse IP ou plage d'adresses IP choisie par le client pour sa passerelle locale | Plage de ports multimédias choisie par le client pour sa passerelle locale |
S'applique aux passerelles locales basées sur des certificats | |
| Signalisation d’appel vers la passerelle RTCP (SIP TLS) | NIC interne de la passerelle locale | 8000-65535 | TCP | Votre RTCP ITSP GW ou Unified CM | Dépend de l’option RTCP (par exemple, typiquement 5060 ou 5061 pour Unified CM) | ||
| Appelez les médias vers la passerelle PSTN (SRTP/SRTCP) | NIC interne de la passerelle locale | 8000-48199†* | UDP | Votre RTCP ITSP GW ou Unified CM | Cela dépend de l'option PSTN (par exemple, généralement 5060 ou 5061 pour Unified CM). | ||
| Configuration du dispositif et gestion du firmware (périphériques Cisco) | Périphériques Webex Calling | Éphémère | TCP |
Consultez la sectionSous-réseaux IP pour les services d'appel Webex | 443, 6970, 80 |
Requis pour les raisons suivantes :
| |
| Configuration de l'application Webex | Applications Webex App | Éphémère | TCP |
Consultez la sectionSous-réseaux IP pour les services d'appel Webex | 443, 8443 | Utilisé pour l'authentification via courtier d'identité, les services de configuration de l'application Webex pour les clients, l'accès Web basé sur un navigateur pour l'autogestion et l'accès à l'interface d'administration. Le port TCP 8443 est utilisé par l'application Webex sur la configuration Cisco Unified CM pour télécharger la configuration. Seuls les clients qui utilisent cette configuration pour se connecter à Webex Calling doivent ouvrir le port. | |
| Synchronisation de l’heure du périphérique (NTP) | Périphériques Webex Calling | 51494 | UDP | Reportez-vous à Sous-réseaux IP pour les services d’appel Webex. | 123 | Ces adresses IP sont nécessaires pour la synchronisation temporelle des périphériques (téléphones MPP, ATA et SPA ATA). | |
|
Résolution du système de noms de domaine (DNS) | Appareils d'appel Webex, application Webex et appareils Webex | Éphémère | UDP et TCP | Défini par l’organisateur | 53 | Utilisé pour les recherches DNS afin de découvrir les adresses IP des services d'appel Webex dans le cloud. Bien que les requêtes DNS classiques soient effectuées via UDP, certaines peuvent nécessiter TCP si les réponses aux requêtes ne peuvent pas être incluses dans des paquets UDP. | |
| Network Time Protocol (NTP) | Application Webex et appareils Webex | 123 | UDP | Défini par l’organisateur | 123 | Synchronisation de l'heure | |
| Cscan | Outil de préqualification de la préparation du réseau Web pour les appels Webex | Éphémère | TCP | Reportez-vous à Sous-réseaux IP pour les services d’appel Webex. | 8934 et 443 | Outil de préqualification de la disponibilité du réseau basé sur le Web pour les appels Webex. Rendez-vous sur cscan.webex.com pour plus d’informations. | |
| UDP | 19569-19760 | ||||||
| Appels Webexsupplémentaires & Services Webex Aware (Tiers) | |||||||
| Services de notifications push APNS et FCM | Applications Webex Calling | Éphémère | TCP |
Veuillez vous référer aux sous-réseaux IP mentionnés sous les liens. | 443, 2197, 5228, 5229, 5230, 5223 | Notifications aux applications Webex sur les appareils mobiles (Exemple : (Lorsque vous recevez un nouveau message ou lorsqu'un appel est pris) | |
-
†*La plage de ports multimédias CUBE est configurable avec plage de ports rtp.
-
†*Ports multimédias pour les périphériques et les applications qui sont attribués dynamiquement dans les plages de ports SRTP. Les ports SRTP sont des ports numérotés pairs, et le port SRTCP correspondant est associé au port numéroté impair suivant.
-
Si une adresse de serveur proxy est configurée pour vos applications et appareils, le trafic de signalisation est envoyé au proxy. Les flux multimédias SRTP sur UDP transitent directement par votre pare-feu au lieu du serveur proxy.
-
Si vous utilisez les services NTP et DNS au sein de votre réseau d'entreprise, ouvrez les ports 53 et 123 dans votre pare-feu.
Taille MTU pour les appels Webex & Services Webex Aware
L'unité de transmission maximale (MTU) est la taille maximale qu'un paquet IP peut transmettre sur une liaison réseau sans nécessiter de fragmentation. Des problèmes peuvent survenir si la MTU n'est pas configurée sur les valeurs par défaut. Webex Calling recommande de conserver la taille MTU par défaut de 1500 octets pour tous les paquets IP sur votre réseau.
Pour les services Webex Calling et Webex Aware, si un paquet nécessite une fragmentation, définissez le bit Don't Fragment (DF) pour nécessiter une communication ICMP.
Qualité du service (QoS)/Type des conditions générales de service (CGU)
Permet d'activer l'étiquetage des paquets provenant du périphérique ou du client local vers la plateforme cloud Webex Calling. La QoS vous permet de prioriser le trafic en temps réel par rapport aux autres types de trafic de données. L'activation de ce paramètre modifie les marquages QoS pour les applications et les périphériques qui utilisent la signalisation et les médias SIP.
| Adresses sources | Type de trafic | Adresses de destination | Ports source | Ports de destination | Classe et valeur DSCP |
|---|---|---|---|---|---|
| Application Webex | Audio |
Consultez les sous-réseaux IP, les domaines et les URL pour les services d'appel Webex. | 8500-8599 | 8500-8599, 19560-65535 | Expédition accélérée (46) |
| Application Webex | Vidéo | 8600-8699 | 8600-8699, 19560-65535 | Livraison assurée 41 (34) | |
| Application Webex | Signalisation | Ephémère (dépend du système d’exploitation) | 8934 | CS0 (0) | |
| Appareils Webex (MPP et salle) | Audio et vidéo | 19560-19661 | 19560-65535 |
Expédition accélérée (46) & Livraison assurée 41 (34) | |
| Périphériques Webex | Signalisation | 5060-5080 | 8934 | Sélecteur de classe 3 (24) |
-
Créez un profil QoS distinct pour l'audio et Video/Share car ils utilisent des plages de ports source différentes pour marquer le trafic différemment.
-
Pour les clients Windows : Pour activer la différenciation des ports sources UDP pour votre organisation, contactez votre équipe commerciale locale. Sans activer cette option, vous ne pouvez pas faire la différence entre l'audio et Video/Share utilisation des stratégies QoS Windows (GPO) car les ports sources sont identiques pour audio/video/share. Pour plus de détails, voir Activer les plages de ports de source multimédia pour l'application Webex
-
Pour les appareils Webex, configurez les modifications des paramètres QoS à partir des paramètres de l'appareil Control Hub. Pour plus de détails, voir Configurer & modifier les paramètres de l'appareil dans Webex-Calling
Réunions/Messagerie Webex - Configuration réseau requise
Pour les clients utilisant la suite de services de collaboration cloud Webex, les produits enregistrés sur le cloud Webex permettent d'intégrer les appareils MPP au cloud Webex pour des services tels que l'historique des appels, la recherche dans l'annuaire, les réunions et la messagerie. Assurez-vous que le Domains/URLs/IP Addresses/Ports mentionnés dans cet article sont les exigences réseau ouvertes pour les services Webex.
Configuration réseau requise pour Webex for Government
Pour les clients qui ont besoin de la liste des domaines, URL, plages d'adresses IP et ports pour les services Webex pour le gouvernement, les informations sont disponibles ici : Configuration réseau requise pour Webex for Government
Configuration réseau requise pour la console Webex Attendant
Pour les clients utilisant la console d'opérateur (réceptionnistes, opérateurs et personnel d'accueil), assurez-vous de… Domains/URLs/IP Addresses/Ports/Protocols sont ouverts Configuration réseau requise pour la console de l'opérateur
Premiers pas avec la passerelle locale d'appel Webex
Pour les clients utilisant la solution Local Gateway avec Webex Calling pour l'interopérabilité entre le réseau téléphonique public commuté (RTPC) sur site et les SBC tiers, consultez l'article Démarrage avec Local Gateway
Références
Pour connaître les nouveautés de Webex Calling, consultez Nouveautés de Webex Calling
Pour connaître les exigences de sécurité relatives aux appels Webex, consultez l'article
Optimisation des médias d'appel Webex avec établissement de connectivité interactive (ICE) Article
Historique des révisions du document
|
Date |
Nous avons apporté les modifications suivantes à cet article |
|---|---|
|
5 décembre 2025 |
Ajout de l'utilisation des sous-réseaux IP, des ports et des protocoles qui sont répertoriés dans la section Sous-réseaux IP pour les services d'appel Webex. |
|
24 octobre 2025 |
Amélioration de la qualité de l'image et correction du lien brisé vers le service Google Firebase Cloud Messaging (FCM). |
|
15 septembre 2025 |
|
|
10 avril 2025 |
Texte ajouté pour souligner la taille MTU pour les services Webex Calling et Webex Aware |
|
27 mars 2025 |
Mise à jour du sous-réseau IP pour les services d'appels Webex 62.109.192.0/18 pour accompagner l'expansion du marché des appels Webex dans la région de l'Arabie saoudite. |
|
21 janvier 2025 |
Ajout de détails concernant l'utilisation de la passerelle de couche application SIP. |
|
8 janvier 2025 |
L'adresse de sous-réseau IP relative à la configuration de l'appareil et à la configuration de l'application Webex a été déplacée vers la section Sous-réseaux IP pour les services d'appel Webex |
|
17 décembre 2024 |
Ajout de la prise en charge de WebRTC pour la spécification Webex Calling Media. |
|
14 novembre 2024 |
Mise à jour de la plage de ports pris en charge pour les flux multimédias d'appel Webex Calling sur les périphériques ATA de la série VG400 |
|
11 novembre 2024 |
Ajout de la plage de ports pris en charge pour les flux multimédias d'appel Webex Calling sur les périphériques ATA de la série VG400. |
|
25 juillet 2024 |
J'ai réintégré le sous-réseau IP 52.26.82.54 car il est nécessaire pour la configuration du périphérique Cisco ATA et la gestion du firmware. |
|
18 juillet 2024 |
Mise à jour avec les détails suivants :
|
|
28 juin 2024 |
Mise à jour de l'utilisation des plages de ports SRTP/SRTCP pour la spécification Webex Calling Media. |
|
11 juin 2024 |
Le domaine « huron-dev.com » a été supprimé car il n'est plus utilisé. |
|
6 mai 2024 |
Mise à jour de l'utilisation des plages de ports SRTP/SRTCP pour la spécification Webex Calling Media. |
|
3 avril 2024 | Mise à jour des sous-réseaux IP pour les services d'appels Webex avec 163.129.0.0/17 pour accompagner l'expansion du marché des appels Webex dans la région indienne. |
|
18 décembre 2023 |
Inclut l'URL sudirenewal.cisco.com et l'exigence de port 80 pour la configuration de l'appareil et la gestion du micrologiciel du renouvellement MIC du téléphone Cisco MPP. |
|
11 décembre 2023 |
Mise à jour des sous-réseaux IP pour les services d'appels Webex afin d'inclure un plus grand nombre d'adresses IP. 150.253.209.128/25 – changé en 150.253.128.0/17 |
|
29 novembre 2023 |
Mise à jour des sous-réseaux IP pour les services d'appels Webex afin d'inclure un plus grand nombre d'adresses IP pour accompagner l'expansion de la région Webex Calling en vue de sa croissance future. 144.196.33.0/25 – changé en 144.196.0.0/16 Les sections relatives aux sous-réseaux IP pour les services d'appel Webex sous Webex Calling (SIP TLS) et aux médias d'appel vers Webex Calling (STUN, SRTP) ont été mises à jour afin de clarifier le trunking basé sur les certificats et les exigences de pare-feu pour la passerelle locale. |
|
14 août 2023 |
Nous avons ajouté les adresses IP suivantes 144.196.33.0/25 et 150.253.156.128/25 pour répondre aux besoins accrus en capacité des services d'appel Edge et Webex. Cette plage d'adresses IP est prise en charge uniquement dans la région des États-Unis. |
|
5 juillet 2023 |
Ajout du lien https://binaries.webex.com pour installer le firmware Cisco MPP. |
|
7 mars 2023 |
Nous avons entièrement remanié l'article pour y inclure :
|
|
5 mars 2023 |
Mise à jour de l'article pour inclure les éléments suivants :
|
|
15 novembre 2022 |
Nous avons ajouté les adresses IP suivantes pour la configuration des périphériques et la gestion du firmware (périphériques Cisco) :
Nous avons supprimé les adresses IP suivantes de la configuration des périphériques et de la gestion du micrologiciel (périphériques Cisco) :
|
|
14 novembre 2022 |
Ajout du sous-réseau IP 170.72.242.0/24 pour le service d'appels Webex. |
|
Le 8 septembre 2022 |
Le firmware Cisco MPP passe à l'utilisation de https://binaries.webex.com comme URL hôte pour les mises à niveau du firmware MPP dans toutes les régions. Ce changement améliore les performances de mise à niveau du microprogramme (firmware). |
|
30 août 2022 |
Suppression de la référence au port 80 dans les lignes de configuration du périphérique et de gestion du firmware (périphériques Cisco), de configuration de l'application et de CScan du tableau des ports, car il n'y a aucune dépendance. |
|
18 août 2022 |
Aucun changement dans la solution. Mise à jour des ports de destination 5062 (requis pour le tronc certificat), 8934 (requis pour le tronc basé sur l’enregistrement) pour la signalisation d’appel Webex Calling (SIP TLS). |
|
26 juillet 2022 |
Ajout de l’adresse IP 54.68.1.225, qui est requise pour la mise à niveau du firmware des périphériques Cisco 840/860. |
|
21 juillet 2022 |
Mise à jour des ports de destination 5062, 8934 pour la signalisation d’Webex Calling (SIP TLS). |
|
14 juillet 2022 |
Ajout des URL permettant un fonctionnement complet des services Webex Aware. Ajout du sous-réseau IP 23.89.154.0/25 pour le service d'appels Webex. |
|
27 juin 2022 |
Mise à jour du domaine et des URL pour Webex Calling services : *.broadcloudpbx.com *.broadcloud.com.au *.broadcloud.eu *.broadcloudpbx.net |
|
15 juin 2022 |
Ajout des ports et des protocoles suivants sous Adresses IP et ports pour Webex Calling services :
Informations mises à jour dans le Webex Meetings/Messaging - Exigences réseau section |
|
24 mai 2022 |
Ajout du sous-réseau IP 52.26.82.54/24 à 52.26.82.54/32 pour le service Webex Calling |
|
6 mai 2022 |
Ajout du sous-réseau IP 52.26.82.54/24 pour Webex Calling service |
|
7 avril 2022 |
Mise à jour de la plage de ports UDP internes et externes de la passerelle locale à 8000-48198† |
|
5 avril 2022 |
Ajout des sous-réseaux IP suivants pour Webex Calling service :
|
|
29 mars 2022 |
Ajout des sous-réseaux IP suivants pour Webex Calling service :
|
|
20 septembre 2021 |
Ajout de 4 nouveaux sous-réseaux IP Webex Calling service :
|
|
2 avril 2021 |
Ajouté *.ciscospark.com sous Domaines et URL pour les services d'appel Webex pour prendre en charge les cas d'utilisation des appels Webex dans l'application Webex. |
|
25 mars 2021 |
Ajout de 6 nouvelles plages d'adresses IP pour activate.cisco.com, effectives à compter du 8 mai 2021.
|
|
5 mars 2020 |
Remplacement des IP discrètes de Webex Calling et des plages d’IP plus petites par des plages simplifiées dans un tableau séparé pour faciliter la compréhension de la configuration du pare-feu. |
|
26 février 2021 |
Ajout de 5004 comme port de destination pour les médias d’appel à Webex Calling (STUN, SRTP) pour prendre en charge la connectivité interactive d’Appelants (ICE) qui sera disponible dans Webex Calling en avril 2021. |
|
22 février 2021 |
Les domaines et les URLs sont maintenant listés dans un tableau séparé. Le tableau des adresses IP et des ports est ajusté afin de regrouper les adresses IP pour les mêmes services. Ajout d'une colonne « Notes » au tableau « Adresses IP et ports » pour faciliter la compréhension des exigences. Déplacement des adresses IP suivantes vers des plages simplifiées pour la configuration des périphériques et la gestion du micrologiciel (périphériques Cisco) :
Ajout des adresses IP suivantes pour la configuration de l'application, car le client Cisco Webex pointe vers un serveur DNS SRV plus récent en Australie en mars 2021.
|
|
21 janvier 2021 |
Nous avons ajouté les adresses IP suivantes à la configuration des périphériques et à la gestion du microprogramme (périphériques Cisco) :
Nous avons supprimé les adresses IP suivantes de la configuration des périphériques et de la gestion du micrologiciel (périphériques Cisco) :
Nous avons ajouté les adresses IP suivantes à la configuration de l'application :
Nous avons supprimé les adresses IP suivantes de la configuration de l'application :
Nous avons supprimé les numéros de port suivants de la configuration de l'application :
Nous avons ajouté les domaines suivants à la configuration de l'application :
|
|
23 décembre 2020 |
Ajout de nouvelles adresses IP de configuration des applications aux images de référence des ports. |
|
22 Décembre 2020 |
Mise à jour de la ligne Configuration des applications dans les tableaux pour inclure les adresses IP suivantes : 135.84.171.154 et 135.84.172.154. Masquez les schémas de réseau jusqu'à ce que ces adresses IP soient ajoutées. |
|
11 décembre 2020 |
Mise à jour des lignes Configuration des périphériques et gestion des micrologiciels (périphériques Cisco) et Configuration des applications pour les domaines canadiens pris en charge. |
|
16 Octobre 2020 |
Mise à jour des entrées de signalisation d’appel et de média avec les adresses IP suivantes :
|
|
23 septembre 2020 |
Sous CScan, remplacement de 199.59.64.156 par 199.59.64.197. |
|
14 août 2020 |
Ajout d’adresses IP supplémentaires pour prendre en charge l’introduction de centres de données au Canada : Signalisation d’appel vers Webex Calling (SIP TLS)–135.84.173.0/25,135.84.174.0/25, 199.19.197.0/24, 199.19.199.0/24 |
|
12 août 2020 |
Ajout d’adresses IP supplémentaires pour prendre en charge l’introduction de centres de données au Canada :
|
|
22 juillet 2020 |
Ajout de l’adresse IP suivante pour prendre en charge l’introduction des centres de données au Canada : 135.84.173.146 |
|
9 juin 2020 |
Nous avons apporté les modifications suivantes à l’entrée CScan :
|
|
11 mars 2020 |
Nous avons ajouté les adresses de domaine et IP suivantes à la configuration de l'application :
Nous avons mis à jour les domaines suivants avec des adresses IP supplémentaires pour la configuration des périphériques et la gestion des micrologiciels :
|
|
27 février 2020 |
Nous avons ajouté le domaine et les ports suivants à la configuration du dispositif et à la gestion du micrologiciel : cloudupgrader.webex.com—443, 6970 |


