What does end-to-end encryption with identity verification do?
 Feedback?
Feedback?Meeting participants can create a common meeting encryption key, which is only accessible to the participants in the meeting. The Webex service can't access the meeting key. For more information, see End-to-end encryption with identity verification for Webex meetings.
Media streams flowing from a client to Webex servers are decrypted after they cross the Webex firewall. Cisco can then provide network-based recordings that include all media streams for future reference. Webex then re-encrypts the media stream before sending it to other clients. However, for businesses requiring a higher level of security, Webex also provides end-to-end encryption. With this option, the Webex cloud does not decrypt the media streams, as it does for normal communications. Instead it establishes a Transport Layer Security (TLS) channel for client-server communication. Additionally, all Webex clients generate key pairs and send the public key to the host’s client.
The host generates a symmetric key using a Cryptographically Secure Pseudo-Random Number Generator (CSPRNG), encrypts it using the public key that the client sends, and sends the encrypted symmetric key back to the client. The traffic generated by clients is encrypted using the symmetric key. In this model, traffic cannot be decoded by the Webex server. This end-to-end encryption option is available for Webex Meetings and Webex Support.
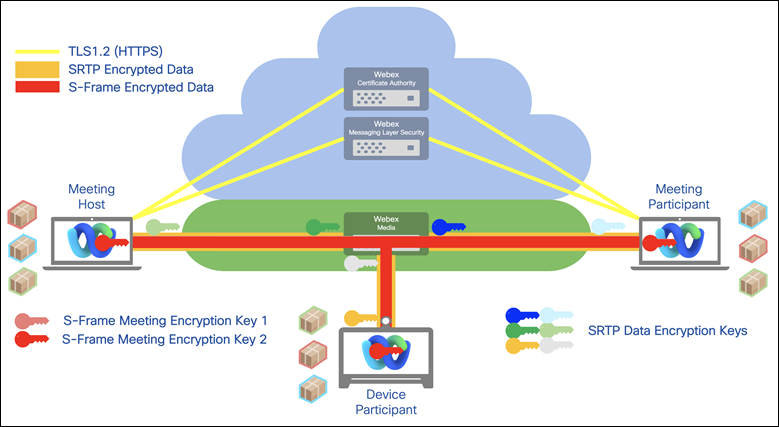
For more information on E2EE and Cisco Secure Real-Time Collaboration, see the Security White Paper.


