As an administrator, use this article to get your bearings with all the information and references to the related articles that you need to set up, maintain, and troubleshoot the Local Gateway.
The local gateway helps you migrate to Webex Calling at your own pace. The local gateway integrates your existing on-premises deployment with Webex Calling. You can also use your existing PSTN connection.
Ensure the following before configuring a Local Gateway for Webex Calling:
-
Knowledge of VoIP, such as SIP and media protocols, and the ability to perform basic troubleshooting.
-
Working understanding of the devices (session border controller) that are configured as a Local Gateway.
-
Required license to operate the session border controller.
-
Knowledge of Cisco Unified Communications Manager (Unified CM) or equivalent PBX deployed on your premises and configured to work with Webex Calling. (In the case of an integration with an on-premises environment.)
The following articles can help you familiarize with the deployment options:
|
Term |
References |
|---|---|
|
Trunks and Route Groups |
For more information, see trunks and route groups in Webex Calling Preferred Architecture. |
|
ByoPSTN, Enterprise Dialing |
Stands for Bring Your Own PSTN. For more information, see PSTN access and on-premises interconnect in Webex Calling Preferred Architecture. |
|
Over the Top (OTT), Webex Edge Connect |
For more information, see Access Connectivity options in Webex Calling Preferred Architecture. |
There are two types of Local Gateway trunking models:
-
Registration-based trunks
-
Certificate-based trunks
These models provide similar functionality, but they differ in scale and device support. Select the right trunking model that meets your requirement.
|
Functionality |
Registration-based |
Certificate-based | ||||
|---|---|---|---|---|---|---|
|
Concurrent calls |
Concurrent calls of up to 250 per trunk. |
Concurrent calls of > 250 per trunk. |
||||
|
Device type |
Supports only Cisco Unified Border Element (CUBE). For more information, see CUBE Platform Support. |
A choice of device types as mentioned in the table Device types supported for certificate based trunking. |
||||
|
Authentication model |
Digest-based authentication model, which relies on a shared username and password used to authenticate registration and calls. |
Certificate-based authentication model. |
||||
|
Network, firewall, and NAT requirements
|
Any NAT or Public IP. Dynamic NAT is preferred since it’s easier for setup and requires less firewall configurations. Requires firewall to allow both ingress and egress traffic (Webex calling to Local Gateway and vice versa). For ingress traffic, inbound pinholes are opened by the firewall based on outbound registration messages.
|
Public internet-facing network including a public IP or Static NAT. Requires firewall to allow both ingress and egress traffic (Webex calling to Local Gateway and vice versa). |
||||
|
Public DNS service requirements |
No specific configuration is required on a public DNS service. |
|
||||
|
CA and certificate requirements |
|
|
||||
|
Onboarding and troubleshooting using a cloud connector |
Supports automated troubleshooting of configuration issues. |
Doesn't support automated troubleshooting of configuration issues. |
|
SBC vendor and model |
Minimum Version |
Open Caveats | ||
|---|---|---|---|---|
|
Cisco—CUBE models listed in Router platform support |
Cisco IOS XE Bengaluru 17.6.1a
|
Cisco ISR 1100 platforms don’t support configuration validation. For a gateway deployed in controller mode with Cisco SD-WAN, the following aren’t supported:
|
|
SBC Vendor and model |
Minimum Version |
Open Caveats |
|---|---|---|
|
Cisco—CUBE models listed in Router platform support |
Cisco IOS XE Cupertino 17.9.1a |
For a gateway deployed in controller mode with Cisco SD-WAN, the following aren’t supported:
|
|
Oracle—AP series |
9.0.0 |
Limitation with ICE interoperability. See Section 9 in Cisco Webex - Oracle SBC integration with Cisco Webex Calling as 3rd party Local Gateway (LGW) solution documentation. |
|
Oracle—VME |
9.0.0 |
Limitation with ICE interoperability. See Section 9 in Cisco Webex - Oracle SBC integration with Cisco Webex Calling as 3rd party Local Gateway (LGW) solution documentation. |
|
Oracle—Oracle SBC on Public Cloud |
9.0.0 |
Limitation with ICE interoperability. See Section 9 in Cisco Webex - Oracle SBC integration with Cisco Webex Calling as 3rd party Local Gateway (LGW) solution documentation. |
|
AudioCodes—Mediant CE & VE |
7.40A.250.440 |
Limitation with ICE interoperability. See Section 2.4.2 of Connecting Webex Calling with AudioCodes SBC Configuration Note. |
|
AudioCodes—Mediant Appliances |
7.40A.250.440 |
Limitation with ICE interoperability. See Section 2.4.2 of Connecting Webex Calling with Audio Codes SBC Configuration Note. |
|
Ribbon—SBC 5000 Series, SBC 7000, and SBC SWe |
10.1 |
Limitation with ICE interoperability. See Caveats section. |
|
Ribbon—SBC SWe Edge |
11.0.2 |
Limitation with ICE interoperability. See workaround solution in Caveats section. |
|
Ribbon—SBC 1000, SBC 2000 |
11.0.1 |
Limitation with ICE interoperability. See workaround solution in Caveats section. |
| anynode—SBC | 4.10 |
Webex Calling supports the deployment of Local Gateways behind NAT. Call behavior may depend on the type of NAT firewall used in your network and the functionality provided by your session border controller. |
The Registration-based and Certificate-based trunking models have different concurrent call capacities, as shown in the following table:
|
Concurrent call requirement) |
Approximate user numbers |
Trunk type Preference |
Minimum link quality |
|---|---|---|---|
|
~ 2000–6500 |
65000 |
Certificate-based |
Interconnect |
|
~ 250–2000 |
20000 |
Certificate-based |
Over the top (OTT) |
|
Up to 250 |
2500 |
Registration-based |
OTT |
Connection qualifications
An OTT and interconnect connection must meet the following link quality conditions:
|
Connection type |
Latency |
Jitter |
Packet loss |
|---|---|---|---|
|
OTT |
100 ms (max) |
100 ms (max) |
0.2% |
|
Interconnect |
30 ms |
5 ms |
Zero packet loss |
| 1 |
Configure trunk from Control Hub. | ||
| 2 |
Configure your device to perform the role of a Local Gateway.
| ||
| 3 |
Confirm that the Local Gateway is active in the Control Hub status. |
If the Local Gateway status isn’t active or there are other issues, refer to the following documents before you contact the support team:
-
Troubleshoot issues with Registration-based Local Gateway deployment from the Control Hub.
-
Troubleshoot issues with Certificate-based Local Gateway deployment from the Control Hub.
When the Local Gateway isn't active, check the trunk status in the Control Hub:
-
Log in to Control Hub using https://admin.webex.com, go to .
-
Select the trunk that you want to check the status.
-
Click Trunk Info.
The following are the different statuses of a certificate-based trunk:
-
Online—Successful connection between all the Webex Calling edge proxies and Local Gateway
-
Offline—Unsuccessful connection between the Webex Calling and Local Gateway
-
Impaired—Unsuccessful connection between at least one Webex Calling edge proxy and Local Gateway
-
Unknown—While establishing a connection between Webex Calling and the recently added Local Gateway
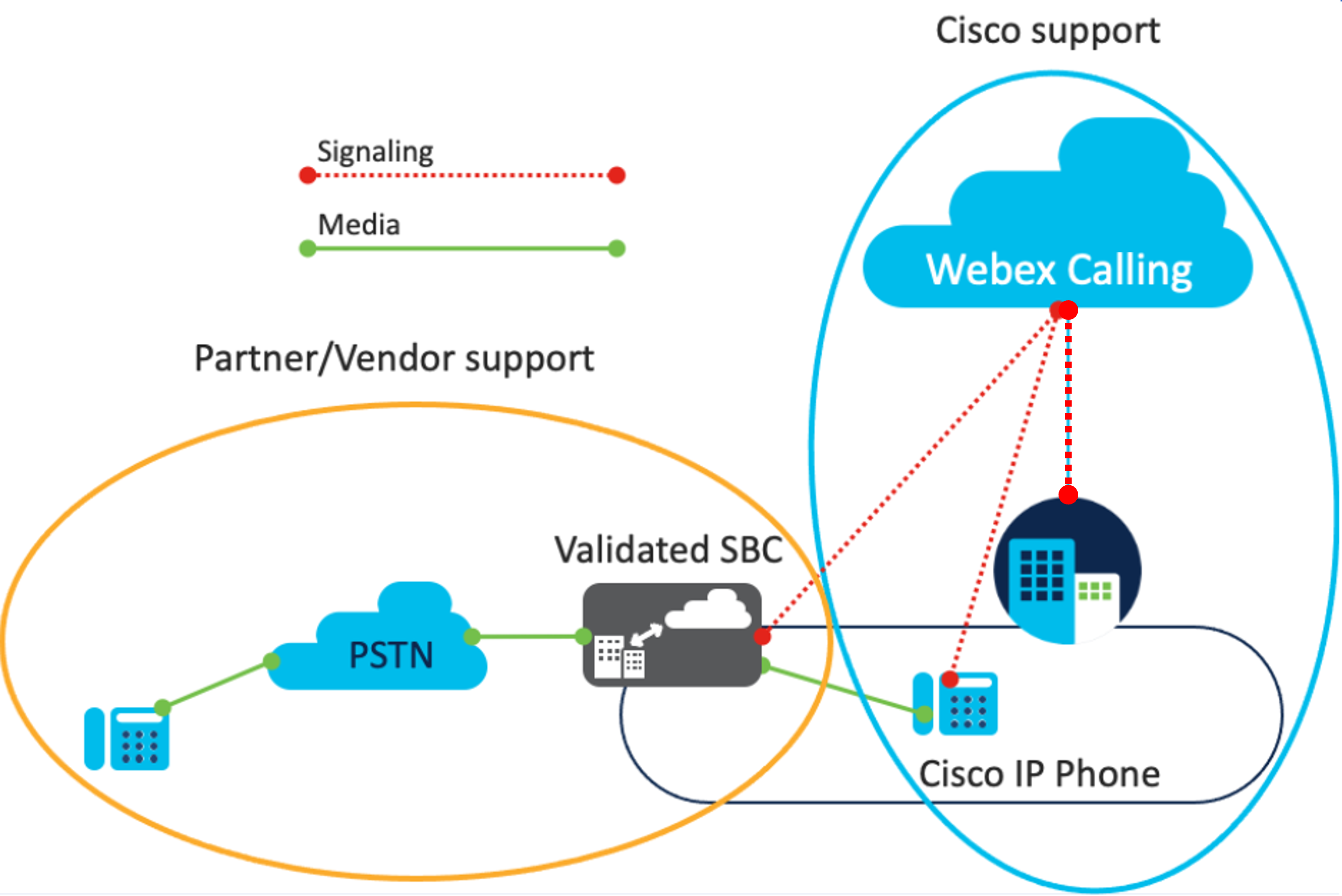
Support from both Cisco and the vendor partner are required for a Webex Calling deployment using a third-party SBC. The following outlines the support details:
-
Webex Calling support:
-
Cisco or partners who use Webex Calling are required to have a support agreement with Cisco in order to get Cisco assistance (TAC support).
-
Cisco provides customer assistance for the Webex Calling up to edge deployment and the Webex Calling registered Cisco IP Phones.
-
-
Vendor support:
-
During deployment, Cisco provides support for the customers or partners that have a validated third-party SBC device and is not responsible for providing assistance for the actual SBC.
-
Cisco isn’t responsible for non-Cisco support cases involving the customer and the SBC vendor. Issues or software defects that arise during deployment can be discussed with the SBC vendor and Cisco.
-