- Home
- /
- Article


Dedicated Instance for Webex Calling - base configuration
 In this article
In this article Feedback?
Feedback?The base configuration of the Dedicated Instance of Webex Calling configuration in Control Hub includes the Unified Communication application.
Overview
This article provides high level configuration details about the Dedicated Instance for Webex Calling System Configuration (Dedicated Instance). It includes the following Unified Communications (UC) applications:
-
Cisco Unified Communication Manager (Unified CM)
-
Cisco Unified Instant Message and Presence (IM&P)
-
Cisco Unified Unity Connection (CUCxN) and
-
Cisco Emergency Responder (CER)
-
Edge components (Cisco Expressways)
Cisco Configured Components
Cisco configures multiple components in the customer’s Dedicated Instance UC applications. For these components to be easily identifiable, Cisco inserts an x in the beginning of the name of the component. This x prefix alerts partners to a Cisco-configured name that the partner or customer administrators should not modify or delete. This format is also used for Cisco’s operational monitoring/readiness of the Dedicated Instance UC applications.
The partner or customer should not modify or delete any of the following:
-
Region entries which are associated with resources in the Datacenter (DC), such as conference bridges, SIP trunks, etc.
-
Device pool entries which are associated with devices in the Cisco Datacenter.
-
Security configurations as required:
-
Credential policy configuration
-
SIP security profile configuration
-
-
Cisco-configured SIP trunks for various services integration, such as RedSky, Inter-op trunk to Webex Calling Multi-tenant, etc.
Cisco configures two CDR destinations in Unified CM to monitor the application and provide analytics in Control Hub for administrators.
Exceptions are when a Dedicated Instance document explicitly mentions changing a customer-specific configuration in the SIP trunks.
Control Hub – Webex Calling
|
Component |
Cisco Assigned Name |
Details |
|---|---|---|
|
Location Services → Calling → Location |
|
Location is mandatory for activation of Interop SIP trunk between Webex Calling and Dedicated Instance. A PSTN connection and a main number are required for successful call routing between MT and DI. The administrator must configure the main number for the default location. If this isn't configured, users can't make or receive calls through the Route Group associated with that location. If you're not using CCPP, the PSTN connection can be premise-based. For more information, see the Configure PSTN Connection section in How to Activate Dedicated Instance . |
|
SIP Trunk Services → Calling → Call Routing → Trunk |
|
SIP trunk one to each Dedicated Instance datacenter within a region is configured for basic interop between Webex Calling and Dedicated Instance. These are default trunks created by Cisco, should not be modified or deleted. |
|
Route Group Services → Calling → Call Routing → Route Group |
|
Route Groups are configured with the Interop SIP trunks and administrator can easily configure or link their custom Dial Plan to the default Route Group. |
Cisco Unified Communication Manager (Unified CM)
|
Component |
Cisco assigned name |
Details |
|---|---|---|
|
Unified CM Groups System → Cisco Unified CM Group |
|
A Unified Communications Manager Group is a prioritized list of up to three redundant servers to which devices can register. Each group contains a primary node and up to two backup nodes. |
|
Region System → Region Information → Region |
|
Regions provide capacity controls for Unified Communications Manager multisite deployments where you may need to limit the bandwidth for certain calls. |
|
Device Pool System → Device Pool |
|
Device pools provide a common set of configurations for a group of devices. You can assign a device pool to devices such as phones, gateways, trunks, and CTI route points. |
|
SIP Trunk Security Profile System → Security → SIP Trunk Security Profile
|
|
Security related settings for the SIP trunk to allow you to assign a single security profile to multiple SIP trunks. Security related settings include device security mode, digest authentication, and incoming/outgoing transport type settings. |
|
MRA Service Domain Advanced Features → MRA Service Domain |
MRA voice service domain <customer name>. <region>. wxc-di.webex.com. |
MRA Service Domains let you specify which Expressway your phones register. For example, customer.amer.wxc-di.webex.com, customer.emea.wxc-di.webex.com The SIP URI address value provided during the Dedicated Instance Service Activation is the domain used for all the UC applications and Mobile and Remote Access (MRA) service domain for each region(s). The Voice Service Domain per region is provided in the Dedicated Instance access document shared through the Webex App message at the time-of-service activation. |
|
SIP Trunk Device → Trunk |
SIP Trunks to:
|
The SIP Trunk Configuration window contains the SIP signaling configurations that Unified CM uses to manage SIP calls. The customer administrator must configure the SIP Normalization Script created. For more information, refer to Integrated Audio for Webex configuration. |
|
Route Group Call Routing → Route/Hunt → Route Group |
|
- |
|
Route List Call Routing → Route/Hunt → Route List |
|
- |
|
SIP Profile Device → Device Settings → SIP Profile |
|
SIP settings that you can assign to SIP devices and trunks that use this profile. |
|
Common Phone Profile Device → Device Settings → Common Phone Profile |
|
Common Phone Profiles allow you to configure Feature Control Policy settings and then apply those settings to all the phones in your network that use that profile. |
|
SIP Normalization Scripts Device → Device Settings → SIP Normalization Scripts |
|
Use the SIP Normalization script to add the X-DI-WxC-otg SIP Header for the Trunk towards Webex Calling. This value will be used for identifying the customer/cluster for call routing in the Webex Calling side. Customer or partner is expected to update the RedSky account ID. |
|
Application User User Management → Application Users |
|
The other application users are used by Cisco for operational and monitoring purpose. |
|
Credential Policy User Management → User Settings → Credential Policies |
|
Credential policies control the authentication process for resources in Unified CM. A credential policy defines password requirements and account lockout details such as failed login attempts, expiration periods and lockout durations for end-user passwords, end-user PINs, and application user passwords. Credential policies can be assigned broadly to all accounts of a specific credential type, such as all end-user PINs, or they can be customized for a specific application user, or end user. |
|
Roles User Management → preferences → Roles |
|
The other Role is created by Cisco, and can’t be edited or deleted by Partner or Customer administrators. |
|
Access Control Groups User Management → User Settings → Access Control Group |
See Rank 5 Access Control Group role assignment. | These Access Control Groups (AGC) are created by Cisco; Any combination of these ACGs can be used with partner or customer user with user rank 5 or below. |
|
UC Services User Management → User Settings → UC Services
|
|
Configure the user's service profile to point to the Unified CM services that you want to apply to this service profile. |
|
Service Profiles User Management → User Settings → Service Profiles → xSTD-Cluster-UCSP-Voice-Only |
|
Service Profile allows you to create a profile that comprises common Unified CM Services settings. The partner admin is required to get the HELD Customer ID and HELD+ Secure ID from his RedSky account and add them in the xSTD-Cluster-UCSP-Voice-Only of Service Profile section. |
|
User Rank User Management → User Settings → User Rank |
|
The User Rank hierarchy provides a set of controls over which access control groups an administrator and can assign to an end user or application user. |
|
Service Parameters - Cisco CallManager System → Service Parameters → Cisco CallManager |
|
- |
|
Service Parameters - Cisco IP Voice Media Streaming App System → Service Parameters → Cisco IP Voice Media Streaming App |
|
- |
|
Enterprise Parameters System → Enterprise Parameters |
|
Provides a unique identifier to the cluster. |
|
This is the protocol used by the auto-registration phone during initialization. |
|
|
- |
|
|
Cisco configures the Unified CM publisher node as default. |
|
|
- |
|
|
Indicates the security mode of the cluster and the algorithm to be used while generating the CTL, ITL, and TFTP configuration files. The Cluster security mode is set to Mixed Mode for the Unified CM Cluster. |
|
|
Initiates the expiry checking services for the different applications. |
|
|
|
|
|
- |
|
|
- |
Rank 5 Access Control Group role assignment
| Access Control Group Name | Rank | Role Assignment | Role privilege |
| Partner CCM Read Only | 5 | Same as Standard | See Role privilege table. |
| Customer CCM End Users | 5 | Standard CCM End Users | - |
| Partner CTI Allow Control of Phones supporting Connected Xfer and conf | See Role privilege table. | ||
| Partner CTI Allow Control of Phones supporting Rollover Mode | See Role privilege table. | ||
| Standard CTI Enabled | - | ||
| Partner Admin-3rd Party API | 5 | Same as Standard | See Role privilege table. |
| Partner Application Client Users | 5 | Same as Standard | See Role privilege table. |
| Partner CAR Admin Users | 5 | Same as Standard | See Role privilege table. |
| Partner CCM End Users | 5 | Standard CCM End Users | - |
| Standard CCMUSER Administration | - | ||
| Partner CCM Gateway Administration | 5 | Same as Standard | - |
| Partner CCM Phone Administration | 5 | Same as Standard | - |
| Partner CCM Server Maintenance | 5 | Same as Standard | - |
| Partner CCM Server Monitoring | 5 | Same as Standard | - |
| Partner Confidential Access Level Users | 5 | Same as Standard | - |
| Partner CTI Allow Call Monitoring | 5 | Same as Standard | - |
| Partner CCM Admin Users | 5 | Partner AXL API Access | See Role privilege table. |
| Partner CCMADMIN | See Role privilege table. | ||
| Partner IMPADMIN | See Role privilege table. | ||
| Partner RealtimeAndTraceCollection | See Role privilege table. | ||
| Standad AXL API Users | - | ||
| Standard Admin Rep Tool Admin | - | ||
| Standard CCM Admin Users | - | ||
| Standard CCM End Users | - | ||
| Standard CCMUSER Administration | - | ||
| Partner CTI Allow Control of Phones supporting Connected Xfer and conf | See Role privilege table. | ||
| Partner CTI Allow Control of Phones supporting Rollover Mode | See Role privilege table. | ||
| Standard CTI Enabled | - | ||
| Standard CUReporting | - | ||
| Partner CTI Allow Call Park Monitoring | 5 | Same as Standard | - |
| Partner Third Party Application Users | 5 | Same as Standard | - |
| Partner CTI Allow Call Recording | 5 | Same as Standard | - |
| Partner CTI Allow Calling Number Modification | 5 | Same as Standard | - |
| Partner CTI Allow Control of All Devices | 5 | Same as Standard | - |
| Partner CTI Allow Control of Phones supporting Connected Xfer and conf | 5 | Same as Standard | - |
| Partner CTI Allow Control of Phones supporting Rollover Mode | 5 | Same as Standard | - |
| Partner CTI Allow Reception of SRTP Key Material | 5 | Same as Standard | - |
| Partner CTI Enabled | 5 | Same as Standard | - |
| Partner CTI Secure Connection | 5 | Same as Standard | - |
| Partner EM Authentication Proxy Rights | 5 | Same as Standard | - |
| Partner EM Roaming Across Clusters Super Users | 5 | Same as Standard | - |
| Partner Packet Sniffer Users | 5 | Same as Standard | - |
| Partner RealtimeAndTraceCollection | 5 | Same as Standard | - |
| Partner TabSync User | 5 | Same as Standard | - |
Role privilege
| Role | Rank | Resource | Privilege |
| Partner CAR Admin Users | 5 | Copy of Standard CAR Admin Users | same as Rank 1 |
| Partner CCM Admin Users | 5 | Copy of Standard CCM Admin Users | same as Rank 1 |
| Partner CCM End Users | 5 | Copy of Standard CCM End Users | same as Rank 1 |
| Partner CCM Gateway Administration | 5 | Copy of Standard CCM Gateway Administration | same as Rank 1 |
| Partner CCM Phone Administration | 5 | Copy of Standard CCM Phone Administration | same as Rank 1 |
| Partner CCM Read Only | 5 | Copy of Standard CCM Read Only | same as Rank 1 |
| Partner CCM Server Maintenance | 5 | Copy of Standard CCM Server Maintenance | same as Rank 1 |
| Partner CCM Server Monitoring | 5 | Copy of Standard CCM Server Monitoring | same as Rank 1 |
| Partner Confidential Access Level Users | 5 | Copy of Standard Confidential Access Level Users | same as Rank 1 |
| Partner CTI Allow Call Monitoring | 5 | Copy of Standard CTI Allow Call Monitoring | same as Rank 1 |
| Partner CTI Allow Call Park Monitoring | 5 | Copy of Standard CTI Allow Call Park Monitoring | same as Rank 1 |
| Partner CTI Allow Call Recording | 5 | Copy of Standard CTI Allow Call Recording | same as Rank 1 |
| Partner CTI Allow Calling Number Modification | 5 | Copy of Standard CTI Allow Calling Number Modification | same as Rank 1 |
| Partner CTI Allow Control of All Devices | 5 | Copy of Standard CTI Allow Control of All Devices | same as Rank 1 |
| Partner CTI Allow Control of Phones supporting Connected Xfer and conf | 5 | Copy of Standard CTI Allow Control of Phones supporting Connected Xfer and conf | same as Rank 1 |
| Partner CTI Allow Control of Phones supporting Rollover Mode | 5 | Copy of Standard CTI Allow Control of Phones supporting Rollover Mode | same as Rank 1 |
| Partner CTI Allow Reception of SRTP Key Material | 5 | Copy of Standard CTI Allow Reception of SRTP Key Material | same as Rank 1 |
| Partner CTI Enabled | 5 | Copy of Standard CTI Enabled | same as Rank 1 |
| Partner CTI Secure Connection | 5 | Copy of Standard CTI Secure Connection | same as Rank 1 |
| Partner EM Authentication Proxy Rights | 5 | Copy of Standard EM Authentication Proxy Rights | same as Rank 1 |
| Partner EM Roaming Across Clusters Super Users | 5 | Copy of Standard EM Roaming Across Clusters Super Users | same as Rank 1 |
| Partner Packet Sniffer Users | 5 | Copy of Standard Packet Sniffer Users | same as Rank 1 |
| Partner TabSync User | 5 | Copy of Standard TabSync User | same as Rank 1 |
| Partner Admin-3rd Party API | 5 | Copy of Standard Admin-3rd Party API | same as Rank 1 |
| Partner Application Client Users | 5 | Copy of Standard Application Client Users | same as Rank 1 |
| Partner Third Party Application Users | 5 | Copy of Standard Third Party Application Users | same as Rank 1 |
| Partner CCMADMIN Role | 5 | AAR Group web pages | read, update |
| ALL License Device Usage Report | read, update | ||
| Access Control Group web pages | read, update | ||
| Access List | read, update | ||
| Add Unity User | read, update | ||
| Advanced License Device Usage Report | read, update | ||
| Advanced License User Usage Report | read, update | ||
| Advertised Route Pattern | read, update | ||
| All License User Usage Report | read, update | ||
| Announcement | read, update | ||
| Annunciator web pages | read, update | ||
| Application Dial Rules web pages | read, update | ||
| Application Server | read, update | ||
| Application User CAPF | read, update | ||
| Application User Web Pages | read, update | ||
| Audio Codec Preference List | read, update | ||
| BLF Directed Call Park | read, update | ||
| BLF Speeddial | read, update | ||
| Basic License Device Usage Report | read, update | ||
| Basic License User Usage Report | read, update | ||
| Blocked Learned Pattern | read, update | ||
| Blocked Learned Patterns | read, update | ||
| Blocked Patterns | read, update | ||
| Bulk Add/Update Lines | read, update | ||
| Bulk Add/Update Phones | read, update | ||
| Bulk CUPS User Page | read, update | ||
| Bulk Config Tool Export | read, update | ||
| Bulk Config Tool Import | read, update | ||
| Bulk Config Tool Import Validation | read, update | ||
| Bulk Delete Access List | read, update | ||
| Bulk Delete Call Pickup Group | read, update | ||
| Bulk Delete Client Matter Codes | read, update | ||
| Bulk Delete Fallback Profile | read, update | ||
| Bulk Delete Forced Authorization Codes | read, update | ||
| Bulk Delete Gateways | read, update | ||
| Bulk Delete IPMA Assistants | read, update | ||
| Bulk Delete IPMA Managers | read, update | ||
| Bulk Delete IPMA Managers/Assistants | read, update | ||
| Bulk Delete Mobility Profiles | read, update | ||
| Bulk Delete Phones | read, update | ||
| Bulk Delete Remote Destination | read, update | ||
| Bulk Delete Remote Destination Profile | read, update | ||
| Bulk Delete UDP | read, update | ||
| Bulk Delete Users | read, update | ||
| Bulk Delete Vipr Enrolled DID Pattern Group | read, update | ||
| Bulk Delete Vipr Exclusion Number Group | read, update | ||
| Bulk Delete Vipr Route Filter Element | read, update | ||
| Bulk Delete Vipr Route Filter Group | read, update | ||
| Bulk EMCC Delete | read, update | ||
| Bulk EMCC Insert/Update | read, update | ||
| Bulk EMCC Template | read, update | ||
| Bulk Export Access List | read, update | ||
| Bulk Export Line Appearance | read, update | ||
| Bulk Export Mobility Profiles | read, update | ||
| Bulk Export Phones | read, update | ||
| Bulk Export Remote Destination | read, update | ||
| Bulk Export Remote Destination Profile | read, update | ||
| Bulk Export UDP | read, update | ||
| Bulk Export Users | read, update | ||
| Bulk File Upload Pages | read, update | ||
| Bulk Gateway File Format | read, update | ||
| Bulk Gateway Template | read, update | ||
| Bulk Generate Gateway Reports | read, update | ||
| Bulk Generate IPMA Assistant Reports | read, update | ||
| Bulk Generate IPMA Manager Reports | read, update | ||
| Bulk Generate Phone Reports | read, update | ||
| Bulk Generate UDP Reports | read, update | ||
| Bulk Generate User Reports | read, update | ||
| Bulk Infrastructure Device Insert | insert, update | ||
| Bulk Insert Access List | read, update | ||
| Bulk Insert Call Pickup Group | read, update | ||
| Bulk Insert Client Matter Codes | read, update | ||
| Bulk Insert Fallback Profile | read, update | ||
| Bulk Insert Forced Authorization Codes | read, update | ||
| Bulk Insert Gateways | read, update | ||
| Bulk Insert IPMA Managers/Assistants | read, update | ||
| Bulk Insert Imported Directory URI | read, update | ||
| Bulk Insert Intercom | read, update | ||
| Bulk Insert Mobility Profiles | read, update | ||
| Bulk Insert Phones | read, update | ||
| Bulk Insert Phones with Users | read, update | ||
| Bulk Insert Remote Destination | read, update | ||
| Bulk Insert Remote Destination Profile | read, update | ||
| Bulk Insert UDP | read, update | ||
| Bulk Insert Users | read, update | ||
| Bulk Insert Vipr Enrolled DID Pattern Group | read, update | ||
| Bulk Insert Vipr Exclusion Number Group | read, update | ||
| Bulk Insert Vipr Route Filter Element | read, update | ||
| Bulk Insert Vipr Route Filter Group | read, update | ||
| Bulk Intercom DN Template | read, update | ||
| Bulk Job Scheduler pages | read, update | ||
| Bulk Migrate Phones | read, update | ||
| Bulk Phone & Users File Format | read, update | ||
| Bulk Phone File Format | read, update | ||
| Bulk Phone Migration | read, update | ||
| Bulk Phone Template | read, update | ||
| Bulk Region Matrix | read, update | ||
| Bulk Remote Destination Profile Add File Format | read, update | ||
| Bulk Remote Destination Profile Create File Format | read, update | ||
| Bulk Remote Destination Profile Template | read, update | ||
| Bulk Reset Password/PIN | read, update | ||
| Bulk Reset/Restart Phones | read, update | ||
| Bulk Secure TAPS | read, update | ||
| Bulk UDP File Format | read, update | ||
| Bulk UDP Intercom DN Add | read, update | ||
| Bulk UDP Intercom DN Update | read, update | ||
| Bulk UDP Template | read, update | ||
| Bulk Update Intercom | read, update | ||
| Bulk Update Line Appearance | read, update | ||
| Bulk Update Phones | read, update | ||
| Bulk Update UDP | read, update | ||
| Bulk Update Users | read, update | ||
| Bulk User CAPF Delete | read, update | ||
| Bulk User CAPF Export | read, update | ||
| Bulk User CAPF Insert | read, update | ||
| Bulk User Locales for TAPS | read, update | ||
| Bulk User Template | read, update | ||
| Bulk Validate Phones | read, update | ||
| Bulk Validate Phones/Users | read, update | ||
| Bulk Validate UDP | read, update | ||
| Bulk View TAPS Log File | read, update | ||
| Bulk Wipe/Lock Phones | read, update | ||
| CCD Advertising Service Profile | read, update | ||
| CCD Feature Configuration | read, update | ||
| CCD Requesting Service Profile | read, update | ||
| CMC Info | read, update | ||
| CTI Route Point web pages | read, update | ||
| CUMA Server Security Profile | read, update | ||
| Call Control Agent Profile | read, update | ||
| Call Control Discovery Partition | read, update | ||
| Call Park web pages | read, update | ||
| Call Pickup web pages | read, update | ||
| CallManager Group web pages | read, update | ||
| CallManager web pages | read, update | ||
| Called Party Tracing | read, update | ||
| Called Party Transformation Pattern | read, update | ||
| Calling Search Space web pages | read, update | ||
| Certificate web pages | read | ||
| Cloud Onboarding Page | read | ||
| Common Device Mobility Profile | read, update | ||
| Common Phone Profile | read, update | ||
| Conference Bridge web pages | read, update | ||
| Conference Now web pages | read, update | ||
| Confidential Access Level | read, update | ||
| Credential | read, update | ||
| Credential Policy | read, update | ||
| Credential Policy Default | read, update | ||
| Cross-Origin Resource Sharing | read, update | ||
| DHCP Server Web Pages | read, update | ||
| DHCP Subnet Web Pages | read, update | ||
| DRF Restore Warning Page | read | ||
| DRF Schedule Page | read | ||
| DRF Show Dependency Page | read | ||
| DRF Show Status Page | read | ||
| Date/Time Group web pages | read, update | ||
| Default Device Profile web pages | read, update | ||
| Delete Unassigned DN | read, update | ||
| Device Default web pages | read, update | ||
| Device Mobility Group | read, update | ||
| Device Mobility Info | read, update | ||
| Device Pool web pages | read, update | ||
| Device Profile web pages | read, update | ||
| Dial Plan | read, update | ||
| Dial Rule Pattern Info | read, update | ||
| Dial Rules Info | read, update | ||
| Directed Call Park | read, update | ||
| Directory Dial Rules pages | read, update | ||
| Directory Number web pages | read, update | ||
| Download Local Directory URI | read, update | ||
| E911 Messages | read, update | ||
| ELIN Group Web Pages | read, update | ||
| EMCC Feature Config | read, update | ||
| EMCC Intercluster Service Profile | read, update | ||
| EMCC Remote Cluster | read, update | ||
| EMCC Remote Cluster Service Override | read, update | ||
| Emergency Call Routing Regulations | read, update | ||
| Emergency Location Configuration Web Pages | read, update | ||
| Emergency Notification Page | read, update | ||
| End User CAPF | read, update | ||
| Enhanced License Device Usage Report | read, update | ||
| Enhanced License User Usage Report | read, update | ||
| Enterprise Parameters web pages | read, update | ||
| Enterprise Phone Configuration | read, update | ||
| Essential License Device Usage Report | read, update | ||
| Essential License User Usage Report | read, update | ||
| Export Local URIs | read, update | ||
| Expressway-C | - | ||
| External Call Control Profile | read, update | ||
| Fac Info | read, update | ||
| FallBack Feature Configuration Page | read, update | ||
| Fallback Profile Web Pages | read, update | ||
| Feature Control Policy | read, update | ||
| Feature Group Template web pages | read, update | ||
| Firmware Load web pages | read, update | ||
| Fixed MOH Audio Source | read, update | ||
| Gate Keeper web pages | read, update | ||
| Gateway Security Profile | read, update | ||
| Gateway web pages | read, update | ||
| Geolocation | read, update | ||
| Geolocation Filter | read, update | ||
| Geolocation Policy | read, update | ||
| H323 Security Profile | read, update | ||
| HTTP Profile | read, update | ||
| Handoff Mobility Setup | read, update | ||
| Headset Finesse Configuration | read, update | ||
| Headset and Accessories Inventory | read, update | ||
| Headset and Accessories Inventory Summary | read, update | ||
| Headset and Accessories Template | read, update | ||
| Hosted DN Group | read, update | ||
| Hosted DN Patterns | read, update | ||
| Hunt List | read, update | ||
| Hunt Pilot | read, update | ||
| ILS Cluster View page | read, update | ||
| ILS web pages | read, update | ||
| IME Enrolled Group Web Pages | read, update | ||
| IME Enrolled Pattern Web Pages | read, update | ||
| IME Exclusion Group Web Pages | read, update | ||
| IME Exclusion Number Web Pages | read, update | ||
| IME Feature Configuration Page | read, update | ||
| IME Firewall Web Pages | read, update | ||
| IME Learned Route Web Pages | read, update | ||
| IME Server Web Pages | read, update | ||
| IME Service Web Pages | read, update | ||
| IME Transformation Web Pages | read, update | ||
| IME Trusted Element Web Pages | read, update | ||
| IME Trusted Group Web Pages | read, update | ||
| IME UCM External Address List Web Page | read, update | ||
| IPMA Wizard web pages | read, update | ||
| IVR Source web pages | read, update | ||
| Imported Directory URI | read, update | ||
| Imported Directory URI Catalog | read, update | ||
| Imported Pattern | read, update | ||
| Intercluster Directory URI Configuration | read, update | ||
| IntercomCallingSearchSpace | read, update | ||
| IntercomDirectoryNumber | read, update | ||
| IntercomRoutePartition | read, update | ||
| IntercomTranslation | read, update | ||
| LDAP Authentication Configuration Page | read, update | ||
| LDAP Custom Filter Configuration | read, update | ||
| LDAP Directory Configuration Pages | read, update | ||
| LDAP Search Configuration Page | read, update | ||
| LDAP System Configuration Page | read, update | ||
| Ldap Sync UserGroup | read, update | ||
| Learned Alternate Numbers | read, update | ||
| Learned Directory URIs | read, update | ||
| Learned Object | read, update | ||
| Learned Patterns | read, update | ||
| License Device Usage Report | read, update | ||
| License User Usage Report | read, update | ||
| License User View Details | read, update | ||
| Licensing | read | ||
| Licensing Report | read | ||
| Line Appearance web pages | read, update | ||
| Line Group web pages | read, update | ||
| Line Template Page | read, update | ||
| Local Route Group | read, update | ||
| Location Bandwidth Manager Group | read, update | ||
| Location Bandwidth Manager(LBM) Intercluster Replication Group | read, update | ||
| Location web pages | read, update | ||
| MLPP Domain web pages | read, update | ||
| MOH Audio Source Management web pages | read, update | ||
| MOH Audio Source web pages | read, update | ||
| MOH Server web pages | read, update | ||
| MRA Service Domain | read, update | ||
| Media Resource Group List web pages | read, update | ||
| Media Resource Group web pages | read, update | ||
| Media Termination Point web pages | read, update | ||
| Meet Me web pages | read, update | ||
| Message Waiting web pages | read, update | ||
| Mobile Voice Access | read, update | ||
| Mobility Configuration | read, update | ||
| Mobility Enterprise Feature Access | read, update | ||
| Mobility Profile | read, update | ||
| NTP Server | read, update | ||
| Network Access Profile | read, update | ||
| Page Layout Preference web pages | read, update | ||
| Panic Button Popup Page | read, update | ||
| Pattern Parameter Info | read, update | ||
| Phone Activation Code Page | read | ||
| Phone Add Page | read, update | ||
| Phone Button Layout web pages | read, update | ||
| Phone Button Template web pages | read, update | ||
| Phone Device Profile Page | read, update | ||
| Phone Migration | read, update | ||
| Phone Security Profile | read, update | ||
| Phone Service Subscribe Page | read, update | ||
| Phone Services web pages | read, update | ||
| Phone web pages | read, update | ||
| Physical Location | read, update | ||
| Plugin web pages | read, update | ||
| Premium License Device Usage Report | read, update | ||
| Premium License User Usage Report | read, update | ||
| Presence Group | read,, update | ||
| Presence License User Usage Report | read, update | ||
| Presence Redundancy Group | read, update | ||
| Presence Server Status | read, update | ||
| Presence User Assignment | read, update | ||
| Professional License User Usage Report | read, update | ||
| Recording Profile | read, update | ||
| Region web pages | read, update | ||
| RemoteDestination | read, update | ||
| RemoteDestinationTemplate | read, update | ||
| Reorder Info | read, update | ||
| Resource Priority Namespace | read, update | ||
| Resource Priority Namespace List | read, update | ||
| Role web pages | read | ||
| Route Filter web pages | read, update | ||
| Route Group web pages | read, update | ||
| Route List | read, update | ||
| Route Partition web pages | read, update | ||
| Route Partitions For Learned Patterns | read, update | ||
| Route Pattern Popup Page | read, update | ||
| Route Pattern web pages | read, update | ||
| Route Pattern2 | read, update | ||
| Route Plan Report web pages | read, update | ||
| SAF Forwarder | read, update | ||
| SAF Security Profile | read, update | ||
| SAML Single Sign-On | read, update | ||
| SCCP Security Profile | read, update | ||
| SDP Transparency Profile | read, update | ||
| SIP Normalization Script | read, update | ||
| SIP Phone Security Profile | read, update | ||
| SIP Profile | read, update | ||
| SIP Realm | read, update | ||
| SIP Route Pattern | read, update | ||
| SIP Trunk Security Profile | read, update | ||
| SRST Certificate | read, update | ||
| SRST web pages | read, update | ||
| SSO Wizard web pages | read, update | ||
| Security Setting web pages | read, update | ||
| Self Provisioning Configuration | read, update | ||
| Server web pages | read, update | ||
| Service Parameter web pages | read, update | ||
| Service Profile web pages | read, update | ||
| Service Url Page | read, update | ||
| Softkey Template web pages | read, update | ||
| Speed Dial Page | read, update | ||
| Super Copy Info | read, update | ||
| Switches and Access Point Web Pages | read, update | ||
| Telepresence License Device Usage Report | read, update | ||
| Telepresence License User Usage Report | read, update | ||
| Time Period | read, update | ||
| Time Schedule | read, update | ||
| Transcoder web pages | read, update | ||
| Transformation Pattern | read, update | ||
| Transformation Profile Web Pages | read, update | ||
| Translation Pattern web pages | read, update | ||
| Trunk web pages | read, update | ||
| UC Service web pages | read, update | ||
| Universal Device Template web pages | read, update | ||
| Universal Line Template web pages | read, update | ||
| User Profile | read, update | ||
| User Rank web pages | read, update | ||
| User web pages | read, update | ||
| VOH Server web pages | read, update | ||
| VPN Feature Config | read, update | ||
| VPN Gateway web pages | read, update | ||
| VPN Group web pages | read, update | ||
| VPN Profile | read, update | ||
| Voice Mail Pilot web pages | read, update | ||
| Voice Mail Port Wizard web pages | read, update | ||
| Voice Mail Port web pages | read, update | ||
| Voice Mail Profile web pages | read, update | ||
| Voice Mail web pages | read, update | ||
| Wi-Fi Hotspot Profile | read, update | ||
| Wireless Access Point Controller Web Pages | read, update | ||
| Wireless LAN Profile | read, update | ||
| Wireless LAN Profile Group | read, update | ||
| Partner RealtimeAndTraceCollection | 5 | Alarm Configuration web page | read |
| Alarm Definition web page | read | ||
| Audit Configuration | read | ||
| Audit Trace | read | ||
| CDR Management | read | ||
| Call Home Configuration web page | read | ||
| Called Party Tracing | read, update | ||
| Control Center - Feature Services web page | read, update | ||
| Control Center - Network Services web page | read, update | ||
| Locations Assertions Detail web page | read, update | ||
| Locations Disconnected Groups web page | read, update | ||
| Locations Discrepancy web page | read, update | ||
| Locations Effective Path web page | read, update | ||
| Locations Topology web page | read, update | ||
| Log Partition Monitoring->Configuration web page | read, update | ||
| RTMT->Alert Config | read, update | ||
| RTMT->Profile Saving | read, update | ||
| Real Time Monitoring Tool | read, update | ||
| SNMP->V1/V2c->Configuration->Community String web page | - | ||
| SNMP->V1/V2c->Configuration->Notification Destination web page | - | ||
| SNMP->V3 Configuration->Notification Destination web page | - | ||
| SNMP->V3 Configuration->User web page | - | ||
| SNMP->system Group Configuration->MIB2 System Group Configuration web page | - | ||
| SOAP Backup and Restore APIs | - | ||
| SOAP CDR on Demand APIs | - | ||
| SOAP CDR on Demand APIs 2 | - | ||
| SOAP Call Record APIs | - | ||
| SOAP Control Center APIs | - | ||
| SOAP Control Center APIs 2 | - | ||
| SOAP Diagnostic Portal Database Service | - | ||
| SOAP Log Collection APIs | - | ||
| SOAP Log Collection APIs 2 | - | ||
| SOAP Performance Informations APIs | - | ||
| SOAP Performance Informations APIs 2 | - | ||
| SOAP Realtime Informations and Control Center APIs | - | ||
| SOAP Realtime Informations and Control Center APIs 2 | - | ||
| SOAP SNMP Config API | - | ||
| SOAP Troubleshooter API | - | ||
| Service Activation web page | read, update | ||
| Serviceability Report Archive | read, update | ||
| Trace Collection Tool | read, update | ||
| Trace Configuration web page | read, update | ||
| Troubleshoot Trace Settings web page | read, update | ||
| Partner AXL API Access | 5 | Add Api | Allow to use API |
| Execute SQL Query | Allow to use API | ||
| Execute SQL Update | Allow to use API | ||
| Get Api | Allow to use API | ||
| List Api | Allow to use API | ||
| Remove Api | Allow to use API | ||
| Update Api | Allow to use API | ||
| Partner IMPADMIN | 5 | read update | - |
| Advanced Presence Settings | read, update | ||
| Applications Listeners | read, update | ||
| Bulk Contact List Export | read, update | ||
| Bulk Contact List Update | read, update | ||
| Bulk Contacts Rename | read, update | ||
| Bulk File Upload Pages | read, update | ||
| Bulk Job Scheduler pages | read, update | ||
| Bulk Legacy Clients/Microsoft RCC | read, update | ||
| CCMCIP Profile | read, update | ||
| Centralized Deployment | - | ||
| Certificate Import Tool | read, update | ||
| Client Types | read, update | ||
| Compliance | read, update | ||
| Compliance Change Password | - | ||
| Compliance Disable Encryption | - | ||
| Compliance Download Encryption | - | ||
| Compliance Profile | read, update | ||
| Compliance Profile Routing Priority | read, update | ||
| Dashboard | read, update | ||
| Email Federated Domains | read, update | ||
| Enterprise Parameters web pages | read, update | ||
| Exchange Certificate Config | read, update | ||
| Exchange Certificate Detail | read, update | ||
| Export Non-presence Contact List | read, update | ||
| Export User Location Details | - | ||
| External Database Jobs | read, update | ||
| External Database Settings | read, update | ||
| External File Server | read, update | ||
| Federated Domains | read, update | ||
| File Transfer | read, update | ||
| General Certificate Config | read, update | ||
| Global Security Settings | read, update | ||
| Group Chat Rooms Relocation | - | ||
| Group Chat Server Alias and Room | - | ||
| Group Chat and Persistent Chat Settings | read, update | ||
| Import Non-presence Contact List | read, update | ||
| Import User Location Details | - | ||
| Incoming SIP Proxy ACL | read, update | ||
| Inter-Clustering | read, update | ||
| Intradomian Federation Setup | read, update | ||
| LDAP Hosts for Third Party Client Contact Search | read, update | ||
| LDAP Settings for Third Party Client Contact Search | read, update | ||
| Legacy Client Settings | read, update | ||
| MOC Troubleshooter | read, update | ||
| Messaging Settings | read, update | ||
| Method/Event Routing | read, update | ||
| Microsoft RCC Settings | read, update | ||
| Microsoft RCC User Assignment | read, update | ||
| Notifications | read, update | ||
| Number Expansion | read, update | ||
| Outgoing SIP Proxy ACL | read, update | ||
| Plugin web pages | read, update | ||
| Presence Domains | read, update | ||
| Presence Gateways | read, update | ||
| Presence Routing Settings | read, update | ||
| Presence Search | read, update | ||
| Presence Settings | read, update | ||
| Service Parameter web pages | read, update | ||
| Static Routes | read, update | ||
| TC Sysadmins | read, update | ||
| TLS Context | read, update | ||
| TLS Peer Subjects | read, update | ||
| Text Chat Node Alias | read, update | ||
| Third Party Compliance Server | read, update | ||
| Topology | read, update | ||
| Troubleshooter | read, update | ||
| Whats New | read, update | ||
| XMPP Federation Policy | read, update | ||
| XMPP Federation Settings | read, update |
Cisco Unified Unity Connection (CUCxN)
|
Component |
Cisco Assigned Name |
Details |
|---|---|---|
|
Partition Dialplan → Partition |
<customer id><dc id>ccnXXX Partition |
Tenant partitioning also introduces the concept of using the corporate email addresses as their alias, which enables alias uniqueness across tenants. |
|
Search Space Dialplan → Search Space |
<customer id><dc id>ccnXXX Search Space |
Search spaces are assigned to objects such as user primary extensions, routing rules, call handlers, or VPIM locations. |
|
Authentication Rules System Settings |
UCM For Cloud Credential Policy - Voice Mail Application UCM For Cloud Credential Policy - Web Application |
Authentication rules govern user passwords, PINs, and account lockouts for all user accounts. |
|
Roles System Settings → Roles → Custom Roles |
Partner CUC Admin |
Custom roles are the roles that you create with a list of privileges based on your organizational requirements. Custom roles can be assigned or unassigned to users by System Administrator or a custom role user with role assignment privilege. |
|
Port Group Telephony Integrations → Port Group |
|
Port Groups are assigned voice messaging ports that define Unity Connection integration configuration settings. |
|
Port Telephony Integrations → Port |
|
|
|
Enterprise Parameters System Settings → Enterprise Parameters |
|
Enterprise parameters for Cisco Unity Connection provide default settings that apply to all services in Cisco Unified Serviceability. |
|
Users Users → Users |
Partneradmin |
The other application users are used by Cisco for operational and monitoring purpose. |
Cisco Emergency Responder (CER)
|
Component |
Cisco Assigned Name |
Details |
|---|---|---|
|
SysLog Server System → Cisco ER Group Settings |
Syslog Server |
|
|
SNMPv3 Settings Phone Tracking → SNMPv3 Settings |
SNMP user details will be added for all the CUCM nodes. |
|
|
Cisco Unified Communications Manager Cluster |
CUCM Publisher details will be added. |
|
|
Users User Management → Users |
Partneradmin |
The other application users are used by Cisco for operational and monitoring purpose. |
|
Roles User Management → Roles |
Partner CUC Admin |
|
|
User Groups User Management → User Groups |
Partner → Admin Group |
|
|
Red Sky Configuration System → Intrado VUI Settings |
|
As part of the RedSky configuration:
The partner administrator is required to get the CER Account ID from their RedSky portal and add the details in Intrado Account ID field. |
Edge Components (Cisco Expressways)
|
Component |
Cisco Assigned Name |
|---|---|
|
IP System → Network Interfaces → IP |
LAN 1 IP address |
|
DNS System → DNS |
DNS server IP address (should not be modified) |
|
Time System → Time |
NTP servers IP address (should not be modified) |
|
Clustering System → Clustering |
Cisco UCM details address (should not be modified) |
Call Policy Rule
To enhance the security of the base Dedicated Instance platform, and to promote good security practice, Dedicated Instance Expressway E’s are preconfigured with a Call Policy to block all inbound B2B calls.
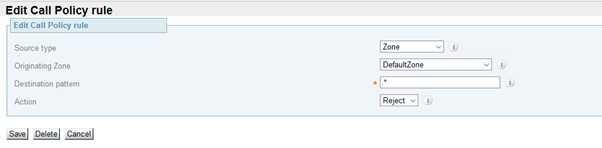
During configuration and testing of B2B services, this call policy should be updated in line with the customers requirement. This ensures that the B2B calls are destined for the correct destinations and/or come from valid sources.
Refer to About Call Policy for more information.
The Dedicated Instance UC application access details along with the credentials are shared only through the Webex App message to the partner or customer email ID provided in the Cisco Webex Order for a Customer wizard. By default, the access document is shared only to the partner's email ID through Webex App. If the partner's email ID is not available then the customer's email ID is used for the Webex App message notification.
See, Webex App | Sign In for the First Time for more information.


