- 홈
- /
- 문서


Webex Calling에 대한 포트 참조 정보
 이 문서에서
이 문서에서 피드백이 있습니까?
피드백이 있습니까?이 문서는 네트워크 관리자, 특히 조직 내에서 Webex Calling 서비스를 사용하는 방화벽 및 프록시 보안 관리자를 대상으로 합니다. 여기에는 네트워크 요구 사항이 설명되어 있으며 전화기, Webex 앱, Webex Calling 서비스에 대한 게이트웨이를 연결하는 데 사용되는 주소, 포트, 프로토콜이 나열되어 있습니다.
성공적인 통화 배포를 위해서는 올바르게 구성된 방화벽과 프록시가 필수적입니다. Webex Calling은 글로벌 서비스이므로 통화 신호에 SIP 및 HTTPS를 사용하고 미디어, 네트워크 연결 및 게이트웨이 연결에 관련 주소와 포트를 사용합니다.
모든 방화벽 구성에 포트를 열 필요가 있는 것은 아닙니다. 하지만 내부-외부 규칙을 실행하는 경우 서비스를 외부로 개방하기 위해 필요한 프로토콜에 대한 포트를 열어야 합니다.
네트워크 주소 변환(NAT)
네트워크 주소 변환(NAT)과 포트 주소 변환(PAT) 기능은 두 네트워크의 경계에 적용되어 주소 공간을 변환하거나 IP 주소 공간의 충돌을 방지합니다.
조직에서는 NAT 또는 PAT 서비스를 제공하는 방화벽 및 프록시와 같은 게이트웨이 기술을 사용하여 개인 IP 주소 공간에 있는 Webex 앱 애플리케이션이나 Webex 장치에 인터넷 액세스를 제공합니다. 이러한 게이트웨이는 내부 앱이나 장치에서 인터넷으로 향하는 트래픽이 하나 이상의 공개적으로 라우팅 가능한 IP 주소에서 오는 것처럼 보이게 합니다.
-
NAT를 배포하는 경우 방화벽에서 인바운드 포트를 열 필요는 없습니다.
-
여러 앱 사용자와 장치가 Webex Calling에 액세스할 때 앱 또는 장치 연결에 필요한 NAT 풀 크기를 확인합니다. & NAT 또는 PAT를 사용하는 Webex 인식 서비스. 포트 고갈을 방지하기 위해 NAT 풀에 적절한 공용 IP 주소가 할당되었는지 확인하세요. 포트 고갈로 인해 내부 사용자와 장치가 Webex Calling 및 Webex Aware 서비스에 연결할 수 없게 됩니다.
-
합리적인 바인딩 기간을 정의하고 NAT 장치에서 SIP를 조작하지 마세요.
-
장치가 제대로 작동하도록 최소 NAT 시간 초과를 구성하세요. 예: Cisco 전화는 1~2분마다 후속 REGISTER 새로 고침 메시지를 보냅니다.
-
네트워크에서 NAT 또는 SPI를 구현하는 경우 연결에 대해 더 긴 시간 제한(최소 30분)을 설정하세요. 이러한 시간 초과를 통해 사용자의 모바일 기기의 배터리 소모를 줄이는 동시에 안정적인 연결이 가능해집니다.
SIP 애플리케이션 계층 게이트웨이
라우터나 방화벽이 SIP를 인식하는 경우, 즉 SIP 애플리케이션 계층 게이트웨이(ALG) 또는 이와 유사한 기능이 활성화되어 있는 경우, 서비스의 정확한 작동을 위해 이 기능을 끄는 것이 좋습니다. 모든 Webex Calling 트래픽은 암호화되지만, 특정 SIP ALG 구현으로 인해 방화벽 통과 문제가 발생할 수 있습니다. 따라서 고품질 서비스를 보장하려면 SIP ALG를 끄는 것이 좋습니다.
특정 장치에서 SIP ALG를 비활성화하는 방법은 해당 제조업체의 설명서를 확인하세요.
Webex Calling에 대한 프록시 지원
조직에서는 네트워크에서 나가고 들어오는 HTTP 트래픽을 검사, 제한 및 제어하기 위해 인터넷 방화벽이나 인터넷 프록시 및 방화벽을 배포합니다. 이를 통해 다양한 형태의 사이버 공격으로부터 네트워크를 보호할 수 있습니다.
프록시는 다음과 같은 여러 가지 보안 기능을 수행합니다.
-
특정 URL에 대한 액세스를 허용하거나 차단합니다.
-
사용자 인증
-
아이피 address/domain/hostname/URI 평판 조회
-
트래픽 복호화 및 검사
프록시 기능을 구성하면 HTTP 프로토콜을 사용하는 모든 애플리케이션에 적용됩니다.
Webex 앱과 Webex 장치 애플리케이션에는 다음이 포함됩니다.
-
Webex 서비스
-
GDS, EDOS 장치 활성화, 프로비저닝과 같은 Cisco Cloud 프로비저닝 플랫폼을 사용한 고객 장치 활성화(CDA) 절차 & Webex 클라우드에 온보딩.
-
인증서 인증
-
펌웨어 업그레이드
-
상태 보고서
-
PRT 업로드
-
XSI 서비스
프록시 서버 주소가 구성된 경우 신호 트래픽만 (HTTP/HTTPS) 프록시 서버로 전송됩니다. SIP를 사용하여 Webex Calling 서비스와 관련 미디어에 등록하는 클라이언트는 프록시로 전송되지 않습니다. 따라서 이러한 클라이언트가 방화벽을 직접 통과하도록 허용하세요.
지원되는 프록시 옵션, 구성 & 인증 유형
지원되는 프록시 유형은 다음과 같습니다.
-
명시적 프록시(검사 또는 비검사) - 클라이언트 앱이나 기기를 명시적 프록시로 구성하여 사용할 서버를 지정합니다.
-
투명 프록시(비검사) - 클라이언트는 특정 프록시 서버 주소를 사용하도록 구성되지 않았으며 비검사 프록시와 함께 작동하기 위해 어떠한 변경도 필요하지 않습니다.
-
투명 프록시(검사) - 클라이언트는 특정 프록시 서버 주소를 사용하도록 구성되지 않았습니다. HTTP 구성을 변경할 필요는 없습니다. 그러나 클라이언트인 앱이나 장치에는 프록시를 신뢰할 수 있도록 루트 인증서가 필요합니다. IT 팀은 검사 프록시를 사용하여 방문할 웹사이트와 허용되지 않는 콘텐츠 유형에 대한 정책을 시행합니다.
다음을 사용하여 Cisco 장치와 Webex 앱에 대한 프록시 주소를 수동으로 구성하세요.
-
플랫폼 OS
-
장치 UI
-
다음과 같은 웹 프록시 메커니즘을 사용하여 자동으로 검색됨:
-
웹 프록시 자동 검색(WPAD) - 웹 프록시 자동 검색 프로토콜
-
프록시 자동 구성(PAC) 파일 - 프록시 자동 구성 파일
-
선호하는 제품 유형을 구성하는 동안 다음 프록시 구성 중에서 선택하세요. & 표의 인증 유형:
|
제품 |
프록시 구성 |
인증 유형 |
|---|---|---|
|
Mac용 Webex |
수동, WPAD, PAC |
인증 없음, 기본, NTLM,† |
|
Windows용 Webex |
수동, WPAD, PAC, GPO |
인증 없음, 기본, NTLM, †, 협상 † |
|
iOS용 Webex |
수동, WPAD, PAC |
인증 없음, 기본, 다이제스트, NTLM |
|
Webex Android용 |
수동, PAC |
인증 없음, 기본, 다이제스트, NTLM |
|
Webex 웹 앱 |
OS를 통해 지원됨 |
인증 없음, 기본, 다이제스트, NTLM, 협상 † |
|
Webex 장치 |
WPAD, PAC 또는 수동 |
인증 없음, 기본, 다이제스트 |
|
Cisco IP 전화기 |
수동, WPAD, PAC |
인증 없음, 기본, 다이제스트 |
|
Webex 비디오 메시 노드 |
수동 |
인증 없음, 기본, 다이제스트, NTLM |
표의 범례:
-
†Mac NTLM 인증 - 컴퓨터가 도메인에 로그인할 필요가 없으며 사용자에게 암호를 입력하라는 메시지가 표시됩니다.
-
†Windows NTLM 인증 - 컴퓨터가 도메인에 로그인한 경우에만 지원됩니다.
-
협상 †- NTLM 대체 인증을 사용한 Kerberos.
-
Cisco Webex Board, Desk 또는 Room Series 장치를 프록시 서버에 연결하려면 Board, Desk 또는 Room Series 장치를 프록시 서버에 연결을 참조하세요.
-
Cisco IP 전화의 경우 프록시 서버 및 설정을 구성하기 위한 예로 프록시 서버 설정 을 참조하세요.
No Authentication의 경우 인증을 지원하지 않는 프록시 주소로 클라이언트를 구성합니다. Proxy Authentication를 사용하는 경우 유효한 자격 증명으로 구성하세요. 웹 트래픽을 검사하는 프록시는 웹 소켓 연결을 방해할 수도 있습니다. 이 문제가 발생하면 트래픽을 검사하지 않는 것을 우회합니다. *.Webex.com 문제를 해결할 수도 있습니다. 이미 다른 항목이 표시되면 마지막 항목 뒤에 세미콜론을 추가한 다음 Webex 예외를 입력합니다.
Windows OS용 프록시 설정
Microsoft Windows는 프록시 구성을 허용하는 HTTP 트래픽(WinINet 및 WinHTTP)에 대한 두 가지 네트워크 라이브러리를 지원합니다. WinINet은 WinHTTP의 상위 집합입니다.
-
WinInet은 단일 사용자, 데스크톱 클라이언트 애플리케이션용으로 설계되었습니다.
-
WinHTTP는 주로 다중 사용자, 서버 기반 애플리케이션을 위해 설계되었습니다.
두 가지 중에서 선택할 때 프록시 구성 설정으로 WinINet을 선택하세요. 자세한 내용은 wininet-vs-winhttp를 참조하세요.
자세한 내용은 회사 네트워크에 있는 동안 Webex에 액세스할 수 있는 허용 도메인 목록 구성 을 참조하세요.
-
사람들이 사전 정의된 도메인 목록의 계정을 사용해서만 애플리케이션에 로그인하도록 보장합니다.
-
프록시 서버를 사용하여 요청을 인터셉트하고 허용되는 도메인으로 제한합니다.
프록시 검사 및 인증서 핀 고정하기
Webex 앱과 장치는 TLS 세션을 설정할 때 서버의 인증서를 검증합니다. 인증서 발급자 및 디지털 서명 등을 확인하는 인증서 검사는 루트 인증서까지의 인증서 체인을 검증하는 데 의존합니다. 유효성 검사를 수행하기 위해 Webex 앱과 장치는 운영 체제 신뢰 저장소에 설치된 신뢰할 수 있는 루트 CA 인증서 세트를 사용합니다.
TLS 검사 프록시를 배포하여 Webex Calling 트래픽을 가로채고, 해독하고, 검사한 경우 프록시가 제시하는 인증서(Webex 서비스 인증서 대신)가 인증 기관에서 서명한 인증서인지, 그리고 루트 인증서가 Webex 앱이나 Webex 장치의 신뢰 저장소에 설치되어 있는지 확인하세요.
-
Webex 앱의 경우 - 장치의 운영 체제에서 프록시가 인증서에 서명하는 데 사용되는 CA 인증서를 설치합니다.
-
Webex Room 장치 및 Cisco 멀티플랫폼 IP 전화기의 경우 TAC 팀에 서비스 요청을 열어 CA 인증서를 설치하세요.
이 표는 프록시 서버에서 TLS 검사를 지원하는 Webex 앱 및 Webex 장치를 보여줍니다.
|
제품 |
TLS 검사에 대해 사용자 정의 신뢰할 수 있는 CA를 지원함 |
|---|---|
|
Webex 앱(Windows, Mac, iOS, Android, 웹) |
예 |
|
Webex Room 장치 |
예 |
|
Cisco IP 멀티플랫폼(MPP) 전화기 |
예 |
방화벽 구성
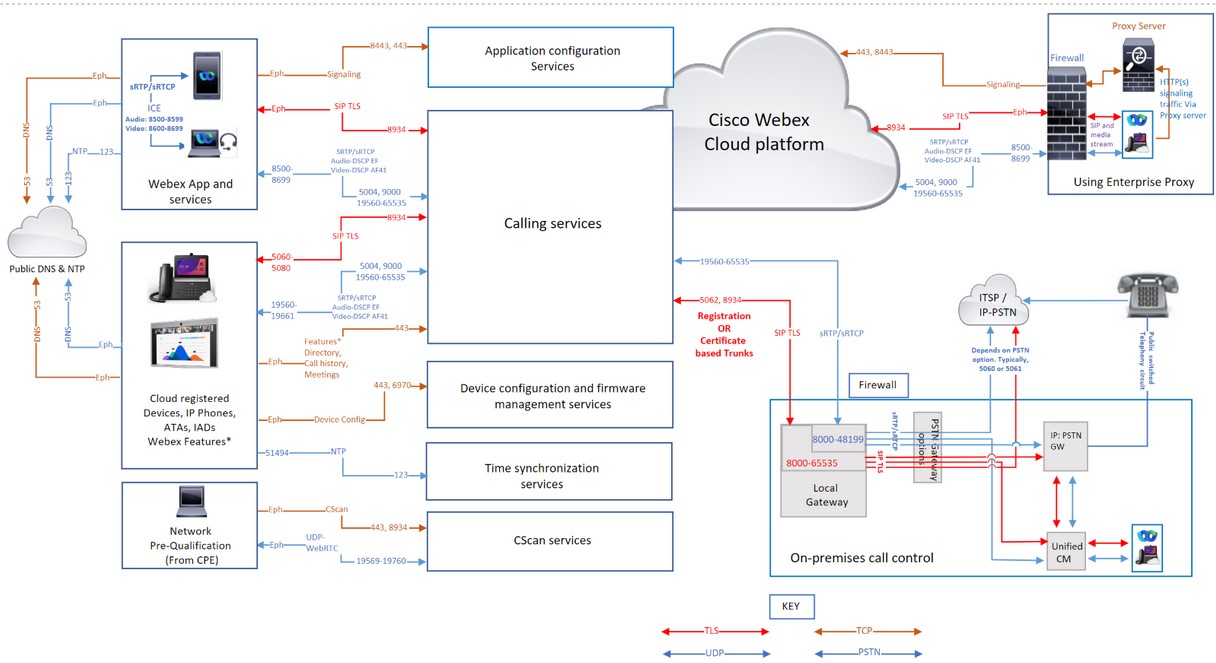
Cisco는 보안된 Cisco 및 Amazon Web Services(AWS) 데이터 센터에서 Webex Calling 및 Webex Aware 서비스를 지원합니다. Amazon은 Cisco에서만 사용할 수 있도록 자사의 IP 서브넷을 예약했으며, AWS 가상 사설 클라우드 내에서 이러한 서브넷에 위치한 서비스를 보호했습니다.
방화벽을 구성하여 기기, 앱 애플리케이션, 인터넷 연결 서비스의 통신을 허용하고 해당 기능을 제대로 수행할 수 있도록 하세요. 이 구성을 사용하면 지원되는 모든 Webex Calling 및 Webex Aware 클라우드 서비스, 도메인 이름, IP 주소, 포트 및 프로토콜에 액세스할 수 있습니다.
Webex Calling 및 Webex Aware 서비스가 올바르게 작동하도록 다음 항목을 허용 목록에 추가하거나 액세스를 개방하세요.
-
그만큼 URLs/Domains Webex Calling 서비스의 도메인 및 URL섹션에 언급됨
-
Webex Calling 서비스의 IP 서브넷 섹션에 나열된 IP 서브넷, 포트 및 프로토콜은 통화 신호, Webex Calling과의 미디어 트래픽, NTP(네트워크 시간 프로토콜) 동기화, 해당 IP 서브넷에 대한 CScan 네트워크 준비 테스트를 포함한 여러 목적으로 활용됩니다.
-
귀하의 조직에서 Webex Meetings, Messaging, Webex Attendant Console 및 기타 관련 서비스를 포함한 Webex Suite 클라우드 협업 서비스를 사용하는 경우 Webex 서비스의 네트워크 요구 사항 및 Attendant 콘솔의 네트워크 요구 사항 문서에 지정된 IP 서브넷, 도메인 및 URL이 네트워크를 통해 허용되는지 확인하세요. 이는 Webex 서비스의 적절한 연결성과 기능을 보장하는 데 필요합니다.
방화벽만 사용하는 경우 IP 주소만을 사용하여 Webex Calling 트래픽을 필터링하는 것은 지원되지 않습니다. 일부 IP 주소 풀은 동적이며 언제든지 변경될 수 있기 때문입니다. 정기적으로 규칙을 업데이트하세요. 방화벽 규칙 목록을 업데이트하지 않으면 사용자 경험에 영향을 미칠 수 있습니다. Cisco는 특정 지역이나 클라우드 서비스 제공업체를 기준으로 IP 주소 하위 집합을 필터링하는 것을 지지하지 않습니다. 지역별로 필터링하면 통화 경험이 심각하게 저하될 수 있습니다.
Cisco에서는 동적으로 변경되는 IP 주소 풀을 유지하지 않으므로 이 문서에서는 나열하지 않았습니다.
방화벽이 지원하지 않는 경우 Domain/URL 필터링을 한 다음 Enterprise Proxy 서버 옵션을 사용하세요. 이 옵션 filters/allows ~에 의해 URL/domain 방화벽으로 전달하기 전에 프록시 서버에서 Webex Calling 및 Webex Aware 서비스로 전송되는 HTTP 신호 트래픽을 확인합니다.
통화 미디어에 대한 포트 및 IP 서브넷 필터링을 사용하여 트래픽을 구성할 수 있습니다. 미디어 트래픽은 인터넷에 직접 접속해야 하므로 신호 트래픽에 대한 URL 필터링 옵션을 선택하세요.
Webex Calling의 경우 UDP는 미디어를 위한 Cisco의 기본 전송 프로토콜이며 UDP를 통한 SRTP만 사용할 것을 권장합니다. 프로덕션 환경에서는 Webex Calling에서 미디어의 전송 프로토콜로 TCP 및 TLS가 지원되지 않습니다. 이러한 프로토콜의 연결 지향적 특성은 손실이 있는 네트워크에서 미디어 품질에 영향을 미칩니다. 전송 프로토콜에 관한 질문이 있는 경우 지원 티켓을 제출하세요.
Webex Calling 서비스의 도메인 및 URL
에이 * URL의 시작 부분에 표시됨(예: *.webex.com) 최상위 도메인과 모든 하위 도메인의 서비스에 액세스할 수 있음을 나타냅니다.
|
도메인 / URL |
설명 |
해당 도메인 / URL을 사용하는 Webex 앱 및 장치 |
|---|---|---|
|
Cisco Webex 서비스 | ||
|
*.broadcloudpbx.com |
Control Hub에서 통화 관리 포털로의 크로스 런칭을 위한 Webex 인증 마이크로 서비스. |
Control Hub |
|
*.broadcloud.com.au |
호주의 Webex Calling 서비스. |
모두 |
|
*.broadcloud.eu |
유럽의 Webex Calling 서비스. |
모두 |
|
*.broadcloudpbx.net |
Calling 클라이언트 구성 및 관리 서비스. |
Webex 앱 |
|
*.webex.com *.cisco.com |
코어 Webex 통화 & Webex Aware 서비스
휴대폰이 처음으로 네트워크에 연결되거나 DHCP 옵션이 설정되지 않은 공장 초기화 이후에 연결되면, 제로 터치 프로비저닝을 위해 장치 활성화 서버에 접속합니다. 새로운 전화기는 activate.cisco.com을 사용하고 11.2(1) 이전 펌웨어 릴리스가 있는 전화기는 프로비저닝을 위해 webapps.cisco.com을 계속 사용합니다. binaries.webex.com에서 장치 펌웨어 및 로캘 업데이트를 다운로드하세요. 12.0.3 버전보다 이전 버전의 Cisco Multiplatform 전화기(MPP)가 포트 80을 통해 sudirenewal.cisco.com 에 액세스하여 제조업체 설치 인증서(MIC)를 갱신하고 보안 고유 장치 식별자(SUDI)를 갖도록 허용합니다. 자세한 내용은 필드 공지를 참조하세요. 프록시 서버를 사용하지 않고 방화벽만 사용하여 URL을 필터링하는 경우 |
모두 |
|
*.ucmgmt.cisco.com |
Webex Calling 서비스 |
Control Hub |
|
*.wbx2.com 및 *.ciscospark.com |
Webex Calling에 접근하기 위한 클라우드 인식에 사용됨 & 온보딩 중 및 온보딩 후의 Webex Aware 서비스. 이러한 서비스는 다음에 필요합니다.
|
모두 |
|
*.webexapis.com |
Webex 앱 애플리케이션과 Webex 장치를 관리하는 Webex 마이크로서비스입니다.
|
모두 |
|
*.webexcontent.com |
다음을 포함한 일반 파일 저장과 관련된 Webex 메시징 서비스:
|
Webex 앱 메시징 서비스. 2019년 10월 webexcontent.com을 이용한 파일 저장은 clouddrive.com으로 대체되었습니다. |
|
*.accompany.com |
People Insights 통합 |
Webex 앱 |
|
추가 Webex 관련 서비스 (타사 도메인) | ||
|
*.appdynamics.com *.eum-appdynamics.com |
성능 추적, 오류 및 충돌 캡처, 세션 메트릭스. |
Webex 앱, Webex 웹 앱 |
|
*.sipflash.com |
장치 관리 서비스. 펌웨어 업그레이드 및 보안 온보딩 목적. |
Webex 앱 |
|
*.walkme.com *.walkmeusercontent.com |
Webex 앱 사용자 안내 클라이언트. 새로운 사용자에게 등록 및 사용 투어를 제공합니다. WalkMe에 대한 자세한 정보는 여기를 클릭하십시오. |
Webex 앱 |
|
*.google.com *.googleapis.com |
모바일 기기의 Webex 앱에 대한 알림(예: (전화가 연결되면 새 메시지가 전송됩니다) IP 서브넷의 경우 다음 링크를 참조하세요. Google Firebase 클라우드 메시징(FCM) 서비스 Apple Push Notification Service (APNS) APNS의 경우 Apple은 이 서비스에 대한 IP 서브넷을 나열합니다. | Webex 앱 |
Webex Calling 서비스를 위한 IP 서브넷
|
Webex Calling 서비스의 IP 서브넷*† | ||
|---|---|---|
|
23.89.0.0/16 |
62.109.192.0/18 |
85.119.56.0/23 |
|
128.177.14.0/24 |
128.177.36.0/24 |
135.84.168.0/21 |
|
139.177.64.0/21 |
139.177.72.0/23 |
144.196.0.0/16 |
|
150.253.128.0/17 |
163.129.0.0/17 |
170.72.0.0/16 |
|
170.133.128.0/18 |
185.115.196.0/22 |
199.19.196.0/23 |
|
199.19.199.0/24 |
199.59.64.0/21 | |
|
장치 구성 및 펌웨어 관리 (Cisco 장치) | ||
|
3.14.211.49 |
3.20.185.219 |
3.130.87.169 |
|
3.134.166.179 |
52.26.82.54 |
62.109.192.0/18 |
|
72.163.10.96/27 |
72.163.15.64/26 |
72.163.15.128/26 |
|
72.163.24.0/23 |
72.163.10.128/25 |
173.37.146.128/25 |
|
173.36.127.0/26 |
173.36.127.128/26 |
173.37.26.0/23 |
|
173.37.149.96/27 |
192.133.220.0/26 |
192.133.220.64/26 |
|
Webex 앱 구성 | ||
|
62.109.192.0/18 |
64.68.96.0/19 |
150.253.128.0/17 |
|
207.182.160.0/19 | ||
|
연결 목적 | 소스 주소 | 소스 포트 | 프로토콜 | 대상 주소 | 대상 포트 | 메모 | |
|---|---|---|---|---|---|---|---|
| Webex Calling에 대한 통화 시그널링 (SIP TLS) | 로컬 게이트웨이 외부 (NIC) | 8000-65535 | TCP | Webex Calling 서비스용 IP 서브넷을 참조하십시오. | 5062, 8934 |
이것들 IPs/ports 로컬 게이트웨이, 장치 및 Webex 앱 애플리케이션(소스)에서 Webex Calling Cloud(대상)로의 아웃바운드 SIP-TLS 통화 신호에 필요합니다. 포트 5062(인증서 기반 트렁크에 필요). 그리고 포트 8934(등록 기반 트렁크에 필요) | |
| 장치 | 5060-5080 | 8934 | |||||
| Room 시리즈 | 사용 후 삭제 | ||||||
| Webex 앱 | 임시 (OS 종속) | ||||||
| Webex Calling(SIP TLS)에서 로컬 게이트웨이로의 호출 신호 |
Webex Calling 주소 범위. Webex Calling 서비스의 IP 서브넷을 참조하세요. | 8934 | TCP | 고객이 로컬 게이트웨이에 대해 선택한 IP 또는 IP 범위 | 고객이 로컬 게이트웨이에 대해 선택한 포트 또는 포트 범위 |
인증서 기반 로컬 게이트웨이에 적용됩니다. Webex Calling에서 로컬 게이트웨이로의 연결을 설정해야 합니다. 등록 기반 로컬 게이트웨이는 로컬 게이트웨이에서 생성된 연결을 재사용하는 방식으로 작동합니다. 목적지 포트는 고객이 선택합니다 트렁크 구성 | |
| Webex Calling(STUN,)으로 미디어 호출 SRTP/SRTCP, T38, DTLS) | 로컬 게이트웨이 외부 NIC | 8000-48199†* | UDP | Webex Calling 서비스용 IP 서브넷을 참조하십시오. |
5004, 9000(STUN 포트) 오디오: 8500-8599 비디오: 8600-8699 19560-65535(UDP를 통한 SRTP) |
| |
| 장치†* | 19560-19661 | ||||||
| 룸 시리즈†* | 오디오 52050-52099 비디오52200-52299 | ||||||
|
VG400 ATA 장치 | 19560-19849 | ||||||
| Webex 앱†* |
오디오: 8500-8599 비디오: 8600-8699 | ||||||
|
WebRTC | 일시적(브라우저 정책에 따라) | ||||||
| Webex Calling에서 미디어 통화 (SRTP/SRTCP, T38) |
Webex Calling 주소 범위. Webex Calling 서비스의 IP 서브넷을 참조하세요. | 19560-65535(UDP를 통한 SRTP) | UDP | 고객이 로컬 게이트웨이에 대해 선택한 IP 또는 IP 범위 | 고객이 로컬 게이트웨이에 대해 선택한 미디어 포트 범위 |
인증서 기반 로컬 게이트웨이에 적용됩니다. | |
| PSTN 게이트웨이에 대한 통화 시그널링 (SIP TLS) | 로컬 게이트웨이 내부 NIC | 8000-65535 | TCP | 귀하의 ITSP PSTN GW 또는 Unified CM | PSTN 옵션에 따라 달라짐 (예: 일반적으로 Unified CM의 5060 또는 5061) | ||
| PSTN 게이트웨이로 미디어 호출 (SRTP/SRTCP) | 로컬 게이트웨이 내부 NIC | 8000-48199†* | UDP | 귀하의 ITSP PSTN GW 또는 Unified CM | PSTN 옵션에 따라 다릅니다(예: 일반적으로 Unified CM의 경우 5060 또는 5061) | ||
| 장치 구성 및 펌웨어 관리 (Cisco 장치) | Webex Calling 장치 | 임시 | TCP |
Webex Calling 서비스의 IP 서브넷을 참조하세요. | 443, 6970, 80 |
다음과 같은 이유로 필요합니다.
| |
| Webex 앱 구성 | Webex 앱 애플리케이션 | 임시 | TCP |
Webex Calling 서비스의 IP 서브넷을 참조하세요. | 443, 8443 | ID 브로커 인증, 클라이언트를 위한 Webex 앱 구성 서비스, 셀프 케어를 위한 브라우저 기반 웹 액세스 및 관리 인터페이스 액세스에 사용됩니다. TCP 포트 8443은 Cisco Unified CM 설정의 Webex 앱에서 구성을 다운로드하는 데 사용됩니다. Webex Calling에 연결하기 위해 설정을 사용하는 고객만 포트를 열어야 합니다. | |
| 장치 시간 동기화 (NTP) | Webex Calling 장치 | 51494 | UDP | Webex Calling 서비스용 IP 서브넷을 참조하십시오. | 123 | 이 IP 주소는 장치(MPP 전화, ATAS 및 SPA ATAS)의 시간 동기화에 필요합니다. | |
|
도메인 이름 시스템(DNS) 확인 | Webex 통화 장치, Webex 앱 및 Webex 장치 | 임시 | UDP 및 TCP | 호스트가 정의함 | 53 | 클라우드에서 Webex Calling 서비스의 IP 주소를 찾기 위한 DNS 조회에 사용됩니다. 일반적인 DNS 조회는 UDP를 통해 이루어지지만, 쿼리 응답이 UDP 패킷에 맞지 않을 경우 TCP가 필요할 수도 있습니다. | |
| 네트워크 시간 프로토콜(NTP) | Webex 앱 및 Webex 장치 | 123 | UDP | 호스트가 정의함 | 123 | 시간 동기화 | |
| CScan | Webex Calling을 위한 웹 기반 네트워크 준비 사전 자격 평가 도구 | 임시 | TCP | Webex Calling 서비스용 IP 서브넷을 참조하십시오. | 8934와 443 | Webex Calling을 위한 웹 기반 네트워크 준비 사전 자격 심사 도구입니다. 자세한 정보는 cscan.webex.com을 참조하십시오. | |
| UDP | 19569-19760 | ||||||
| 추가 Webex 통화 & Webex Aware 서비스 (타사) | |||||||
| 푸시 알림 APNS 및 FCM 서비스 | Webex Calling 응용프로그램 | 임시 | TCP |
링크 아래에 언급된 IP 서브넷을 참조하세요. | 443, 2197, 5228, 5229, 5230, 5223 | 모바일 기기의 Webex 앱에 대한 알림(예: 새로운 메시지를 받거나 전화에 응답할 때) | |
-
†*CUBE 미디어 포트 범위는 rtp-port 범위로 구성할 수 있습니다.
-
†*SRTP 포트 범위에 동적으로 할당되는 장치 및 애플리케이션에 대한 미디어 포트입니다. SRTP 포트는 짝수 포트이고, 해당 SRTCP 포트는 연속된 홀수 포트에 할당됩니다.
-
앱과 기기에 프록시 서버 주소가 구성된 경우 신호 트래픽이 프록시로 전송됩니다. UDP를 통한 SRTP를 통해 전송된 미디어는 프록시 서버 대신 방화벽으로 직접 전달됩니다.
-
회사 네트워크 내에서 NTP 및 DNS 서비스를 사용하는 경우 방화벽을 통해 포트 53 및 123을 열어주세요.
Webex Calling의 MTU 크기 & Webex Aware 서비스
최대 전송 단위(MTU)는 IP 패킷이 조각화 없이 네트워크 링크를 통해 전송할 수 있는 최대 크기입니다. MTU가 기본값으로 설정되지 않으면 문제가 발생할 수 있습니다. Webex Calling에서는 네트워크의 모든 IP 패킷에 대해 기본 MTU 크기를 1500바이트로 유지할 것을 권장합니다.
Webex Calling 및 Webex Aware 서비스의 경우 패킷을 조각화해야 하는 경우 ICMP 통신이 필요하도록 DF(조각화 안 함) 비트를 설정합니다.
서비스 품질 (QoS)/Type 서비스 약관(ToS)
로컬 장치 또는 클라이언트에서 Webex Calling 클라우드 플랫폼으로 패킷에 태그를 지정할 수 있습니다. QoS를 사용하면 다른 데이터 트래픽보다 실시간 트래픽을 우선시할 수 있습니다. 이 설정을 활성화하면 SIP 신호와 미디어를 사용하는 앱과 장치에 대한 QoS 표시가 수정됩니다.
| 소스 주소 | 교통 유형 | 대상 주소 | 소스 포트 | 대상 포트 | DSCP 클래스 및 값 |
|---|---|---|---|---|---|
| Webex 앱 | 오디오 |
Webex Calling 서비스에 대한 IP 서브넷, 도메인 및 URL을 참조하세요. | 8500-8599 | 8500-8599, 19560-65535 | 긴급 운송(46) |
| Webex 앱 | 비디오 | 8600-8699 | 8600-8699, 19560-65535 | 확실한 운송 41(34) | |
| Webex 앱 | 시그널링 | 임시 (OS 종속) | 8934 | CS0 (0) | |
| Webex 장치(MPP 및 Room) | 오디오 및 비디오 | 19560-19661 | 19560-65535 |
긴급 운송(46) & 확실한 운송 41(34) | |
| Webex 장치 | 시그널링 | 5060-5080 | 8934 | 클래스 선택기 3(24) |
-
오디오 및 별도의 QoS 프로필을 만듭니다. Video/Share 트래픽을 다르게 표시하기 위해 서로 다른 소스 포트 범위를 사용하기 때문입니다.
-
Windows 클라이언트의 경우: 귀하의 조직에서 UDP 소스 포트 차별화를 활성화하려면 현지 계정 팀에 문의하세요. 활성화하지 않으면 오디오와 오디오를 구별할 수 없습니다. Video/Share 소스 포트가 동일하기 때문에 Windows QoS 정책(GPO)을 사용합니다. audio/video/share. 자세한 내용은 Webex 앱에 대한 미디어 소스 포트 범위 활성화를 참조하세요.
-
Webex 장치의 경우 Control Hub 장치 설정에서 QoS 설정 변경 사항을 구성합니다. 자세한 내용은 구성을 참조하세요. & Webex-Calling에서 장치 설정 수정
Webex Meetings/Messaging - 네트워크 요구 사항
클라우드 협업 서비스인 Webex Suite를 사용하는 고객의 경우, Webex 클라우드 등록 제품을 사용하면 통화 기록, 디렉토리 검색, 회의, 메시징 등의 서비스를 위해 MPP 장치를 Webex 클라우드에 온보딩할 수 있습니다. 다음을 확인하십시오. Domains/URLs/IP Addresses/Ports 이 문서에 언급된 내용은 Webex 서비스에 대한 네트워크 요구 사항에 대한 공개 내용입니다.
정부용 Webex 네트워크 요구 사항
정부 서비스용 Webex에 대한 도메인, URL, IP 주소 범위 및 포트 목록이 필요한 고객은 다음에서 정보를 찾을 수 있습니다. Webex for Government의 네트워크 요구 사항
Webex Attendant 콘솔의 네트워크 요구 사항
안내원, 안내원, 교환원 기능을 사용하는 고객의 경우, Domains/URLs/IP Addresses/Ports/Protocols 열려 있습니다 참석자 콘솔에 대한 네트워크 요구 사항
Webex Calling 로컬 게이트웨이 시작하기
Webex Calling과 함께 로컬 게이트웨이 솔루션을 사용하여 구내 기반 PSTN 및 타사 SBC 상호 운용성을 구현하는 고객의 경우 로컬 게이트웨이 시작하기문서를 읽어보세요.
참조
Webex Calling의 새로운 기능을 알아보려면 Webex Calling의 새로운 기능을 참조하세요.
Webex Calling의 보안 요구 사항은 문서를 참조하세요.
ICE(Interactive Connectivity Establishment)를 통한 Webex Calling 미디어 최적화 기사
문서 개정 내역
|
날짜 |
이 문서에 다음 변경 사항을 적용했습니다. |
|---|---|
|
2025년 12월 5일 |
Webex Calling 서비스의 IP 서브넷섹션에 나열된 IP 서브넷, 포트 및 프로토콜의 사용법이 추가되었습니다. |
|
2025년 10월 24일 |
Google Firebase Cloud Messaging(FCM) 서비스에 대한 이미지 품질을 개선하고 끊어진 링크를 수정했습니다. |
|
2025년 9월 15일 |
|
|
2025년 4월 10일 |
Webex Calling 및 Webex Aware 서비스의 MTU 크기를 강조하기 위한 텍스트가 포함되었습니다. |
|
2025년 3월 27일 |
Webex Calling 서비스에 대한 IP 서브넷을 업데이트했습니다. 62.109.192.0/18 사우디 아라비아 지역의 Webex Calling 시장 확장에 대응하기 위해. |
|
2025년 1월 21일 |
SIP 애플리케이션 계층 게이트웨이 사용에 대한 세부 정보가 추가되었습니다. |
|
2025년 1월 8일 |
장치 구성 및 Webex 앱 구성과 관련된 IP 서브넷 주소를 Webex Calling 서비스용 IP 서브넷 섹션으로 이동했습니다. |
|
2024년 12월 17일 |
Webex Calling Media 사양에 대한 WebRTC 지원이 추가되었습니다. |
|
2024년 11월 14일 |
VG400 시리즈 ATA 장치에 대한 Webex Calling 통화 미디어의 지원 포트 범위가 업데이트되었습니다. |
|
2024년 11월 11일 |
VG400 시리즈 ATA 장치에 대한 Webex Calling 통화 미디어에 지원되는 포트 범위가 추가되었습니다. |
|
2024년 7월 25일 |
Cisco ATA 장치 구성 및 펌웨어 관리에 필요하므로 52.26.82.54 IP 서브넷을 다시 추가했습니다. |
|
2024년 7월 18일 |
다음 세부정보가 업데이트되었습니다.
|
|
2024년 6월 28일 |
Webex Calling Media 사양에 대한 SRTP/SRTCP 포트 범위 사용을 업데이트했습니다. |
|
2024년 6월 11일 |
사용되지 않는 "huron-dev.com" 도메인을 제거했습니다. |
|
2024년 5월 6일 |
Webex Calling Media 사양에 대한 SRTP/SRTCP 포트 범위 사용을 업데이트했습니다. |
|
2024년 4월 3일 | Webex Calling 서비스에 대한 IP 서브넷을 업데이트했습니다. 163.129.0.0/17 인도 지역의 Webex Calling 시장 확장에 대응하기 위해. |
|
2023년 12월 18일 |
Cisco MPP 전화기의 MIC 갱신을 위한 장치 구성 및 펌웨어 관리를 위해 sudirenewal.cisco.com URL 및 포트 80 요구 사항이 포함되었습니다. |
|
2023년 12월 11일 |
더 많은 IP 주소를 포함하도록 Webex Calling 서비스의 IP 서브넷을 업데이트했습니다. 150.253.209.128/25 – 변경됨 150.253.128.0/17 |
|
2023년 11월 29일 |
향후 성장을 위해 Webex Calling 지역 확장을 수용할 수 있도록 더 많은 IP 주소를 포함하도록 Webex Calling 서비스의 IP 서브넷을 업데이트했습니다. 144.196.33.0/25 – 변경됨 144.196.0.0/16 인증서 기반 트렁킹과 로컬 게이트웨이에 대한 방화벽 요구 사항에 대한 명확성을 위해 Webex Calling(SIP TLS) 및 Webex Calling에 대한 통화 미디어(STUN, SRTP) 섹션의 Webex Calling 서비스용 IP 서브넷이 업데이트되었습니다. |
|
2023년 8월 14일 |
다음 IP 주소를 추가했습니다. 144.196.33.0/25 그리고 150.253.156.128/25 Edge 및 Webex 통화 서비스에 대한 증가된 용량 요구 사항을 지원합니다. 이 IP 범위는 미국 지역에서만 지원됩니다. |
|
2023년 7월 5일 |
Cisco MPP 펌웨어를 설치하기 위한 링크 https://binaries.webex.com 를 추가했습니다. |
|
2023년 3월 7일 |
우리는 다음 내용을 포함하도록 전체 기사를 개편했습니다.
|
|
2023년 3월 5일 |
다음 내용을 포함하도록 기사를 업데이트했습니다.
|
|
2022년 11월 15일 |
다음 IP 주소를 장치 구성 및 펌웨어 관리(Cisco 장치)에 추가했습니다.
다음 IP 주소를 장치 구성 및 펌웨어 관리(Cisco 장치)에서 제거했습니다.
|
|
2022년 11월 14일 |
IP 서브넷을 추가했습니다 170.72.242.0/24 Webex Calling 서비스용. |
|
2022년 9월 8일 |
Cisco MPP 펌웨어는 모든 지역의 MPP 펌웨어 업그레이드를 위한 호스트 URL로 https://binaries.webex.com 을 사용하도록 전환됩니다. 이 변경은 펌웨어 업그레이드 성능을 향상합니다. |
|
2022년 8월 30일 |
종속성이 없으므로 장치 구성 및 펌웨어 관리(Cisco 장치), 포트 테이블의 애플리케이션 구성 및 CScan 행에서 포트 80에 대한 참조를 제거했습니다. |
|
2022년 8월 18일 |
솔루션에 변경된 바는 없습니다. 통화 시그널링에 대해 대상 포트 5062(인증서 기반 트렁크에 필요), 8934(등록 기반 트렁크에 필요)를 Webex Calling 업데이트했습니다. |
|
2022년 7월 26일 |
54.68.1.225 IP 주소를 추가했습니다. 이는 Cisco 840/860 장치의 펌웨어 업그레이드에 대해 필요합니다. |
|
2022년 7월 21일 |
통화 시그널링에 대해 대상 포트 5062, 8934를 Webex Calling(SIP TLS)를 업데이트했습니다. |
|
2022년 7월 14일 |
Webex Aware 서비스의 전체 기능을 지원하는 URL을 추가했습니다. IP 서브넷을 추가했습니다 23.89.154.0/25 Webex Calling 서비스용. |
|
2022년 6월 27일 |
다음 서비스에 대한 도메인 및 Webex Calling 업데이트했습니다. *.broadcloudpbx.com *.broadcloud.com.au *.broadcloud.eu *.broadcloudpbx.net |
|
2022년 6월 15일 |
보안 서비스에 대한 IP 주소 및 포트 아래에 Webex Calling 프로토콜을 추가했습니다.
Webex에서 업데이트된 정보 Meetings/Messaging - 네트워크 요구 사항 섹션 |
|
2022년 5월 24일 |
내 서비스용 IP 서브넷 52.26.82.54/24에 52.26.82.54/32를 Webex Calling 추가했습니다. |
|
2022년 5월 6일 |
내 서비스용 IP 서브넷 52.26.82.54/24를 Webex Calling 추가했습니다. |
|
2022년 4월 7일 |
로컬 게이트웨이 내부 및 외부 UDP 포트 범위를 8000-48198로 업데이트했습니다.† |
|
2022년 4월 5일 |
Webex Calling 다음 IP 서브넷을 추가했습니다. 다음:
|
|
2022년 3월 29일 |
Webex Calling 다음 IP 서브넷을 추가했습니다. 다음:
|
|
2021년 09월 20일 |
Webex Calling 서비스에 대해 4 새로운 IP 서브넷을 추가함:
|
|
2021년 4월 2일 |
추가됨 *.ciscospark.com Webex 앱에서 Webex Calling 사용 사례를 지원하려면 Webex Calling 서비스의 도메인 및 URL 을 참조하세요. |
|
2021년 3월 25일 |
2021년 5월 8일부터 activate.cisco.com에 6개의 새로운 IP 범위가 추가되었습니다.
|
|
2021년 3월 4일 |
방화벽 구성을 쉽게 이해할 수 있도록 별도의 표에서 Webex Calling 개별 IP와 작은 IP 범위를 간소화된 범위로 대체했습니다. |
|
2021년 2월 26일 |
2021년 4월에 2021년 4월에 출시될 예정인 대화형 연결 지대(Webex Calling ICE)를 지원하기 위해 통화 미디어에 대해 5004를 Webex Calling(STUN, SRTP)에 대한 대상 포트로 추가했습니다. |
|
2021년 2월 22일 |
이제 도메인 및 URL은 개별 표에 나열됩니다. IP 주소 및 포트 테이블은 동일한 서비스에 대한 IP 주소를 그룹화하도록 조정됩니다. IP 주소 및 포트 표에 메모 열을 추가하면 요구 사항을 이해하는 데 도움이 됩니다. 다음 IP 주소를 장치 구성 및 펌웨어 관리를 위해 단순화된 범위로 이동합니다(Cisco 장치):
Cisco Webex 클라이언트가 2021년 3월 호주의 새로운 DNS SRV를 가리키므로 애플리케이션 구성을 위해 다음 IP 주소를 추가합니다.
|
|
2021년 1월 21일 |
다음 IP 주소를 장치 구성 및 펌웨어 관리(Cisco 장치)에 추가했습니다.
다음 IP 주소를 장치 구성 및 펌웨어 관리(Cisco 장치)에서 제거했습니다.
다음 IP 주소를 애플리케이션 구성에 추가했습니다.
다음 IP 주소를 애플리케이션 구성에서 제거했습니다.
다음 포트 번호를 애플리케이션 구성에서 제거했습니다.
다음 도메인을 애플리케이션 구성에 추가했습니다.
|
|
2020년 12월 23일 |
포트 참조 이미지에 새로운 응용프로그램 구성 IP 주소를 추가했습니다. |
|
2020년 12월 22일 |
다음 IP 주소를 포함하도록 표에서 응용프로그램 구성 행을 업데이트했습니다. 135.84.171.154 및 135.84.172.154. IP 주소가 추가될 때까지 네트워크 다이어그램을 숨깁니다. |
|
2020년 12월 11일 |
지원되는 캐나다 도메인에 대해 장치 구성 및 펌웨어 관리(Cisco 장치) 및 응용프로그램 구성 행을 업데이트했습니다. |
|
2020년 10월 16일 |
다음 IP 주소로 통화 시그널링 및 미디어 항목을 업데이트했습니다.
|
|
2020년 9월 23일 |
CScan 아래에서 199.59.64.156을 199.59.64.197로 바꿨습니다. |
|
2020년 8월 14일 |
캐나다에서 데이터 센터의 소개를 지원하기 위해 다른 IP 주소를 추가했습니다. Webex Calling에 대한 통화 시그널링 (SIP TLS)—135.84.173.0/25,135.84.174.0/25, 199.19.197.0/24, 199.19.199.0/24 |
|
2020년 8월 12일 |
캐나다에서 데이터 센터의 소개를 지원하기 위해 다른 IP 주소를 추가했습니다.
|
|
2020년 7월 22일 수요일 |
캐나다에서 데이터 센터의 소개를 지원하기 위해 다음 IP 주소를 추가했습니다. 135.84.173.146 |
|
2020년 6월 9일 |
CScan 항목에 다음 변경 사항을 적용했습니다.
|
|
2020년 3월 11일 |
다음 도메인과 IP 주소를 애플리케이션 구성에 추가했습니다.
추가 IP 주소를 포함하여 다음 도메인을 장치 구성 및 펌웨어 관리에 대해 업데이트했습니다.
|
|
2020년 2월 27일 목요일 |
다음 도메인 및 포트를 장치 구성 및 펌웨어 관리에 추가했습니다. cloudupgrader.webex.com—443, 6970 |


